Overview
When you create a codespace, a development container is automatically created on a remote virtual machine. This dev container is created from a Docker image. The image is effectively a template for Docker containers and it determines many aspects of the resulting environment provided by the codespace. For more information, see GitHub Codespaces overview.
You can choose which image you want to use for your codespaces by specifying it in the dev container configuration for a repository. You can do this, for example, by using the image property in the devcontainer.json file.
"image": "mcr.microsoft.com/devcontainers/javascript-node:18",
"image": "mcr.microsoft.com/devcontainers/javascript-node:18",
For more information, see the dev containers specification on the Development Containers website.
Alternatively, you can specify the base image in a Dockerfile. For more information, see Introduction to dev containers.
If you don't specify an image in the dev container configuration for a repository, the default dev container image is used. The default image contains a number of runtime versions for popular languages and commonly used tools. For more information, see Introduction to dev containers.
As an organization owner, you can add a policy to restrict which dev container images can be used for codespaces created within your organization.
If you attempt to create a codespace using a devcontainer.json that specifies an image that is not allowed by the policy, the following message is displayed in GitHub:
The codespace cannot be created because the image specified in your dev container configuration is not allowed. You may need to select a different branch, modify your container configuration, or adjust your organization's policy setting.
Using the CLI, the error message is:
error creating codespace: HTTP 400: Base image 'IMAGE-REFERENCE' is not allowed based on an organization policy set by your organization administrator.
If the image for a codespace is specified in a Dockerfile, and does not match the policy, a codespace is created in recovery mode, using the default recovery container rather than the specified image. A message to this effect is included at the end of the creation log. For more information about the creation log, see GitHub Codespaces logs.
Note
- The dev container base image should not be confused with the host image. The host image is the image used to build the virtual machine on which the dev container runs. For more information, see Choosing the stable or beta host image.
- The base image policy is applied when a codespace is created, and when you perform a full container rebuild. For more information, see Understanding the codespace lifecycle.
- The base image policy does not apply to the default image, or the image that's used to recover a codespace if an error is introduced into a dev container configuration which prevents the container from being rebuilt.
Setting organization-wide and repository-specific policies
When you create a policy you choose whether it applies to all repositories in your organization, or only to specified repositories. If you set an organization-wide policy then any policies you set for individual repositories must fall within the restriction set at the organization level. Adding policies makes the choice of image more, not less, restrictive.
For example, you could create an organization-wide policy that restricts the base image to any of ten specified images. You can then set a policy for Repository A that restricts the image to a subset of just two of the images specified at the organization level. Specifying additional images for Repository A will have no effect because these images are not specified in the organization-level policy. If you add an organization-wide policy, you should set it to the largest choice of images that will be available for any repository in your organization. You can then add repository-specific policies to further restrict the choice.
Note
Codespaces policies only apply to codespaces that your organizations pays for. If someone creates a codespace for a repository in your organization at their own expense, then the codespace will not be bound by these policies. For more information, see Choosing who owns and pays for codespaces in your organization.
Adding a policy to define the allowed images
-
In the upper-right corner of GitHub, select your profile photo, then click Your organizations.
-
Next to the organization, click Settings.
-
In the "Code, planning, and automation" section of the sidebar, select Codespaces then click Policies.
-
On the "Codespaces policies" page, click Create Policy.
-
Enter a name for your new policy.
-
Click Add constraint and choose Base images.
-
Click to edit the constraint.
-
In the "Allowed values" field, enter the image reference of the Docker image you want to allow.
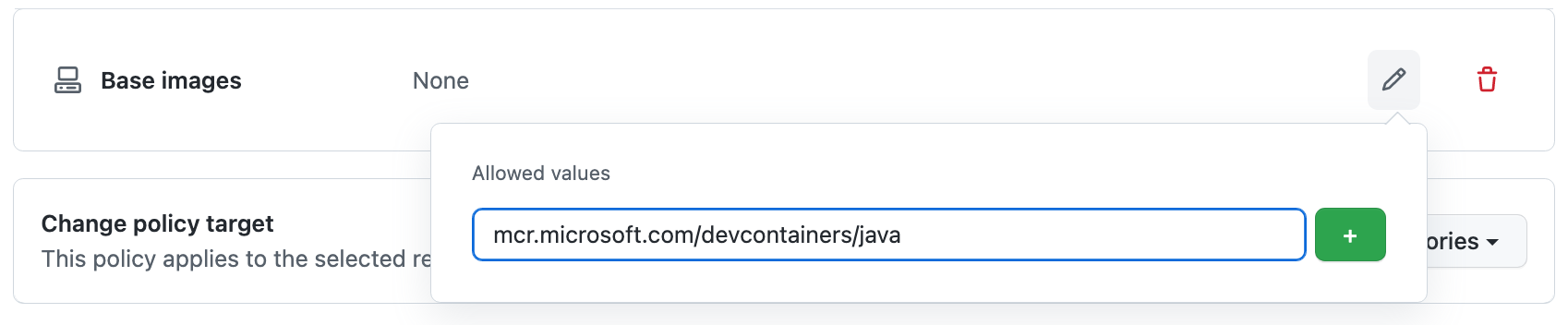
You can use the
*wildcard as the last character of the image reference to match all images that start with the same reference to the left of the wildcard. For example,mcr.microsoft.com/devcontainers/*. -
Click to add the value.
-
If required, repeat the previous two steps to add more image references.
When you add multiple image references, if an image reference specified in the dev container configuration of a repository does not match any of the references in a policy that applies to the repository, you will not be able to create codespaces for that repository.
-
Click outside of the dialog box to close it.
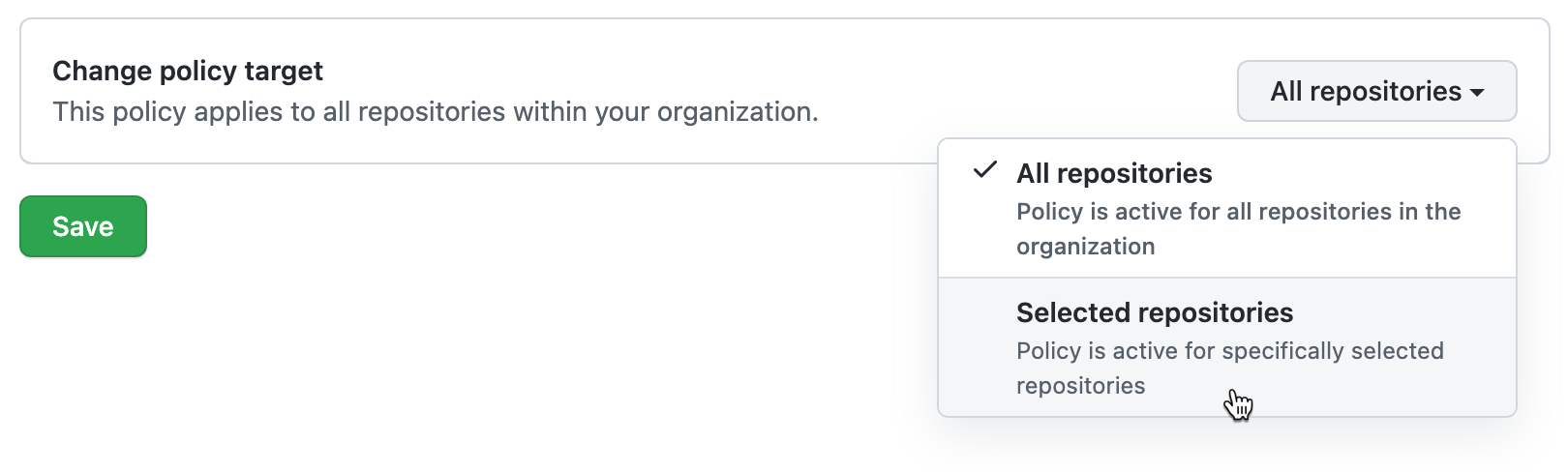
-
By default the policy is set to apply to all repositories, if you want it to apply only to some of the repositories in your organization, click All repositories and then click Selected repositories in the dropdown menu.
Note
If you're adding a constraint to an existing policy that already contains the "Maximum codespaces per user" constraint, you won't be able to apply the policy to selected repositories. This is because the "Maximum codespaces per user" constraint always applies to all repositories in the organization.
With Selected repositories selected:
-
Click .
-
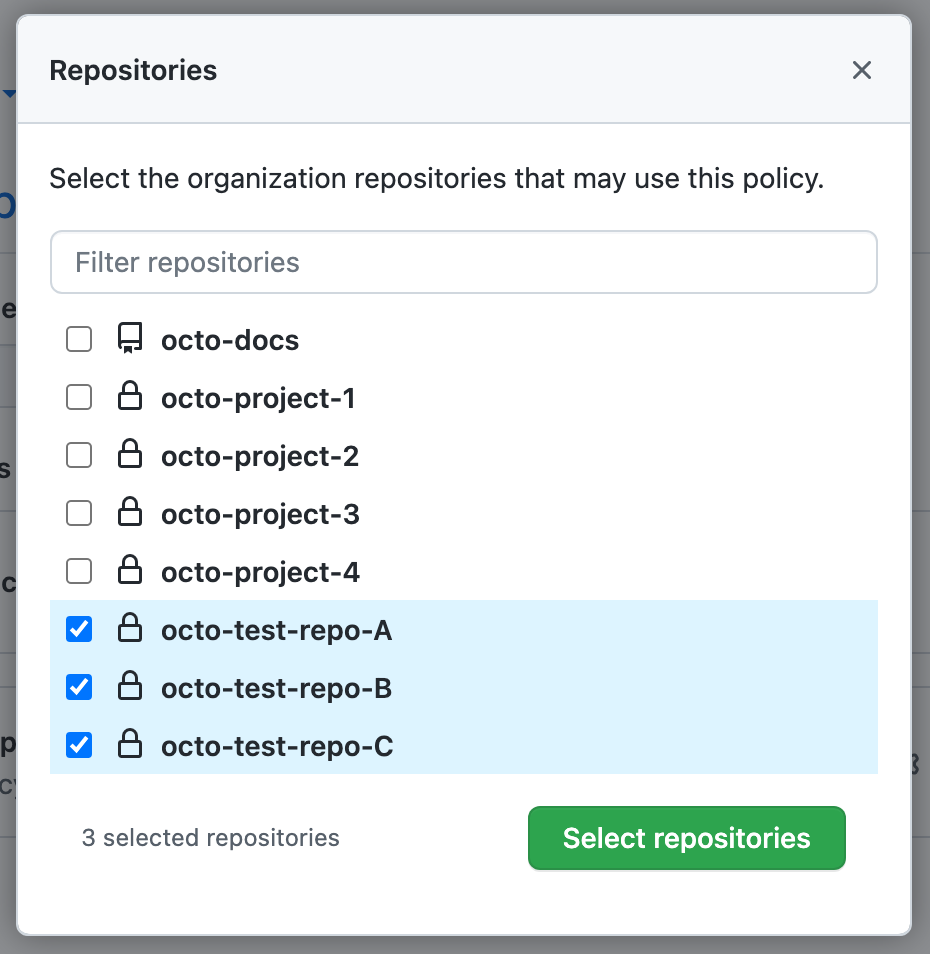
Select the repositories you want this policy to apply to.
-
At the bottom of the repository list, click Select repositories.
-
-
If you want to add another constraint to the policy, click Add constraint and choose another constraint. For information about other constraints, see:
-
After you've finished adding constraints to your policy, click Save.
The policy is applied when anyone attempts to create a new codespace that is billable to your organization. The base image constraint does not affect existing codespaces, either active or stopped.
Editing a policy
You can edit an existing policy. For example, you may want to add or remove constraints to or from a policy.
- Display the "Codespaces policies" page. For more information, see Adding a policy to define the allowed images.
- Click the name of the policy you want to edit.
- Beside the "Base images" constraint, click .
- Add or remove image references.
- Click Save.
Deleting a policy
-
Display the "Codespaces policies" page. For more information, see Adding a policy to define the allowed images.
-
Click to the right of the policy you want to delete.