About built-in authentication for users outside your identity provider
You can use built-in authentication for outside users when you are unable to add specific accounts to your identity provider (IdP), such as accounts for contractors or machine users. You can also use built-in authentication to access a fallback account if the identity provider is unavailable.
After built-in authentication is configured and a user successfully authenticates with SAML or CAS, they will no longer have the option to authenticate with a username and password. If a user successfully authenticates with LDAP, the credentials are no longer considered internal.
Built-in authentication for a specific IdP is disabled by default.
Warning: If you disable built-in authentication, you must individually suspend any users that should no longer have access to the instance. For more information, see "Suspending and unsuspending users."
Configuring built-in authentication for users outside your identity provider
- From an administrative account on GitHub Enterprise Server, click in the upper-right corner of any page.
- In the left sidebar, click Management Console.
- In the left sidebar, click Authentication.
- Select your identity provider.
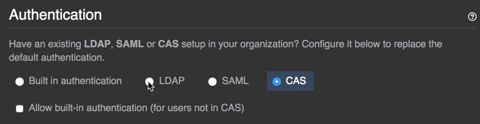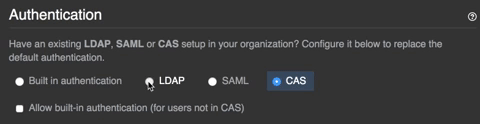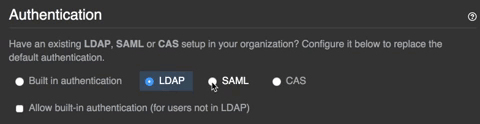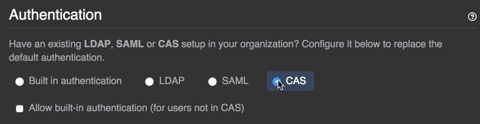
- Select Allow creation of accounts with built-in authentication.
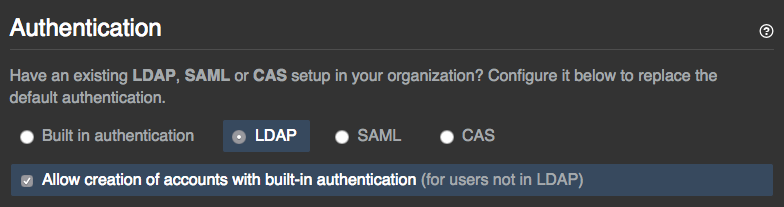
- Read the warning, then click Ok.
Two-factor authentication
When using LDAP or built-in authentication, two-factor authentication is supported. Organization administrators can require members to have two-factor authentication enabled.
Inviting users outside your identity provider to authenticate to your instance
When a user accepts the invitation, they can use their username and password to sign in rather than signing in through the IdP.
- Sign in to your GitHub Enterprise Server instance at
http(s)://HOSTNAME/login. - From an administrative account on GitHub Enterprise Server, click in the upper-right corner of any page.

- In the left sidebar, click Invite user.
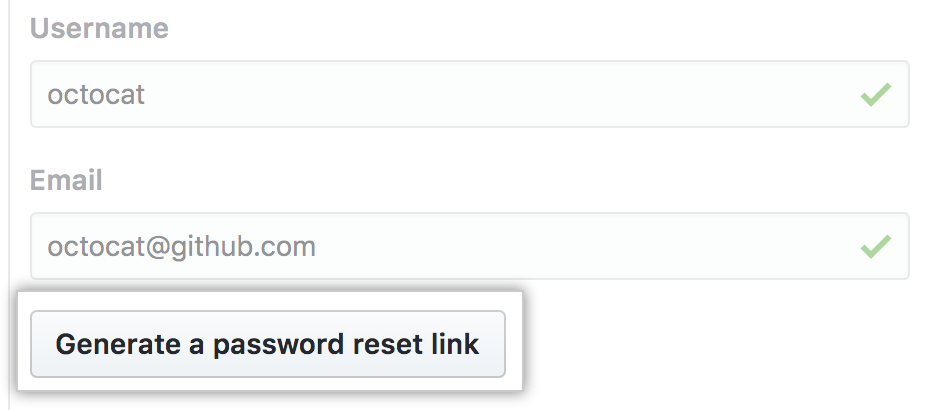
- Type the username and email address for each of the user accounts that you'd like to create, then click Generate a password reset link.
Further reading
- "Using LDAP"
- "Using SAML"
- "Using CAS"