Generieren eines regulären Ausdrucks für ein Repository mit Copilot Geheimnisüberprüfung
Note
Sie benötigen kein Abonnement für GitHub Copilot, um den Generator für reguläre Ausdrücke von GitHub Copilot nutzen zu können. Copilot Geheimnisüberprüfung-Features sind in privaten Repositorys in Organisationen und Unternehmen verfügbar, die GitHub Advanced Security aktiviert haben.
-
Navigieren Sie auf GitHub zur Hauptseite des Repositorys.
-
Wähle unter dem Namen deines Repositorys die Option Einstellungen aus. Wenn die Registerkarte „Einstellungen“ nicht angezeigt wird, wähle im Dropdownmenü die Option Einstellungen aus.

-
Klicke im Abschnitt „Security“ der Randleiste auf Code security.
-
Suche unter „Code security“ nach „GitHub Advanced Security“.
-
Klicke unter Secret scanning unter „Benutzerdefinierte Muster“ auf Neues Muster.
-
Geben Sie im Feld „Mustername“ einen Namen für Ihr Muster ein.
-
Klicken Sie oben rechts auf Mit KI generieren.
Note
Du kannst einen regulären Ausdruck manuell eingeben, anstatt den Generator zu verwenden, indem du einen regulären Ausdruck für das Format deines geheimen Musters im Feld „Secret format“ eingibst. Weitere Informationen findest du unter Definieren eines benutzerdefinierten Musters für ein Repository oder Definieren eines benutzerdefinierten Musters für eine Organisation.
-
Im Schiebebereich, der angezeigt wird:
-
Füllen Sie das Feld „Ich möchte einen regulären Ausdruck“ aus, der im Idealfall in einfachem Englisch beschreibt, welche Muster der reguläre Ausdruck erfassen soll. Sie können andere natürliche Sprachen verwenden, aber die Leistung ist möglicherweise nicht so gut wie bei Englisch.
-
Füllen Sie das Feld „Beispiele für das Gesuchte“ aus, und geben Sie ein Beispiel für ein Muster, nach dem Sie suchen möchten.
-
Klicken Sie auf Vorschläge generieren.
-
Klicken Sie optional auf einen Vorschlag, um eine Beschreibung des regulären Ausdrucks anzuzeigen.
-
Klicken Sie auf Ergebnisse verwenden, das angezeigt wird, für das Ergebnis, das Sie verwenden möchten.

-
-
Du kannst auf More options klicken, um andere umgebende Inhalte oder zusätzliche Übereinstimmungsanforderungen für das geheime Format bereitzustellen. GitHub fügt die Beispiele hinzu, die Sie im Schiebebereich eingegeben haben, zum Feld Zeichenfolge testen.
-
Wenn Sie bereit sind, Ihr neues benutzerdefiniertes Muster zu testen, um Übereinstimmungen im Repository zu identifizieren, ohne Warnungen zu erstellen, klicken Sie auf Save and dry run (Speichern und Probelauf).
-
Wenn der Probelauf abgeschlossen ist, wird eine Auswahl der Ergebnisse (bis zu 1000) angezeigt. Überprüfe die Ergebnisse, und identifiziere alle falsch positiven Ergebnisse.
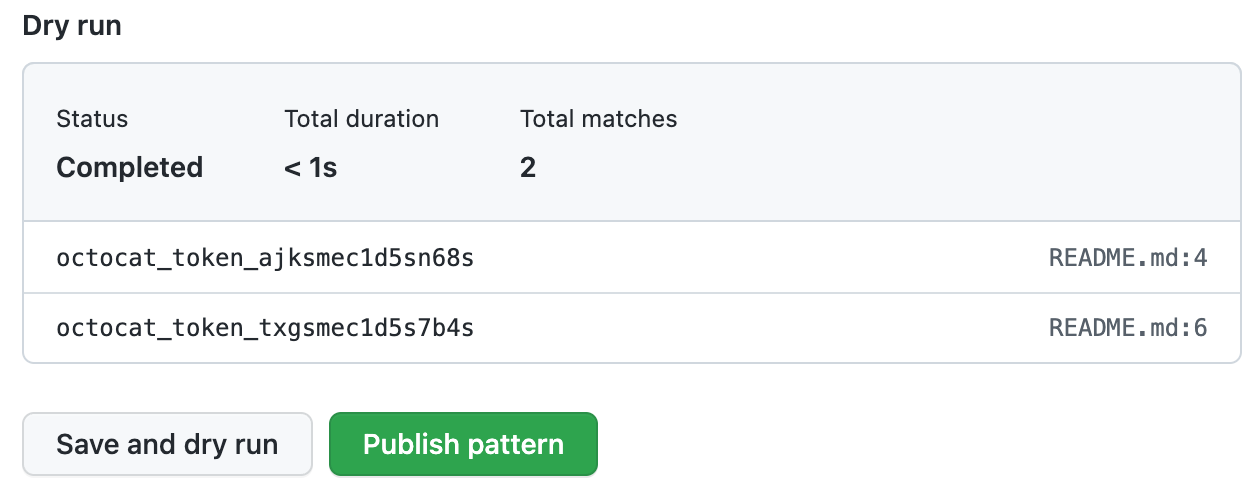
-
Bearbeite das neue benutzerdefinierte Muster, um Probleme mit den Ergebnissen zu beheben, und klicke dann auf Speichern und Probelauf ausführen, um deine Änderungen zu testen.
-
Wenn du mit deinem neuen benutzerdefinierten Muster zufrieden bist, klicke auf Muster veröffentlichen.
Sie können secret scanning so konfigurieren, dass Pushes auf benutzerdefinierte Muster überprüft werden, bevor Commits mit dem Standardbranch zusammengeführt werden. Weitere Informationen findest du unter Aktivieren des Push-Schutzes für ein benutzerdefiniertes Muster.
Generieren eines regulären Ausdrucks für eine Organisation mit Copilot Geheimnisüberprüfung
-
Wählen Sie in der oberen rechten Ecke von GitHub Ihr Profilfoto aus, und klicken Sie dann auf Ihre Organisationen.
-
Klicke neben der Organisation auf Einstellungen.
-
Klicke im Abschnitt „Security“ der Randleiste auf Code security und anschließend auf Global settings.
-
Klicken Sie unter „Benutzerdefinierte Muster“ auf Neues Muster.
-
Geben Sie im Feld „Mustername“ einen Namen für Ihr Muster ein.
-
Klicken Sie oben rechts auf Mit KI generieren.
Note
Du kannst einen regulären Ausdruck manuell eingeben, anstatt den Generator zu verwenden, indem du einen regulären Ausdruck für das Format deines geheimen Musters im Feld „Secret format“ eingibst. Weitere Informationen findest du unter Definieren eines benutzerdefinierten Musters für ein Repository oder Definieren eines benutzerdefinierten Musters für eine Organisation.
-
Im Schiebebereich, der angezeigt wird:
-
Füllen Sie das Feld „Ich möchte einen regulären Ausdruck“ aus, der im Idealfall in einfachem Englisch beschreibt, welche Muster der reguläre Ausdruck erfassen soll. Sie können andere natürliche Sprachen verwenden, aber die Leistung ist möglicherweise nicht so gut wie bei Englisch.
-
Füllen Sie das Feld „Beispiele für das Gesuchte“ aus, und geben Sie ein Beispiel für ein Muster, nach dem Sie suchen möchten.
-
Klicken Sie auf Vorschläge generieren.
-
Klicken Sie optional auf einen Vorschlag, um eine Beschreibung des regulären Ausdrucks anzuzeigen.
-
Klicken Sie auf Ergebnisse verwenden, das angezeigt wird, für das Ergebnis, das Sie verwenden möchten.

-
-
Du kannst auf More options klicken, um andere umgebende Inhalte oder zusätzliche Übereinstimmungsanforderungen für das geheime Format bereitzustellen. GitHub fügt die Beispiele hinzu, die Sie im Schiebebereich eingegeben haben, zum Feld Zeichenfolge testen.
-
Wenn Sie bereit sind, Ihr neues benutzerdefiniertes Muster zu testen, um Übereinstimmungen in ausgewählten Repositorys zu identifizieren, ohne Warnmeldungen zu erzeugen, klicken Sie auf Speichern und Probelauf.
-
Wähle die Repositorys aus, in denen du den Probelauf ausführen möchtest.
- Um den Probelauf in der gesamten Organisation auszuführen, wähle Alle Repositorys in der Organisation aus.
- Wenn du die Repositorys angeben möchtest, in denen der Probelauf ausgeführt werden soll, klicke auf Ausgewählte Repositorys, suche dann bis zu 10 Repositorys, und wähle sie aus.
-
Klicke auf Ausführen, wenn du bereit bist, das neue benutzerdefinierte Muster zu testen.
-
Wenn der Probelauf abgeschlossen ist, wird eine Auswahl der Ergebnisse (bis zu 1000) angezeigt. Überprüfe die Ergebnisse, und identifiziere alle falsch positiven Ergebnisse.

-
Bearbeite das neue benutzerdefinierte Muster, um Probleme mit den Ergebnissen zu beheben, und klicke dann auf Speichern und Probelauf ausführen, um deine Änderungen zu testen.
-
Wenn du mit deinem neuen benutzerdefinierten Muster zufrieden bist, klicke auf Muster veröffentlichen.
Sie können secret scanning so konfigurieren, dass Pushes auf benutzerdefinierte Muster überprüft werden, bevor Commits mit dem Standardbranch zusammengeführt werden. Weitere Informationen findest du unter Aktivieren des Push-Schutzes für ein benutzerdefiniertes Muster.