Note: The "Security risk" and "Security coverage" views are currently in beta and subject to change.
About adoption of code security features
You can use security overview to see which repositories and teams have already enabled each code security feature, and where people need more encouragement to adopt these features. The "Security coverage" view shows a summary and detailed information on feature enablement for an organization. You can filter the view to show a subset of repositories using the "enabled" and "not enabled" links, the "Teams" dropdown menu, and a search field in the page header.
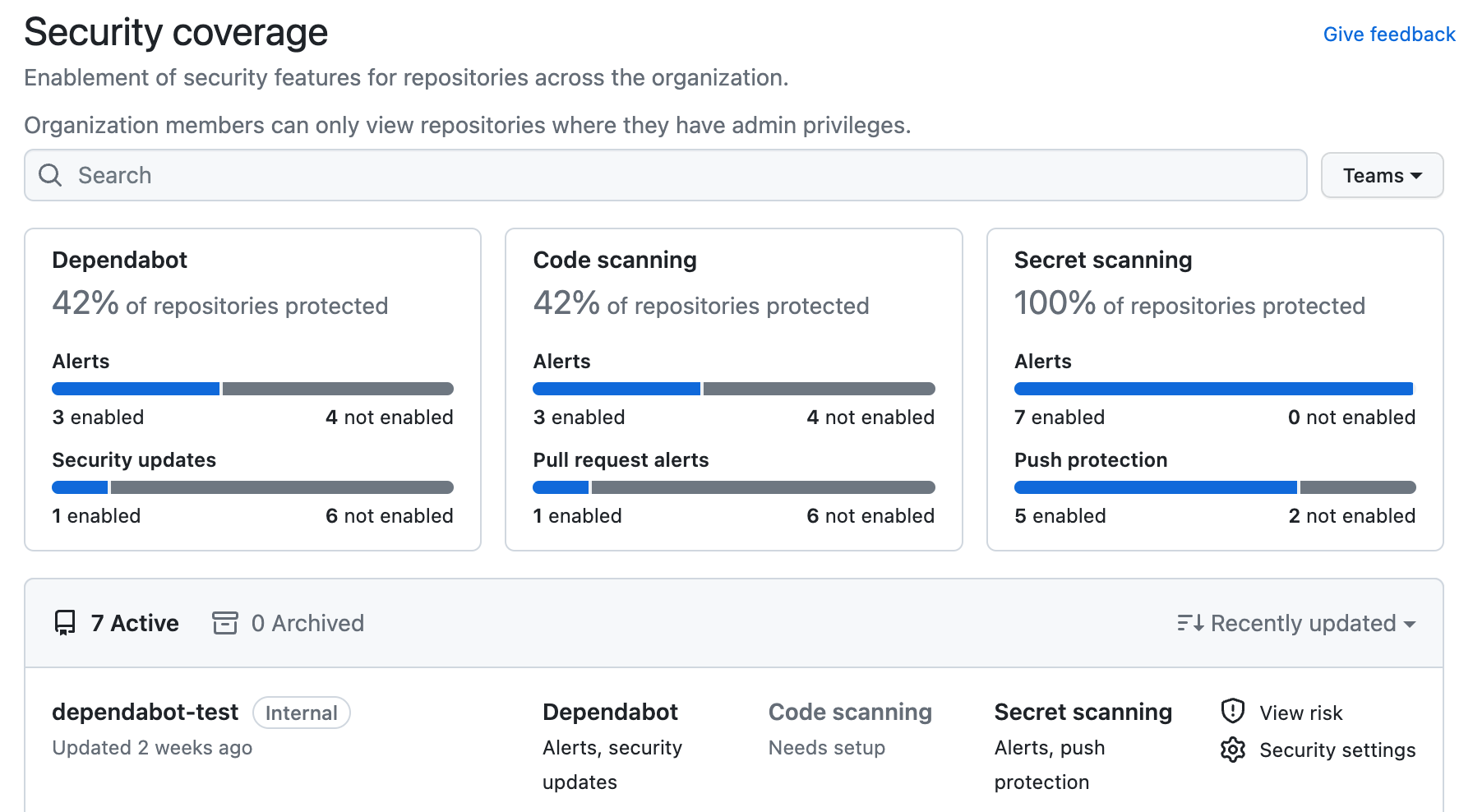
Viewing the enablement of code security features for an organization
The information shown by security overview varies according to your access to repositories, and according to whether GitHub Advanced Security is used by those repositories . For more information, see "About security overview."
-
On your GitHub Enterprise Server instance, navigate to the main page of the organization.
-
Under your organization name, click Security.
-
To display the "Security coverage" view, in the sidebar, click Coverage.
-
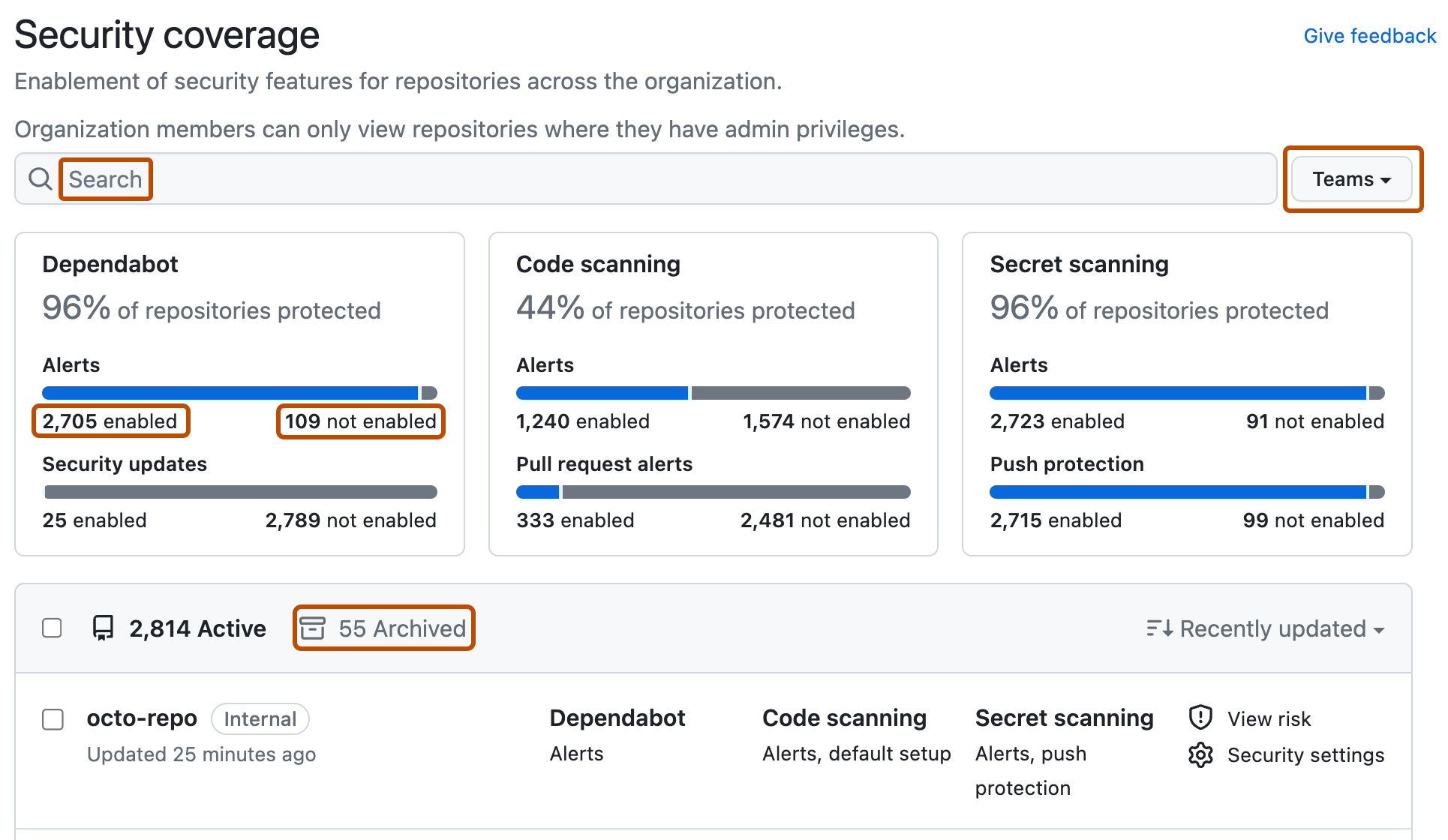
Use options in the page summary to filter results to show the repositories you want to assess. The list of repositories and metrics displayed on the page automatically update to match your current selection. For more information on filtering, see "Filtering alerts in security overview."
- Use the Teams dropdown to show information only for the repositories owned by one or more teams. For more information, see "Managing team access to an organization repository."
- Click NUMBER enabled or NUMBER not enabled in the header for any feature to show only the repositories with that feature enabled or not enabled.
- At the top of the list of repositories, click NUMBER Archived to show only repositories that are archived.
- Click in the search box to add further filters to the repositories displayed.
-
Optionally, click Security settings to enable code security features for a repository and click Save security settings to confirm the changes. If a feature is not shown, it has more complex configuration requirements and you need to use the repository settings dialog. For more information, see "Securing your repository."
Interpreting and acting on the enablement data
Some code security features can and should be enabled on all repositories. For example, secret scanning alerts and push protection reduce the risk of a security leak no matter what information is stored in the repository. If you see repositories that don't already use these features, you should either enable them or discuss an enablement plan with the team who owns the repository. For information on enabling features for a whole organization, see "Managing security and analysis settings for your organization."
Other features are not available for use in all repositories. For example, there would be no point in enabling Dependabot or code scanning for repositories that only use ecosystems or languages that are unsupported. As such, it's normal to have some repositories where these features are not enabled.
Your enterprise may also have configured policies to limit the use of some code security features. For more information, see "Enforcing policies for code security and analysis for your enterprise."