Your repository's Dependabot alerts tab lists all open and closed Dependabot alerts. You can sort the list of alerts, and you can click into specific alerts for more details. You can also dismiss or reopen alerts. For more information, see "About Dependabot alerts."
Viewing Dependabot alerts
- On your GitHub Enterprise Server instance, navigate to the main page of the repository.
- Abaixo do nome do repositório, clique em Segurança.
- Na barra lateral de segurança, clique em Dependabot alerts . Se essa opção está ausente, isso significa que você não tem acesso aos alertas de segurança e precisa receber o acesso. Para obter mais informações, confira "Como gerenciar configurações de segurança e análise para seu repositório".
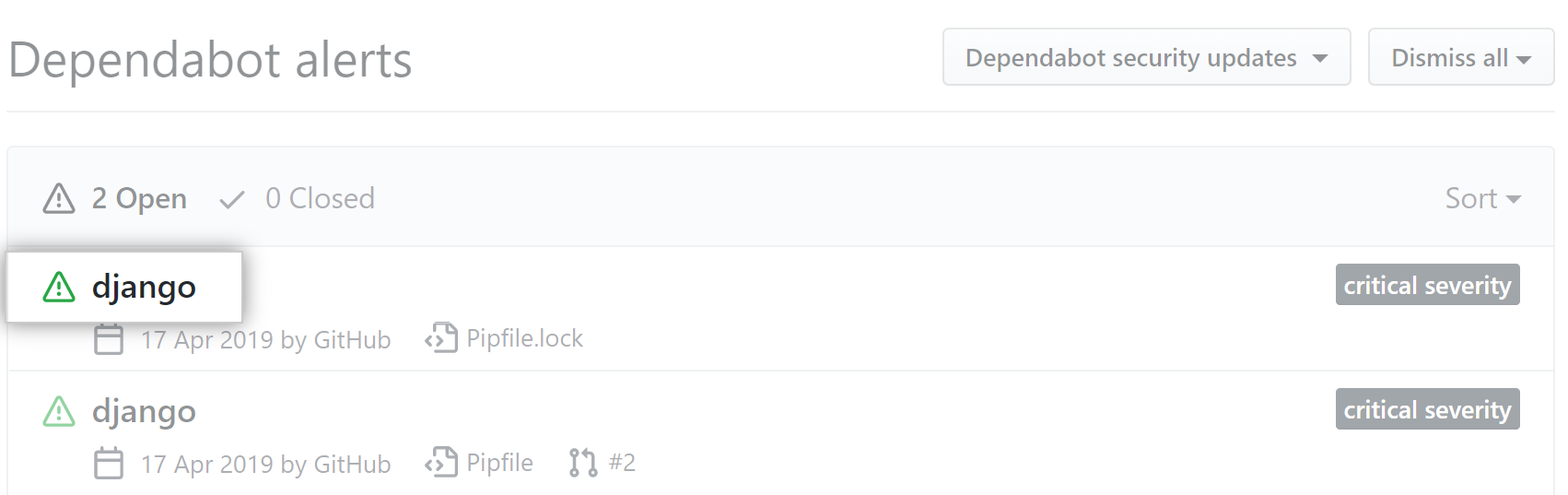
- Click the alert you'd like to view.
Reviewing and fixing alerts
It’s important to ensure that all of your dependencies are clean of any security weaknesses. When Dependabot discovers vulnerabilities in your dependencies, you should assess your project’s level of exposure and determine what remediation steps to take to secure your application.
If a patched version of the dependency is available, you can generate a Dependabot pull request to update this dependency directly from a Dependabot alert. If you have Dependabot security updates enabled, the pull request may be linked will in the Dependabot alert.
In cases where a patched version is not available, or you can’t update to the secure version, Dependabot shares additional information to help you determine next steps. When you click through to view a Dependabot alert, you can see the full details of the security advisory for the dependency including the affected functions. You can then check whether your code calls the impacted functions. This information can help you further assess your risk level, and determine workarounds or if you’re able to accept the risk represented by the security advisory.
Fixing vulnerable dependencies
-
View the details for an alert. For more information, see "Viewing Dependabot alerts" (above).
-
You can use the information on the page to decide which version of the dependency to upgrade to and create a pull request to the manifest or lock file to a secure version.
-
When you're ready to update your dependency and resolve the vulnerability, merge the pull request.
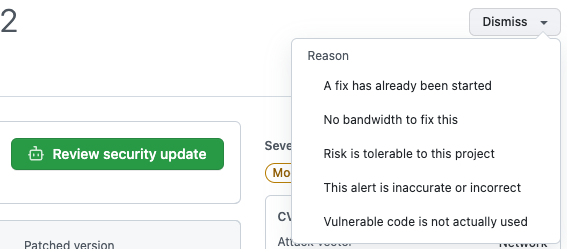
Dismissing Dependabot alerts
Tip: You can only dismiss open alerts.
If you schedule extensive work to upgrade a dependency, or decide that an alert does not need to be fixed, you can dismiss the alert. Dismissing alerts that you have already assessed makes it easier to triage new alerts as they appear.
-
View the details for an alert. For more information, see "Viewing vulnerable dependencies" (above).
-
Select the "Dismiss" dropdown, and click a reason for dismissing the alert.