Información general
Normalmente, dentro de un codespace, puede reenviar puertos de forma privada (solo a sí mismo), a los miembros de la organización o públicamente (a cualquiera que tenga la dirección URL). Para más información, consulta Reenviar puertos en tu codespace.
Como propietario de la organización, es posible que quiera configurar restricciones en las opciones de visibilidad que los usuarios pueden establecer al reenviar puertos. Por ejemplo, por motivos de seguridad, es posible que quiera denegar el reenvío de puertos públicos. Para ello, define una o más políticas en la configuración de GitHub Codespaces de la organización.
Comportamiento al establecer una restricción de visibilidad de puerto
Si hay codespaces existentes que ya no se ajustan a una directiva que ha definido, seguirán funcionando hasta que se detengan o agoten el tiempo de espera. Cuando el usuario reanude el codespace, estará sujeto a las restricciones de directiva.
Note
No se puede deshabilitar el desvío de puertos privados, ya que GitHub Codespaces lo necesita para funcionar como está diseñado, por ejemplo, para reenviar SSH en el puerto 22.
Configurar políticas específicas para los repositorios y a lo largo de la organización
Cuando creas una política, eliges si esta aplica a todos los repositorios de tu organización o solo a algunos específicos. Si configuras una política a lo largo de la organización, entonces cualquier política que configures para los repositorios individuales debe de caer dentro de las restricciones que se configuraron a nivel organizacional. La adición de directivas hace que la elección de opciones de visibilidad sea más restrictiva, no menos.
Por ejemplo, podría crear una directiva para toda la organización que restrinja las opciones de visibilidad solo para la organización. Después, puede establecer una directiva para el repositorio A que no permite la visibilidad pública y de la organización, lo que provocaría que solo el reenvío de puertos privado esté disponible para este repositorio. Establecer una directiva para el repositorio A que permita tanto la visibilidad pública como la de la organización solo daría lugar a visibilidad de la organización, ya que la directiva para toda la organización no permite la visibilidad pública.
Si agrega una directiva para toda la organización, debe establecerla en la opción de visibilidad más permisiva disponible para cualquier repositorio de la organización. Entonces podrás agregar las políticas específicas para los repositorios y así restringir aún más la elección.
Note
Las directivas de Codespaces solo se aplican a los codespaces que paga tu organización. Si alguien crea un codespace para un repositorio de tu organización por su cuenta, dicho codespace no estará sujeto a estas políticas. Para más información, consulta Selección de quién posee y paga los codespaces de una organización.
Adición de una directiva para limitar las opciones de visibilidad de puertos
-
En la esquina superior derecha de GitHub, seleccione la foto del perfil y haga clic en Sus organizaciones.
-
Junto a la organización, haga clic en Settings.
-
En la sección "Código, planificación y automatización" de la barra lateral, selecciona Codespaces y, después, haz clic en Directivas.
-
En la página "Directivas de codespaces", haga clic en Crear directiva.
-
Ingresa un nombre para tu política nueva.
-
Haga clic en Agregar restricción y elija Visibilidad de puertos.
-
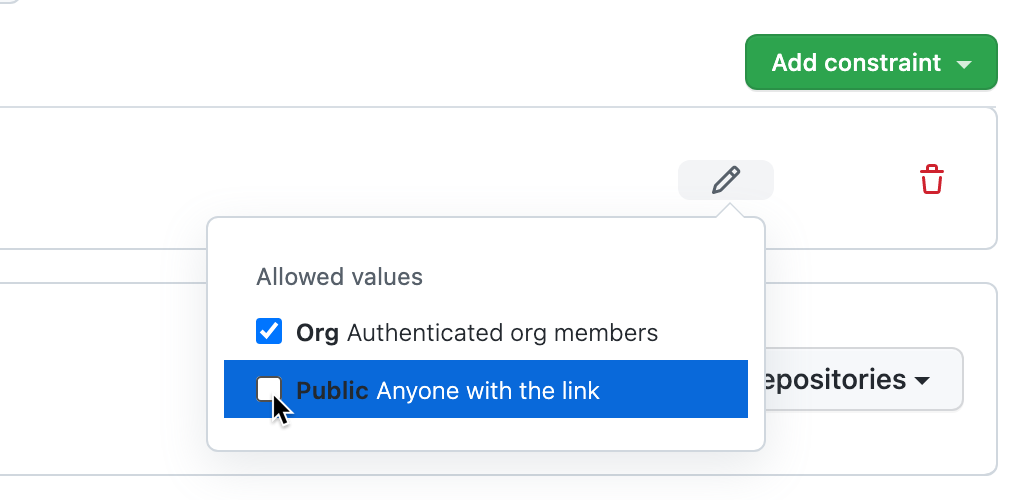
Haz clic en para editar la restricción.
-
Borre la selección de las opciones de visibilidad de puertos (Organización o Pública) que no quiere que estén disponibles.
-
Haz clic fuera del cuadro de diálogo para cerrarlo.
-
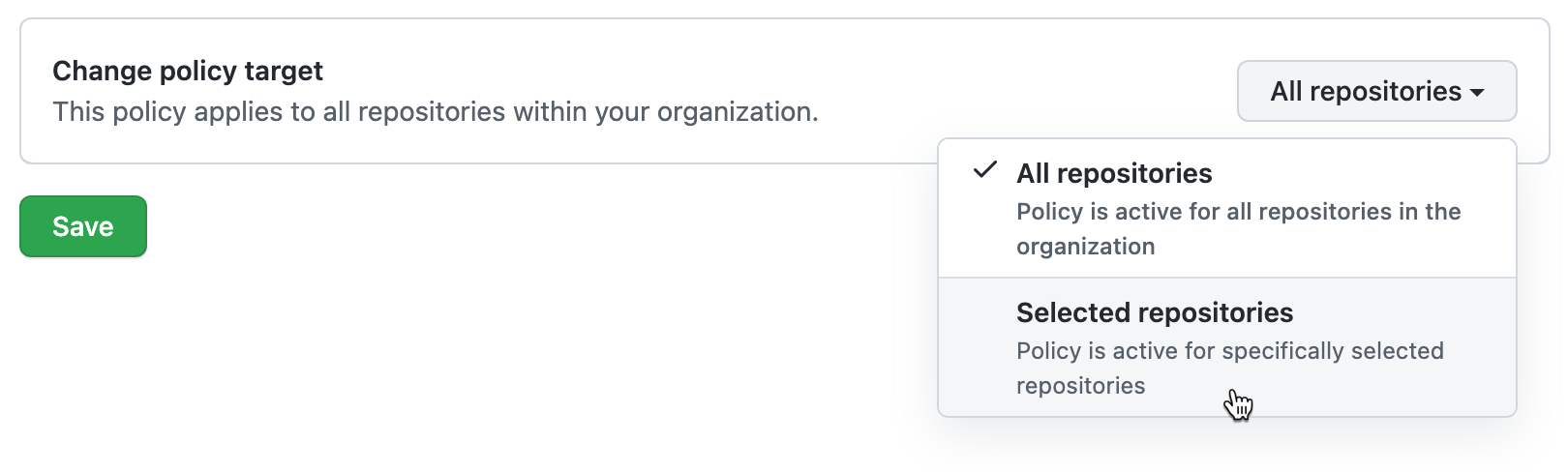
De forma predeterminada, la directiva se establece para aplicarse a todos los repositorios; si deseas que se aplique solo a algunos de los repositorios de la organización, haz clic en Todos los repositorios y, a continuación, haz clic en Repositorios seleccionados en el menú desplegable.
Note
Si vas a agregar una restricción a una directiva existente que ya contiene la restricción "Maximum codespaces per user", no podrás aplicar la directiva a los repositorios seleccionados. Esto se debe a que la restricción "Máximo de codespaces por usuario" siempre se aplica a todos los repositorios de la organización.
Con la opción Repositorios seleccionados seleccionada:
-
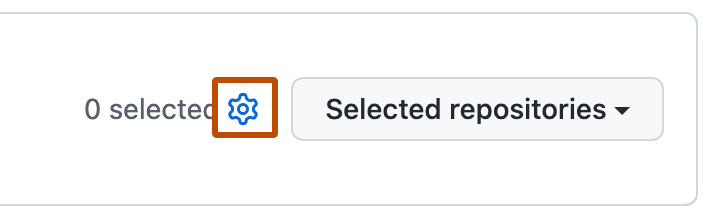
Haga clic en .
-
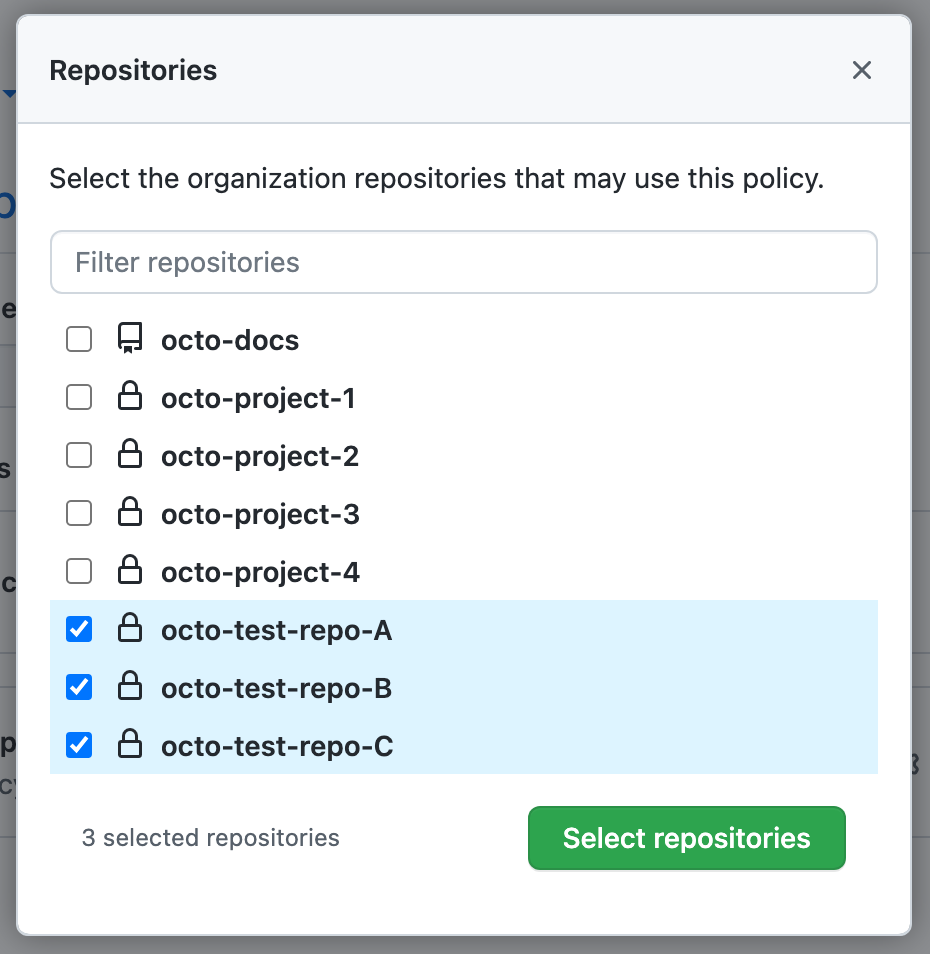
Selecciona los repositorios a los cuales quieres que aplique esta política.
-
En la parte inferior de la lista de repositorios, haga clic en Select repositories.
-
-
Si quieres agregar otra restricción a la directiva, haz clic en Agregar restricción y elige otra restricción. Para obtener información sobre otras restricciones, consulta:
-
Cuando hayas terminado de agregar restricciones a la directiva, haz clic en Guardar.
La directiva se aplicará a todos los codespaces nuevos que se facturen a tu organización. La restricción de visibilidad de puertos también se aplicará a los codespaces existentes la próxima vez que se inicien.
Editar una política
Puedes editar una directiva existente. Por ejemplo, puede que te interese agregar restricciones a una directiva o quitarlas.
- Mostrar la página de "Políticas del Codespaces". Para más información, consulta Adición de una directiva para limitar las opciones de visibilidad de puertos.
- Haz clic en el nombre de la política que quieres editar.
- Junto a la restricción "Visibilidad del puerto", haz clic en .
- Realice los cambios necesarios y haga clic en Save.
Borrar una política
-
Mostrar la página de "Políticas del Codespaces". Para más información, consulta Adición de una directiva para limitar las opciones de visibilidad de puertos.
-
Haz clic en a la derecha de la directiva que quieres eliminar.