Sobre os executores auto-hospedados do GitHub Actions
O GitHub Actions permite que os usuários ba sua empresa melhorem a produtividade automatizando todas as fases do fluxo de trabalho de desenvolvimento de software. Para obter mais informações, confira Sobre o GitHub Actions para empresas.
Com GitHub Actions, os desenvolvedores podem escrever e combinar tarefas individuais denominadas ações para criar fluxos de trabalho personalizados. Você pode hospedar seu próprio computador de executor para executar esses trabalhos e esse computador será chamado de executor auto-hospedado. Os executores auto-hospedados podem ser físicos, virtuais, em um contêiner, no local ou em uma nuvem. Seu computador executor conecta-se ao GitHub usando o aplicativo de executor auto-hospedado de GitHub Actions. Todos auto-hospedados podem ser executados no Linux, Windows ou macOS. Para saber mais, confira Sobre executores auto-hospedados.
Como alternativa, você pode usar máquinas de executores que GitHub hospeda. Os executores hospedados em GitHub estão fora do escopo deste guia. Para saber mais, confira Usar executores hospedados no GitHub.
Este guia mostra como aplicar uma abordagem de gerenciamento centralizada para os executores auto-hospedados para GitHub Actions na sua empresa. No guia, você realizará as seguintes tarefas.
- Configurar uma política limitada para restringir as ações e os fluxos de trabalho reutilizáveis que podem ser executados na empresa
- Implantar um executor auto-hospedado para a sua empresa
- Criar um grupo para gerenciar o acesso aos executores disponíveis para sua empresa
- Opcionalmente, restringir ainda mais os repositórios que podem usar o executor
- Opcionalmente, para criar e dimensionar executores auto-hospedados automaticamente, use Actions Runner Controller (ARC). Para saber mais, confira Sobe o Controlador de Executores de Ação.
Você também encontrará informações adicionais sobre como monitorar e proteger seus executores auto-hospedados, e como personalizar o software nas máquinas dos seus executores.
Depois que você terminar o guia, os membros da sua empresa poderão executar tarefas do fluxo de trabalho do GitHub Actions no computador de um executor auto-hospedado.
Pré-requisitos
- Você precisa ter acesso ao computador que usará como um executor auto-hospedado no seu ambiente.
- Sua empresa deve possuir pelo menos uma organização. Para saber mais, confira Sobre organizações e Criar uma organização do início.
1. Configurar políticas para o GitHub Actions
Primeiro, habilite o GitHub Actions para todas as organizações e configure uma política para restringir as ações e os fluxos de trabalho reutilizáveis que têm permissão de execução na sua empresa. Opcionalmente, os proprietários da organização podem restringir ainda mais essas políticas para cada organização.
- No canto superior direito do GitHub, selecione sua foto de perfil.
- Dependendo do ambiente, selecione Sua empresa ou Suas empresas e escolha a empresa que deseja ver.
- Do lado esquerdo da página, na barra lateral da conta empresarial, clique em Políticas.
- Em " Políticas", clique em Ações.
- Em "Políticas", selecione Habilitar para todas as organizações.
- Para habilitar ações locais e fluxos de trabalho reutilizáveis e ações criadas pelo GitHub, selecione Permitir a empresa e fluxos de trabalho reutilizáveis e ações selecionados que não são empresa e Permitir ações criadas pelo GitHub .
- Clique em Save (Salvar).
Você pode configurar políticas adicionais para restringir as ações disponíveis para os membros da empresa. Para saber mais, confira Aplicando políticas para o GitHub Actions na sua empresa.
2. Implantar o executor auto-hospedado para sua empresa
Em seguida, adicione um executor auto-hospedado à sua empresa. O GitHub vai orientar você durante a instalação do software necessário no computador do executor. Depois de implantar o executor, você poderá verificar a conectividade entre o computador do executor e a sua empresa.
Adicionando o executor auto-hospedado
-
No canto superior direito do GitHub, selecione sua foto de perfil.
-
Dependendo do ambiente, selecione Sua empresa ou Suas empresas e escolha a empresa que deseja ver.
-
Do lado esquerdo da página, na barra lateral da conta empresarial, clique em Políticas.
-
Em " Políticas", clique em Ações.
-
Clique na guia Executores.
-
Clique em Novo executor, depois em Novo executor auto-hospedado. 1. Selecione a imagem e a arquitetura do sistema operacional do computador do executor auto-hospedado.
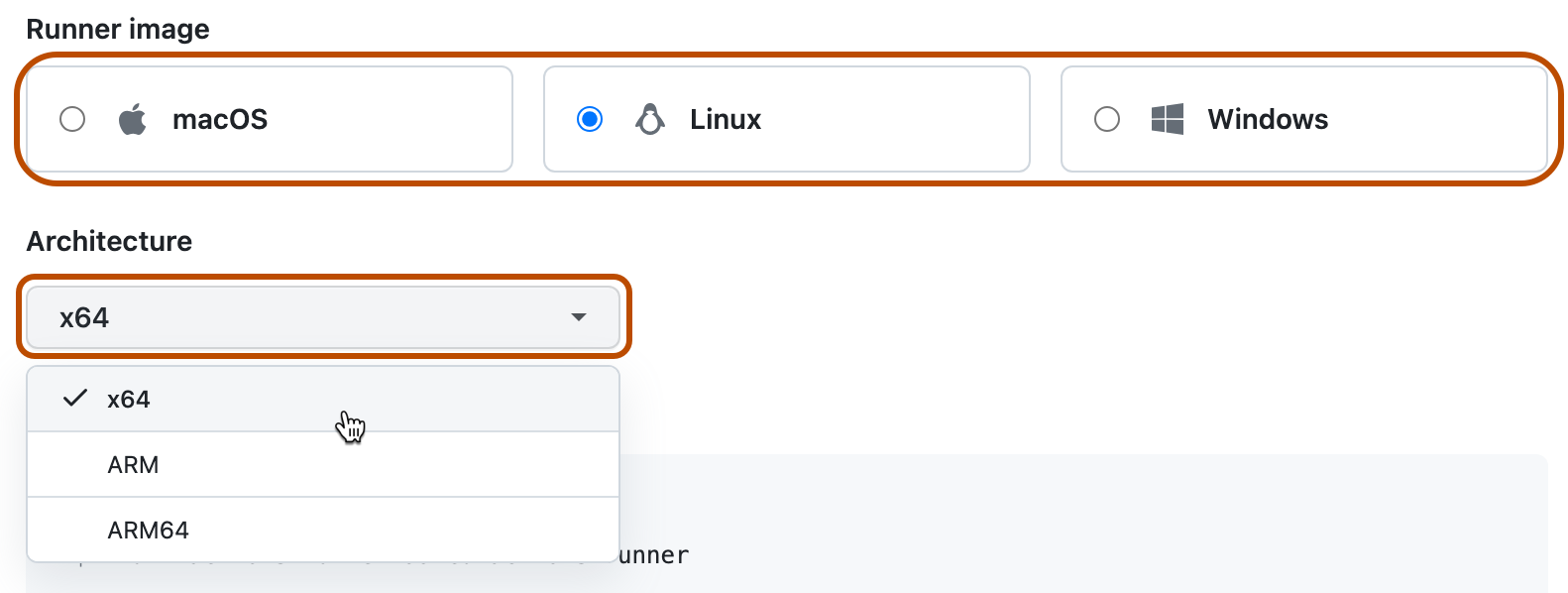
-
Você verá instruções mostrando como baixar o executor e instalá-lo em sua máquina de executor auto-hospedada.
Abra um shell em sua máquina de executor auto-hospedado e execute cada comando shell na ordem mostrada.
Observação: no Windows, caso você deseje instalar o aplicativo do executor auto-hospedado como um serviço, abra um shell com privilégios de administrador. Também recomendamos que você use
C:\actions-runnercomo diretório para o aplicativo do executor auto-hospedado para que as contas do sistema do Windows possam acessar o diretório do executor.As instruções te ajudam a completar estas tarefas:
- Transferindo e extraindo o aplicativo do executor auto-hospedado.
- Executar o script
configpara configurar o aplicativo do executor auto-hospedado e registrá-lo no GitHub Actions. O scriptconfigexige a URL de destino e um token de tempo limitado gerado automaticamente para autenticar a solicitação.- No Windows, o script
configtambém pergunta se você deseja instalar o aplicativo do executor auto-hospedado como um serviço. Para Linux e macOS, você pode instalar um serviço depois de terminar de adicionar o executor. Para obter mais informações, confira "Configurar o aplicativo do executor auto-hospedado como um serviço".
- No Windows, o script
- Executando o aplicativo do executor auto-hospedado para conectar a máquina ao GitHub Actions.
Verificando se o seu executor auto-hospedado foi adicionado com sucesso
Após concluir as etapas para adicionar um executor auto-hospedado, o executor e seu status agora estão listados em "Executores".
A aplicação dos executores auto-hospedados deve estar activa para que o executor aceite os trabalhos. Quando o aplicativo do executor estiver conectado ao GitHub e pronto para receber trabalhos, você verá a seguinte mensagem no terminal do computador.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
3. Gerenciar o acesso ao executor auto-hospedado usando um grupo
Você pode criar um grupo de executor para gerenciar o acesso ao executor que você adicionou à sua empresa. Você usará o grupo para escolher quais organizações podem executar trabalhos a partir de GitHub Actions no executor.
O GitHub adiciona todos os novos executores a um grupo. Os executores podem estar em um grupo por vez. Por padrão, o GitHub adiciona novos executores ao grupo “Default”.
-
No canto superior direito do GitHub, selecione sua foto de perfil.
-
Dependendo do ambiente, selecione Sua empresa ou Suas empresas e escolha a empresa que deseja ver.
-
Do lado esquerdo da página, na barra lateral da conta empresarial, clique em Políticas.
-
Em " Políticas", clique em Ações.
-
Clique na guia Grupos de executores.
-
Clique em Novo grupo de executores.
-
Em "Nome do grupo", digite um nome para o grupo de executores.
-
Para escolher uma política de acesso à organização, em "Acesso à organização", selecione o menu suspenso Acesso à organização e clique em Organizações selecionadas.
-
À direita da lista suspensa com a política de acesso da organização, clique em .
-
Selecione as organizações que você gostaria de conceder acesso ao grupo do executor.
-
Opcionalmente, para permitir que repositórios públicos nas organizações selecionadas usem executores no grupo, selecione Permitir repositórios públicos.
Warning
Recomendamos que você use apenas executores auto-hospedados com repositórios privados. Isso acontece porque as bifurcações do seu repositório público podem executar código perigoso em seu computador de executor auto-hospedado criando uma solicitação de pull que executa o código em um fluxo de trabalho.
Para saber mais, confira Sobre executores auto-hospedados.
-
Clique em Criar grupo para criar o grupo e aplicar a política.
-
Clique na aba "Executores".
-
Na lista de executores, clique no executor que você implantou na seção anterior.
-
Clique em Editar.
-
Clique em Grupos de executores .
-
Na lista de grupos de executores, clique no nome do grupo que você criou anteriormente.
-
Clique em Salvar para mover o executor para o grupo.
Você já implantou um executor auto-hospedado que pode executar trabalhos de GitHub Actions dentro das organizações que você especificou.
4. Restringir ainda mais o acesso ao executor auto-hospedado
Opcionalmente, os proprietários da organização e os usuários com a permissão "Gerenciar executores e conjuntos de executores da organização" podem restringir ainda mais a política de acesso do grupo de executores que você criou. Por exemplo, um proprietário da organização pode permitir que apenas certos repositórios na organização usem o grupo de executores.
Para saber mais, confira Gerenciar o acesso a executores auto-hospedados usando grupos.
Para obter mais informações sobre funções de organização personalizadas, confira Sobre as funções da organização personalizadas.
5. Escalar automaticamente os executores auto-hospedados
Como opção, é possível usar o Actions Runner Controller (ARC) para dimensionar automaticamente os executores auto-hospedados. O Actions Runner Controller (ARC) é um operador Kubernetes que orquestra e dimensiona executores auto-hospedados para o GitHub Actions. Para obter mais informações, confira Padrão do operador da documentação do Kubernetes.
Com o ARC, você pode criar conjuntos de dimensionamento de executores que são dimensionados automaticamente com base no número de fluxos de trabalho em execução em seu repositório, organização ou empresa. Como os executores controlados podem ser efêmeros e baseados em contêineres, novas instâncias do executor podem expandir ou reduzir rapidamente e de forma limpa. Para obter mais informações sobre o dimensionamento automático, confira Redimensionamento automático com executores auto-hospedados.
Próximas etapas
-
Você pode monitorar executores auto-hospedados e resolver problemas comuns. Para saber mais, confira Monitorar e solucionar problemas de executores auto-hospedados.
-
GitHub recomenda que você revise considerações de segurança para máquinas de executores auto-hospedados. Para saber mais, confira Fortalecimento de segurança para o GitHub Actions.
-
Se usar o GitHub Enterprise Server, você poderá sincronizar manualmente os repositórios no GitHub.com que contêm ações para a sua empresa no GitHub Enterprise Server. Como alternativa, você pode permitir que os integrantes da sua empresa acessem automaticamente as ações de GitHub.com usando GitHub Connect. Para obter mais informações, consulte o seguinte.
- Sincronizar ações do GitHub.com manualmente na documentação do GitHub Enterprise Server
- Habilitar o acesso automático a GitHub.com usando o GitHub Connect na documentação do GitHub Enterprise Server
-
Você pode personalizar o software disponível nas suas máquinas de executores auto-hospedados ou configurar seus executores para executar softwares similares a executores hospedados em GitHub. O software que alimenta máquinas de executores para GitHub Actions é de código aberto. Para obter mais informações, confira os repositórios
actions/runnereactions/runner-images.