About Dependabot for GitHub Enterprise Server
Dependabot helps users of your GitHub Enterprise Server instance find and fix vulnerabilities in their dependencies. You can enable Dependabot alerts to notify users about vulnerable dependencies and Dependabot updates to fix the vulnerabilities and keep dependencies updated to the latest version.
Dependabot is just one of many features available to harden supply chain security for your GitHub Enterprise Server instance. For more information about the other features, see "About supply chain security for your enterprise."
About Dependabot alerts
With Dependabot alerts, GitHub identifies insecure dependencies in repositories and creates alerts on your GitHub Enterprise Server instance, using data from the GitHub Advisory Database and the dependency graph service.
We add advisories to the GitHub Advisory Database from the following sources:
- Security advisories reported on GitHub
- The National Vulnerability database
- The npm Security advisories database
- The FriendsOfPHP database
- The Go Vulncheck database
- The Python Packaging Advisory database
- The Ruby Advisory database
- The RustSec Advisory database
- Community contributions. For more information, see https://github.com/github/advisory-database/pulls.
If you know of another database we should be importing advisories from, tell us about it by opening an issue in https://github.com/github/advisory-database.
After you enable Dependabot alerts for your enterprise, vulnerability data is synced from the GitHub Advisory Database to your instance once every hour. Only GitHub-reviewed advisories are synchronized. For more information, see "Browsing security advisories in the GitHub Advisory Database."
You can also choose to manually sync vulnerability data at any time. For more information, see "Viewing the vulnerability data for your enterprise."
Note: When you enable Dependabot alerts, no code or information about code from your GitHub Enterprise Server instance is uploaded to GitHub.com.
When your GitHub Enterprise Server instance receives information about a vulnerability, it identifies repositories in your GitHub Enterprise Server instance that use the affected version of the dependency and generates Dependabot alerts. You can choose whether or not to notify users automatically about new Dependabot alerts.
For repositories with Dependabot alerts enabled, scanning is triggered on any push to the default branch that contains a manifest file or lock file. Additionally, when a new vulnerability record is added to your GitHub Enterprise Server instance, GitHub Enterprise Server scans all existing repositories on your GitHub Enterprise Server instance and generates alerts for any repository that is vulnerable. For more information, see "About Dependabot alerts."
About Dependabot updates
After you enable Dependabot alerts, you can choose to enable Dependabot updates. When Dependabot updates are enabled for your GitHub Enterprise Server instance, users can configure repositories so that their dependencies are updated and kept secure automatically.
Note: Dependabot updates on GitHub Enterprise Server requires GitHub Actions with self-hosted runners.
By default, GitHub Actions runners used by Dependabot need access to the internet, to download updated packages from upstream package managers. For Dependabot updates powered by GitHub Connect, internet access provides your runners with a token that allows access to dependencies and advisories hosted on GitHub.com.
With Dependabot updates, GitHub automatically creates pull requests to update dependencies in two ways.
- Dependabot version updates: Users add a Dependabot configuration file to the repository to enable Dependabot to create pull requests when a new version of a tracked dependency is released. For more information, see "About Dependabot version updates."
- Dependabot security updates: Users toggle a repository setting to enable Dependabot to create pull requests when GitHub detects a vulnerability in one of the dependencies of the dependency graph for the repository. For more information, see "About Dependabot alerts" and "About Dependabot security updates."
Enabling Dependabot alerts
Before you can enable Dependabot alerts:
- You must enable GitHub Connect. For more information, see "Managing GitHub Connect."
- You must enable the dependency graph. For more information, see "Enabling the dependency graph for your enterprise."
-
In the top-right corner of GitHub Enterprise Server, click your profile photo, then click Enterprise settings.
-
In the enterprise account sidebar, click GitHub Connect.
-
Under "Dependabot", to the right of "Users can receive vulnerability alerts for open source code dependencies", select the dropdown menu and click Enabled without notifications. Optionally, to enable alerts with notifications, click Enabled with notifications.
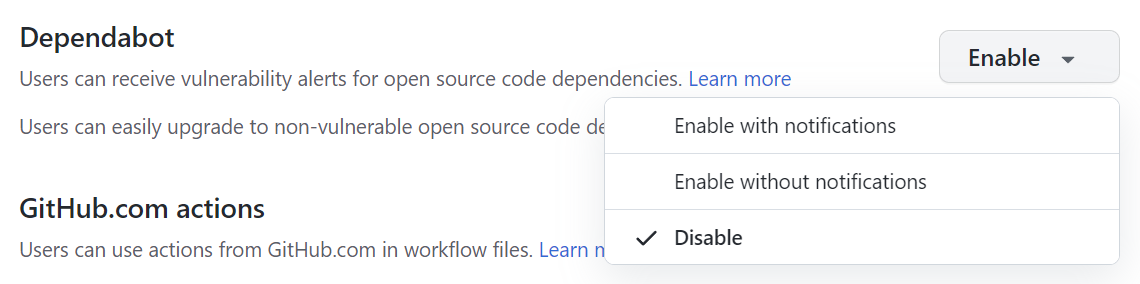
Tip: We recommend configuring Dependabot alerts without notifications for the first few days to avoid an overload of emails. After a few days, you can enable notifications to receive Dependabot alerts as usual.
Enabling Dependabot updates
After you enable Dependabot alerts for your enterprise, you can enable Dependabot updates.
Before you enable Dependabot updates, you must configure your GitHub Enterprise Server instance to use GitHub Actions with self-hosted runners. For more information, see "Getting started with GitHub Actions for GitHub Enterprise Server."
Dependabot updates are not supported on GitHub Enterprise Server if your enterprise uses clustering.
Note: After you enable the dependency graph, you can use the Dependabot action. The action will raise an error if any vulnerabilities or invalid licenses are being introduced. For more information about the action, and for instructions about how to download the most recent version, see "Using the latest version of the official bundled actions."
-
Sign in to your GitHub Enterprise Server instance at
http(s)://HOSTNAME/login. -
From an administrative account on GitHub Enterprise Server, in the upper-right corner of any page, click .
-
If you're not already on the "Site admin" page, in the upper-left corner, click Site admin.
-
In the " Site admin" sidebar, click Management Console.
-
In the "Settings" sidebar, click Security.
-
Under "Security", select Dependabot security updates.
-
Under the "Settings" sidebar, click Save settings.
Note: Saving settings in the Management Console restarts system services, which could result in user-visible downtime.
-
Wait for the configuration run to complete.
-
Click Visit your instance.
-
Configure dedicated self-hosted runners to create the pull requests that will update dependencies. This is required because the workflows use a specific runner label. For more information, see "Managing self-hosted runners for Dependabot updates on your enterprise."
-
In the top-right corner of GitHub Enterprise Server, click your profile photo, then click Enterprise settings.

-
In the enterprise account sidebar, click GitHub Connect.
-
Under "Dependabot", to the right of "Users can easily upgrade to non-vulnerable open source code dependencies", click Enable.
When you enable Dependabot alerts, you should consider also setting up GitHub Actions for Dependabot security updates. This feature allows developers to fix vulnerabilities in their dependencies. For more information, see "Managing self-hosted runners for Dependabot updates on your enterprise."
If you need enhanced security, we recommend configuring Dependabot to use private registries. For more information, see "Configuring access to private registries for Dependabot."