Note: Your site administrator must enable secret scanning for your GitHub Enterprise Server instance before you can use this feature. For more information, see "Configuring secret scanning for your appliance."
You may not be able to enable or disable secret scanning, if an enterprise owner has set a policy at the enterprise level. For more information, see "Enforcing policies for code security and analysis for your enterprise."
Enabling secret scanning
You can enable secret scanning for any repository that is owned by an organization. Once enabled, secret scanning scans for any secrets in your entire Git history on all branches present in your GitHub repository. Secret scanning does not scan issues.
You can also enable secret scanning for multiple repositories in an organization at the same time. For more information, see "Quickstart for securing your organization."
Note: If your organization is owned by an enterprise account, an enterprise owner can also enable secret scanning at the enterprise level. For more information, see "Managing GitHub Advanced Security features for your enterprise."
A repository administrator can choose to disable secret scanning for a repository at any time. For more information, see "Managing security and analysis settings for your repository."
-
On your GitHub Enterprise Server instance, navigate to the main page of the repository.
-
Under your repository name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.
-
In the "Security" section of the sidebar, click Code security and analysis.
-
If Advanced Security is not already enabled for the repository, to the right of "GitHub Advanced Security", click Enable.
-
Review the impact of enabling Advanced Security, then click Enable GitHub Advanced Security for this repository.
-
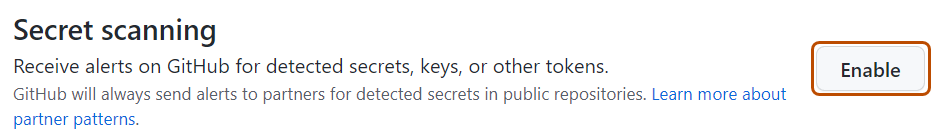
When you enable Advanced Security, secret scanning may automatically be enabled for the repository due to the organization's settings. If "Secret scanning" is shown with an Enable button, you still need to enable secret scanning by clicking Enable. If you see a Disable button, secret scanning is already enabled.
Enabling additional features for secret scanning
You can enable the following additional secret scanning features through your repository's "Code security and analysis" settings:
- Push protection. For more information, see "Push protection for repositories and organizations."
- Scanning for custom patterns. For more information, see "Defining custom patterns for secret scanning."
Excluding directories from secret scanning
You can configure a secret_scanning.yml file to exclude directories from secret scanning, including when you use push protection. For example, you can exclude directories that contain tests or randomly generated content.
-
On your GitHub Enterprise Server instance, navigate to the main page of the repository.
-
Above the list of files, using the Add file drop-down, click Create new file.
-
In the file name field, type .github/secret_scanning.yml.
-
Under Edit new file, type
paths-ignore:followed by the paths you want to exclude from secret scanning.paths-ignore: - "foo/bar/*.js"You can use special characters, such as
*to filter paths. For more information about filter patterns, see "Workflow syntax for GitHub Actions."Notes:
- If there are more than 1,000 entries in
paths-ignore, secret scanning will only exclude the first 1,000 directories from scans. - If
secret_scanning.ymlis larger than 1 MB, secret scanning will ignore the entire file.
- If there are more than 1,000 entries in
You can also ignore individual alerts from secret scanning. For more information, see "Managing alerts from secret scanning."