Auf der Dependabot alerts-Registerkarte Ihres Repositorys werden alle offenen und geschlossenen Dependabot alerts und die entsprechenden Dependabot security updates angezeigt. Du kannst Warnungen nach Paket, Ökosystem oder Manifest filtern. Du kannst die Warnungsliste sortieren, und du kannst auf bestimmte Warnungen klicken, um weitere Details anzuzeigen. Du kannst auch Warnungen verwerfen oder erneut öffnen, entweder einzeln oder mehrere gleichzeitig. Weitere Informationen findest du unter Informationen zu Dependabot-Warnungen.
Sie können automatische Sicherheitsupdates für jedes Repository aktivieren, das Dependabot alerts und das Abhängigkeitsdiagramm verwendet. Weitere Informationen findest du unter Informationen zu Dependabot-Sicherheitsupdates.
Informationen zu Updates für anfällige Abhängigkeiten in deinem Repository
GitHub generiert Dependabot alerts, wenn erkannt wird, dass der Standardbranch der Codebasis Abhängigkeiten verwendet, für die Sicherheitsrisiken bekannt sind. Wenn GitHub bei Repositorys mit aktivierten Dependabot security updates eine anfällige Abhängigkeit im Standardbranch erkennt, erstellt Dependabot einen Pull Request, um diese zu beheben. Der Pull Request aktualisiert die Abhängigkeit auf die minimal mögliche sichere Version, die erforderlich ist, um das Sicherheitsrisiko zu vermeiden.
Dependabot generiert keine Dependabot alerts für Malware. Weitere Informationen findest du unter Informationen zu GitHub Advisory Database.
Jede Dependabot-Warnung verfügt über einen eindeutigen numerischen Bezeichner, und auf der Dependabot alerts-Registerkarte wird eine Warnung für jedes erkannte Sicherheitsrisiko aufgeführt. Dependabot alerts-Legacywarnungen haben Sicherheitsrisiken nach Abhängigkeit gruppiert und eine einzelne Warnung pro Abhängigkeit generiert. Wenn du zu einer Dependabot-Legacywarnung navigierst, wirst du zu einer Dependabot alerts-Registerkarte weitergeleitet, die nach diesem Paket gefiltert ist.
Du kannst Dependabot alerts mithilfe einer Vielzahl von Filtern und Sortieroptionen filtern und sortieren, die auf der Benutzeroberfläche verfügbar sind. Weitere Informationen findest du im Folgenden unter Priorisieren von Dependabot alerts.
Du kannst auch Aktionen überwachen, die als Reaktion auf Dependabot-Warnungen ausgeführt wurden. Weitere Informationen findest du unter Prüfen von Sicherheitswarnungen.
Priorisieren von Dependabot alerts
GitHub unterstützt dich dabei, die Korrektur von Dependabot alerts zu priorisieren. Standardmäßig werden Dependabot alerts nach Relevanz sortiert. Mit der Sortierung nach „Wichtigste“ kannst du priorisieren, auf welche Dependabot alerts du dich zuerst konzentrieren möchtest. Warnungen werden basierend auf potenziellen Auswirkungen, Aktionen und Relevanz bewertet. Unsere Priorisierungsberechnung wird ständig verbessert und umfasst Faktoren wie die CVSS-Bewertung,den Abhängigkeitsbereich und ob anfällige Funktionsaufrufe für die Warnung gefunden werden.
Du kannst auch Dependabot auto-triage rules verwenden, um Dependabot alerts zu priorisieren. Weitere Informationen findest du unter Über Auto-Triage-Regeln von Dependabot.
Du kannst Dependabot alerts sortieren und filtern, indem du Filter als key:value-Paare in die Suchleiste eingibst.
| Option | Beschreibung des Dataflows | Beispiel |
|---|---|---|
ecosystem | Zeigt Warnungen für das ausgewählte Ökosystem an. | Verwende ecosystem:npm zum Anzeigen von Dependabot alerts für npm. |
has | Zeigt Warnungen an, die den ausgewählten Filterkriterien entsprechen. | Verwende has:patch, um Warnungen im Zusammenhang mit Empfehlungen anzuzeigen, die einen Patch betreffen.Verwende has:vulnerable-calls zum Anzeigen von Warnungen im Zusammenhang mit Aufrufen anfälliger Funktionen. |
is | Zeigt Warnungen basierend auf ihrem Status an. | Verwende is:open, um offene Warnungen anzuzeigen. |
manifest | Zeigt Warnungen für das ausgewählte Manifest an. | Verwende manifest:webwolf/pom.xml, um Warnungen für die Datei „pom.xml“ der Webwolf-Anwendung anzuzeigen. |
package | Zeigt Warnungen für das ausgewählte Paket an. | Verwende package:django, um Warnungen für Django anzuzeigen. |
resolution | Zeigt Warnungen mit dem ausgewählten Auflösungsstatus an. | Verwende resolution:no-bandwidth zum Anzeigen von Warnungen, die ausgesetzt wurden, weil zur Behebung keine Zeit oder keine Ressourcen verfügbar sind. |
repo | Zeigt Warnungen basierend auf dem Repository an, auf das sie sich beziehen. Beachte, dass dieser Filter nur für die Sicherheitsübersicht verfügbar ist. Weitere Informationen findest du unter Informationen zur Sicherheitsübersicht. | Verwende repo:octocat-repo, um Warnungen im Repository namens octocat-repo anzuzeigen. |
scope | Zeigt Warnungen basierend auf dem Bereich der Abhängigkeit an, auf die sie sich beziehen. | Verwende scope:development, um Warnungen für Abhängigkeiten anzuzeigen, die nur während der Entwicklung verwendet werden. |
severity | Zeigt Warnungen basierend auf ihrem Schweregrad an. | Verwende severity:high, um Warnungen mit dem Schweregrad „Hoch“ anzuzeigen. |
sort | Zeigt Warnungen entsprechend der ausgewählten Sortierreihenfolge an. | Die Standardsortieroption für Warnungen ist sort:most-important, die Warnungen nach Wichtigkeit bewertet.Verwende sort:newest, um die neuesten von Dependabot gemeldeten Warnungen anzuzeigen. |
Zusätzlich zu den über die Suchleiste verfügbaren Filtern kannst du Dependabot alerts mithilfe der Dropdownmenüs oben in der Warnungsliste sortieren und filtern. Um nach Bezeichnung zu filtern, klicke alternativ auf eine einer Warnung zugewiesene Bezeichnung, sodass dieser Filter automatisch auf die Warnungsliste angewendet wird.
Die Suchleiste ermöglicht auch die Volltextsuche für Warnungen und verwandte Sicherheitsempfehlungen. Du kannst nach einem Teil des Namens einer Sicherheitsempfehlung oder nach einer Beschreibung suchen, um die Warnungen in deinem Repository zurückzugeben, die sich auf diese Sicherheitsempfehlung beziehen. Beispielsweise gibt die Suche nach yaml.load() API could execute arbitrary code Dependabot alerts im Zusammenhang mit PyYAML insecurely deserializes YAML strings leading to arbitrary code execution (Die PyYAML-Deserialisierung von YAML-Zeichenfolgen ist unsicher und führt zu einer beliebigen Codeausführung) zurück, da die Suchzeichenfolge in der Beschreibung der Empfehlung vorkommt.

Unterstützte Ökosysteme und Manifeste für abhängigkeitsbezogene Bereiche
In der folgenden Tabelle ist zusammengefasst, ob der Abhängigkeitsbereich für verschiedene Ökosysteme und Manifeste unterstützt wird, d.h. ob Dependabot erkennen kann, ob eine Abhängigkeit für die Entwicklung oder Produktion verwendet wird.
| Sprache | Ökosystem | Manifestdatei | Unterstützter Abhängigkeitsbereich |
|---|---|---|---|
| Dart | pub | pubspec.yaml | |
| Dart | pub | pubspec.lock | |
| JavaScript | npm | package.json | |
| JavaScript | npm | package-lock.json | |
| PHP | Composer | composer.json | |
| PHP | Composer | composer.lock | |
| Python | Poetry | poetry.lock | |
| Python | Poetry | pyproject.toml | |
| Python | pip | requirements.txt | Bereich ist Entwicklung, wenn der Dateiname test oder dev enthält, sonst ist es Laufzeit |
| Python | pip | pipfile.lock | |
| Python | pip | pipfile | |
| Ruby | RubyGems | Gemfile | |
| Ruby | RubyGems | Gemfile.lock | Nein, standardmäßig auf Laufzeit |
| Rust | Cargo | Cargo.toml | |
| Rust | Cargo | Cargo.lock | Nein, standardmäßig auf Laufzeit |
| YAML | GitHub Actions | - | Nein, standardmäßig auf Laufzeit |
| .NET (C#, F#, VB usw.) | NuGet | .csproj / .vbproj .vcxproj / .fsproj | Nein, standardmäßig auf Laufzeit |
| .NET | NuGet | packages.config | Nein, standardmäßig auf Laufzeit |
| .NET | NuGet | .nuspec | Wenn die Registerkarte != runtime |
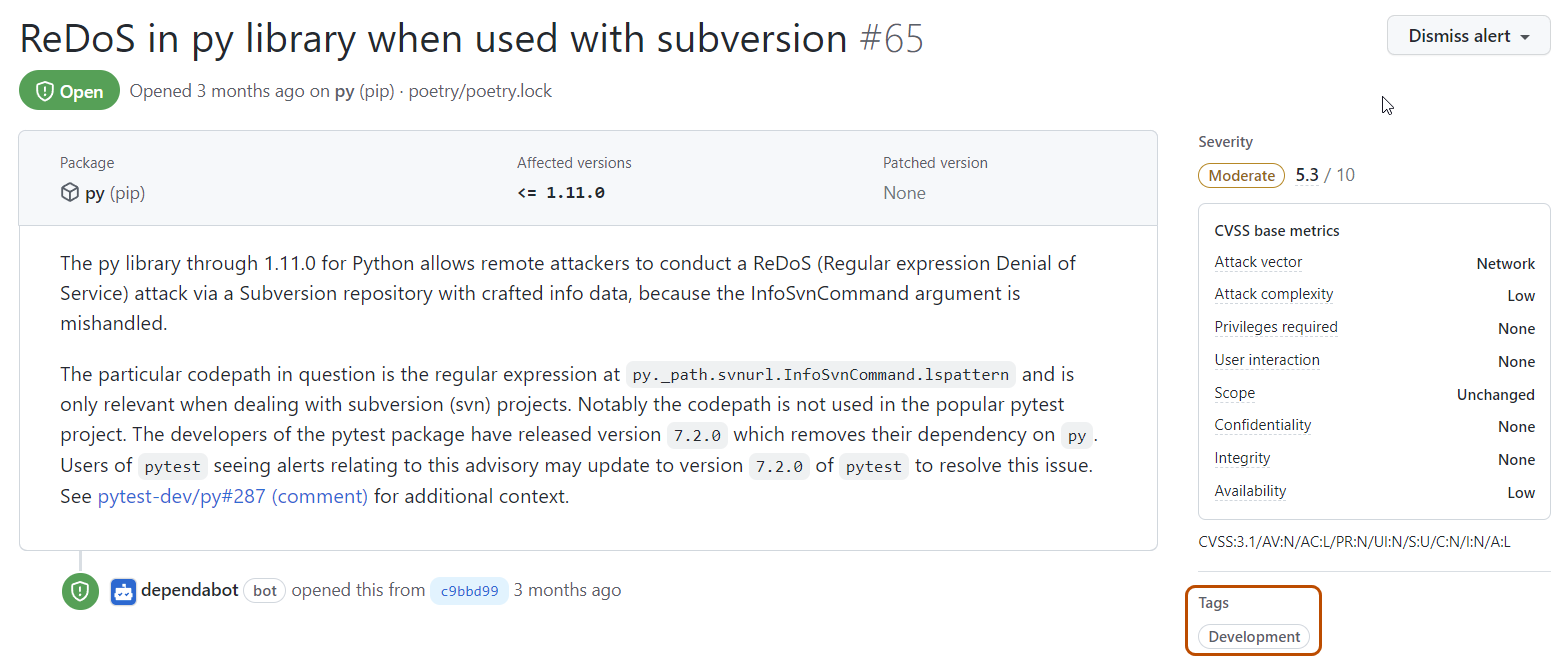
Warnungen für Pakete, die als Entwicklungsabhängigkeiten aufgeführt sind, werden mit der Bezeichnung Development auf der Dependabot alerts-Seite markiert und sind auch für die Filterung über den scope-Filter verfügbar.

Die Seite „Warnungsdetails“ von Warnungen in entwicklungsbezogenen Paketen zeigt einen Abschnitt „Tags“, der eine Development-Bezeichnung enthält.
Informationen zur Erkennung von Aufrufen anfälliger Funktionen
Hinweise:
- Die Ermittlung von Aufrufen anfälliger Funktionen durch Dependabot ist als Betaversion verfügbar. Änderungen sind vorbehalten.
- Die Erkennung anfälliger Aufrufe ist für öffentliche Repositorys aktiviert. Diese Analyse ist auch in privaten Repositorys verfügbar, die Organisationen gehören, die GitHub Enterprise Cloud verwenden und über eine Lizenz für GitHub Advanced Security verfügen. Weitere Informationen findest du unter Informationen zu GitHub Advanced Security.
Wenn Dependabot dich darauf hinweist, dass dein Repository eine anfällige Abhängigkeit verwendet, musst du herausfinden, um welche anfälligen Funktionen es sich handelt, und du musst überprüfen, ob du sie verwendest. Sobald du über diese Informationen verfügst, kannst du bestimmen, wie wichtig ein Upgrade auf eine sichere Version der Abhängigkeit ist.
Für unterstützte Sprachen erkennt Dependabot automatisch, ob du eine anfällige Funktion verwendest und kennzeichnet betroffene Warnmeldungen mit dem Hinweis „Anfälliger Aufruf“. Du kannst diese Informationen in der Dependabot alerts-Ansicht verwenden, um Maßnahmen zur Problementschärfung besser bewerten und priorisieren zu können.
Hinweis: Während der Betaphase ist dieses Feature nur für neue Python-Empfehlungen verfügbar, die nach dem 14. April 2022 erstellt wurden, sowie für eine Teilmenge der historischen Python-Empfehlungen. GitHub arbeitet daran, die Daten für weitere historische Python-Empfehlungen zu ergänzen, die laufend hinzugefügt werden. Anfällige Aufrufe werden nur auf den Dependabot alerts-Seiten hervorgehoben.
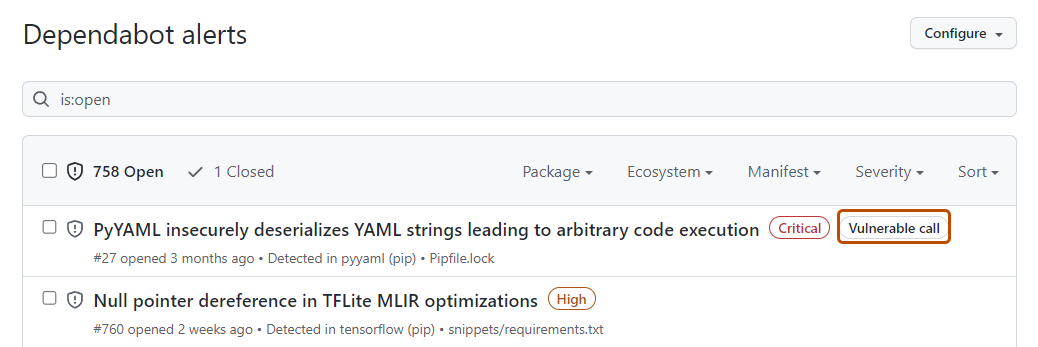
Du kannst die Ansicht so filtern, dass nur Warnungen angezeigt werden, bei denen Dependabot mindestens einen Aufruf einer anfälligen Funktion erkannt hat, indem du den Filter has:vulnerable-calls im Suchfeld verwendest.
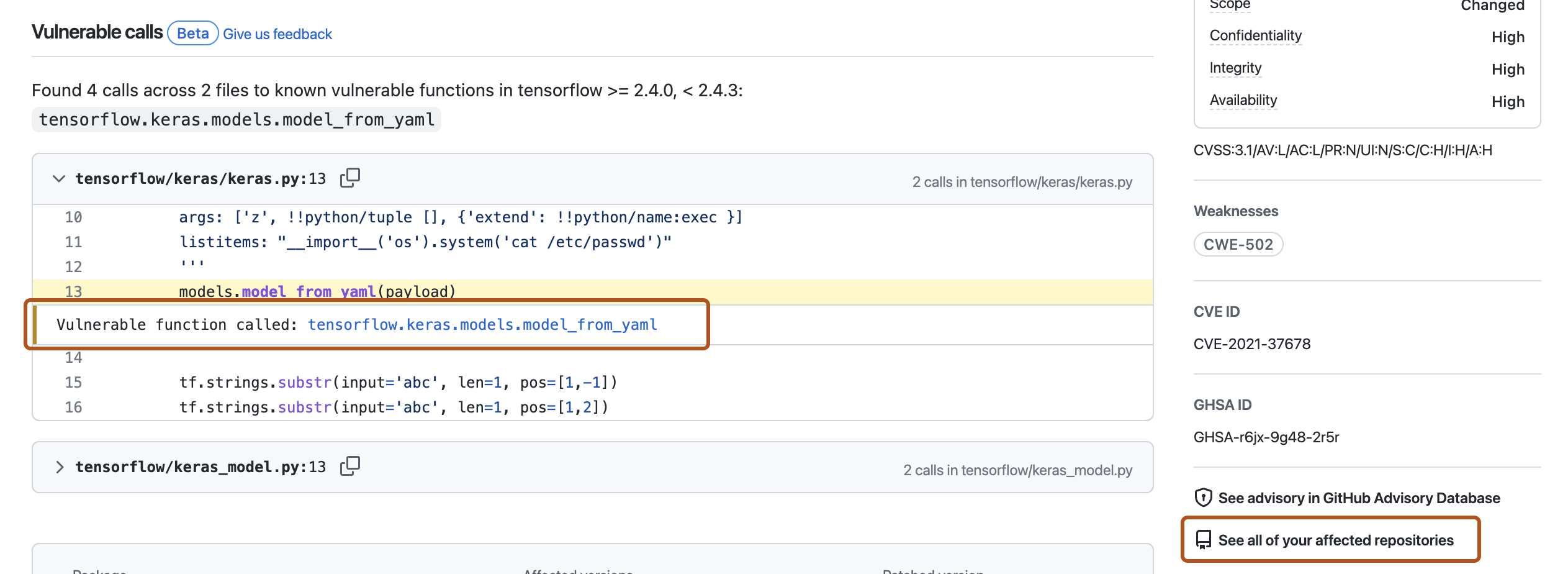
Für Warnungen, bei denen anfällige Aufrufe erkannt wurden, werden auf der Seite mit den Warnungsdetails zusätzliche Informationen angezeigt:
- Mindestens ein Codeblock, der zeigt, wo die Funktion verwendet wird.
- Eine Anmerkung, die die Funktion selbst auflistet, mit einem Link zu der Zeile, in der die Funktion aufgerufen wird.
Weitere Informationen findest du unter Überprüfen und Beheben von Warnungen.
Anzeige von Dependabot alerts
Sie können alle offenen und geschlossenen Dependabot alerts und entsprechenden Dependabot security updates im Dependabot alerts-Reiter Ihres Repositorys sehen. Sie können Dependabot alerts sortieren und filtern, indem Sie einen Filter aus dem Dropdown-Menü auswählen.
-
Navigiere auf GitHub.com zur Hauptseite des Repositorys.
-
Wähle unter dem Repositorynamen die Option Sicherheit aus. Wenn die Registerkarte „Sicherheit“ nicht angezeigt wird, wähle im Dropdownmenü die Option Sicherheit aus.

-
Klicke auf der Randleiste der Sicherheitsübersicht auf Dependabot . Wenn diese Option fehlt, bedeutet das, dass du keinen Zugriff auf die Sicherheitswarnungen hast und dir Zugriff gewährt werden muss. Weitere Informationen findest du unter Verwalten von Sicherheits- und Analyseeinstellungen für dein Repository.
-
Optional kannst du zum Filtern von Warnungen einen Filter in einem Dropdownmenü auswählen und dann auf den Filter klicken, den du anwenden möchtest. Du kannst Filter auch in die Suchleiste eingeben. Um nach Bezeichnung zu filtern, klicke alternativ auf eine einer Warnung zugewiesene Bezeichnung, sodass dieser Filter automatisch auf die Warnungsliste angewendet wird. Weitere Informationen zum Filtern und Sortieren von Warnungen findest du unter Priorisieren von Dependabot alerts.

-
Klicke auf die Warnung, die du anzeigen möchtest.
-
Wenn du optional eine Verbesserung der entsprechenden Sicherheitsempfehlung vorschlagen möchtest, klicke auf der rechten Seite mit den Warnungsdetails auf Vorschlagen von Verbesserungen für diese Empfehlung in GitHub Advisory Database . Weitere Informationen findest du unter Bearbeiten von Sicherheitshinweisen in GitHub Advisory Database.

Überprüfen und Beheben von Warnungen
Es ist wichtig, sicherzustellen, dass keine deiner Abhängigkeiten Sicherheitslücken aufweist. Wenn Dependabot Sicherheitsrisiken in deinen Abhängigkeiten erkennt, solltest du den Grad der Gefährdung deines Projekts einschätzen und festlegen, welche Maßnahmen zur Entschärfung du ergreifen musst, um deine Anwendung abzusichern.
Wenn eine gepatchte Version der Abhängigkeit verfügbar ist, kannst du einen Dependabot-Pull Request generieren, um die betroffene Abhängigkeit direkt aus einer Dependabot-Warnung zu aktualisieren. Wenn du Dependabot security updates aktiviert hast, kann der Pull Request in der Dependabot-Warnung verlinkt werden.
In Fällen, in denen keine gepatchte Version verfügbar ist oder du nicht auf die sichere Version aktualisieren kannst, stellt Dependabot zusätzliche Informationen zur Verfügung, damit du die nächsten Schritte festlegen kannst. Wenn du auf eine Dependabot-Warnung klickst, kannst du die vollständigen Details zur Sicherheitsempfehlung für die Abhängigkeit einschließlich der betroffenen Funktionen anzeigen. Du kannst dann überprüfen, ob dein Code die betroffenen Funktionen aufruft. Diese Informationen können dir helfen, den Gefährdungsgrad einzuschätzen und zu entscheiden, ob du das Risiko, das der Sicherheitshinweis angibt, in Kauf nehmen kannst oder nicht.
Für unterstützte Sprachen werden Aufrufe anfälliger Funktionen automatisch von Dependabot erkannt. Wenn du eine Warnung mit der Bezeichnung „Anfälliger Aufruf“ anzeigst, enthalten die Details den Namen der Funktion und einen Link zum Code, der sie aufruft. Häufig kannst du auf Grundlage dieser Informationen eine Entscheidung treffen, ohne dass weitere Untersuchungen durchgeführt werden müssen.
Beheben von anfälligen Abhängigkeiten
-
Sieh dir die Details zu einer Warnung an. Weitere Informationen findest du unter Anzeigen von Dependabot alerts weiter oben.
-
Wenn du Dependabot security updates aktiviert hast, gibt es möglicherweise einen Link zu einem Pull Request, der die Abhängigkeit behebt. Alternativ kannst du oben auf der Seite mit den Warnungsdetails auf Dependabot-Sicherheitsupdate erstellen klicken, um einen Pull Request zu erstellen.

-
(Optional) Falls du Dependabot security updates nicht verwendest, kannst du anhand der Informationen auf der Seite entscheiden, auf welche Version der Abhängigkeit du ein Upgrade durchführen möchtest und einen Pull Request erstellen, um die Abhängigkeit auf eine sichere Version zu aktualisieren.
-
Wenn du zum Aktualisieren deiner Abhängigkeit und zum Beheben deiner Schwachstelle bereit bist, führe den Merge für den Pull Request durch.
Jeder von Dependabot ausgelöste Pull Request enthält Informationen zu Befehlen, die Sie zum Steuern von Dependabot verwenden können. Weitere Informationen findest du unter Verwalten von Pull Requests für Abhängigkeitsupdates.
Schließen von Dependabot alerts
Tipp: Du kannst nur offene Warnungen verwerfen.
Wenn du umfangreiche Arbeiten zum Upgrade einer Abhängigkeit planst oder entscheidest, dass für eine Warnung keine Maßnahmen ergriffen werden müssen, kannst du die Warnung schließen. Durch das Schließen von bereits bewerteten Warnungen kannst du neue Warnungen leichter einordnen, sobald sie auftreten.
-
Sieh dir die Details zu einer Warnung an. Weitere Informationen findest du unter Anzeigen von anfälligen Abhängigkeiten (oben).
-
Wähle das Dropdownmenü „Schließen“ aus, und klicke auf einen Grund für das Schließen der Warnung. Nicht behobene geschlossene Warnungen können später erneut geöffnet werden. 1. Füge optional einen Kommentar hinzu. Der Kommentar zum Schließen wird der Zeitleiste der Warnung hinzugefügt und kann bei Prüfungen und Berichterstellungen als Begründung verwendet werden. Du kannst einen Kommentar über die GraphQL-API abrufen oder festlegen. Der Kommentar ist im Feld
dismissCommententhalten. Weitere Informationen findest du in der Dokumentation zur GraphQL-API unter Objects.
-
Klicke auf Warnung schließen.
Gleichzeitiges Verwerfen mehrerer Warnungen
- Zeige die geöffnete Dependabot alerts an. Weitere Informationen findest du unter Anzeigen und Aktualisieren von Dependabot-Warnungen.
- Filtere optional die Liste der Warnungen, indem du ein Dropdownmenü auswählst und dann auf den Filter klickst, den du anwenden möchtest. Du kannst Filter auch in die Suchleiste eingeben.
- Wähle links neben jedem Warnungstitel die Warnungen aus, die du verwerfen möchtest.

- Wähle optional oben in der Liste der Warnungen alle Warnungen auf der Seite aus.

- Wähle die Dropdownliste „Warnungen verwerfen“ aus, und klicke auf einen Grund zum Verwerfen der Warnungen.

Anzeigen und Aktualisieren von geschlossenen Warnungen
Du kannst alle geöffneten Warnungen anzeigen und Warnungen erneut öffnen, die zuvor geschlossen wurden. Geschlossene Warnungen, die bereits behoben wurden, können nicht erneut geöffnet werden.
-
Navigiere auf GitHub.com zur Hauptseite des Repositorys.
-
Wähle unter dem Repositorynamen die Option Sicherheit aus. Wenn die Registerkarte „Sicherheit“ nicht angezeigt wird, wähle im Dropdownmenü die Option Sicherheit aus.

-
Klicke auf der Randleiste der Sicherheitsübersicht auf Dependabot . Wenn diese Option fehlt, bedeutet das, dass du keinen Zugriff auf die Sicherheitswarnungen hast und dir Zugriff gewährt werden muss. Weitere Informationen findest du unter Verwalten von Sicherheits- und Analyseeinstellungen für dein Repository.

-
Klicke auf Geschlossen, um geschlossene Warnungen anzuzeigen.

-
Klicke auf die Warnung, die du anzeigen oder aktualisieren möchtest.
-
Alternativ kannst du auf Erneut öffnen klicken, wenn die Datei geschlossen wurde und du sie wieder öffnen möchtest. Warnungen, die bereits behoben wurden, können nicht erneut geöffnet werden.

Gleichzeitiges erneutes Öffnen mehrerer Warnungen
- Zeige die geschlossenen Dependabot alerts an. Weitere Informationen findest du weiter oben unter Anzeigen und Aktualisieren von Dependabot-Warnungen.
- Wähle links jedem neben Warnungstitel die Warnungen aus, die du erneut öffnen möchtest, indem du das Kontrollkästchen neben der jeweiligen Warnung aktivierst.
- Wähle optional oben in der Warnungsliste alle geschlossenen Warnungen auf der Seite aus.

- Klicke auf Erneut öffnen, um die Warnungen erneut zu öffnen. Warnungen, die bereits behoben wurden, können nicht erneut geöffnet werden.
Überprüfen der Überwachungsprotokolle für Dependabot alerts
Wenn ein Mitglied deiner Organisation eine Aktion im Zusammenhang mit Dependabot alerts ausführt, kannst du die Aktionen im Überwachungsprotokoll überprüfen. Weitere Informationen zum Zugriff auf das Protokoll findest du unter Auditprotokoll deiner Organisation überprüfen.

Ereignisse in deinem Überwachungsprotokoll für Dependabot alerts enthalten Details, z. B. wer die Aktion ausgeführt hat, was die Aktion war und wann die Aktion ausgeführt wurde. Das Ereignis enthält auch einen Link zur Warnung selbst. Wenn ein Mitglied deiner Organisation eine Warnung schließt, zeigt das Ereignis den Grund für die Schließung und den Kommentar an. Informationen zu den Dependabot alerts-Aktionen findest du in der repository_vulnerability_alert-Kategorie unter Überwachungsprotokollereignisse für deine Organisation.