Note
GitHub-hosted runners are not currently supported on GitHub Enterprise Server. You can see more information about planned future support on the GitHub public roadmap.
You can add a self-hosted runner to a repository, an organization, or an enterprise.
If you are an organization or enterprise administrator, you might want to add your self-hosted runners at the organization or enterprise level. This approach makes the runner available to multiple repositories in your organization or enterprise, and also lets you to manage your runners in one place.
For information on supported operating systems for self-hosted runners, or using self-hosted runners with a proxy server, see About self-hosted runners.
Warning
We recommend that you only use self-hosted runners with private repositories. This is because forks of your public repository can potentially run dangerous code on your self-hosted runner machine by creating a pull request that executes the code in a workflow.
For more information, see About self-hosted runners.
You can set up automation to scale the number of self-hosted runners. For more information, see Autoscaling with self-hosted runners.
You can register ephemeral runners that perform a single job before the registration is cleaned up by using just-in-time runner registration. For more information, see Security hardening for GitHub Actions.
Prerequisites
-
GitHub Actions must be enabled for GitHub Enterprise Server. A site administrator can enable and configure GitHub Actions for your instance. For more information, see Getting started with GitHub Actions for GitHub Enterprise Server.
-
You must have access to the machine you will use as a self-hosted runner in your environment.
- The connection between self-hosted runners and GitHub is over HTTP (port 80) or HTTPS (port 443). To ensure connectivity over HTTPS, configure TLS for GitHub Enterprise Server. For more information, see Configuring TLS.
Adding a self-hosted runner to a repository
You can add self-hosted runners to a single repository. To add a self-hosted runner to a user repository, you must be the repository owner. For an organization repository, you must be an organization owner, have admin access to the repository, or have the “Manage organization runners and runner groups” permission.
For more information about custom organization roles, see About custom organization roles.
For information about how to add a self-hosted runner with the REST API, see REST API endpoints for self-hosted runners.
Note
Enterprise owners and organization owners can choose which repositories are allowed to create repository-level self-hosted runners. Users with the “Manage organization runners and runner groups” permission can only choose which repositories are allowed to create repository-level self-hosted runners for repositories in your organization.
For more information about custom organization roles, see About custom organization roles.
For more information, see Enforcing policies for GitHub Actions in your enterprise and Disabling or limiting GitHub Actions for your organization.
-
On GitHub, navigate to the main page of the repository.
-
Under your repository name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.

-
In the left sidebar, click Actions, then click Runners.
-
Click New self-hosted runner.
-
Select the operating system image and architecture of your self-hosted runner machine.
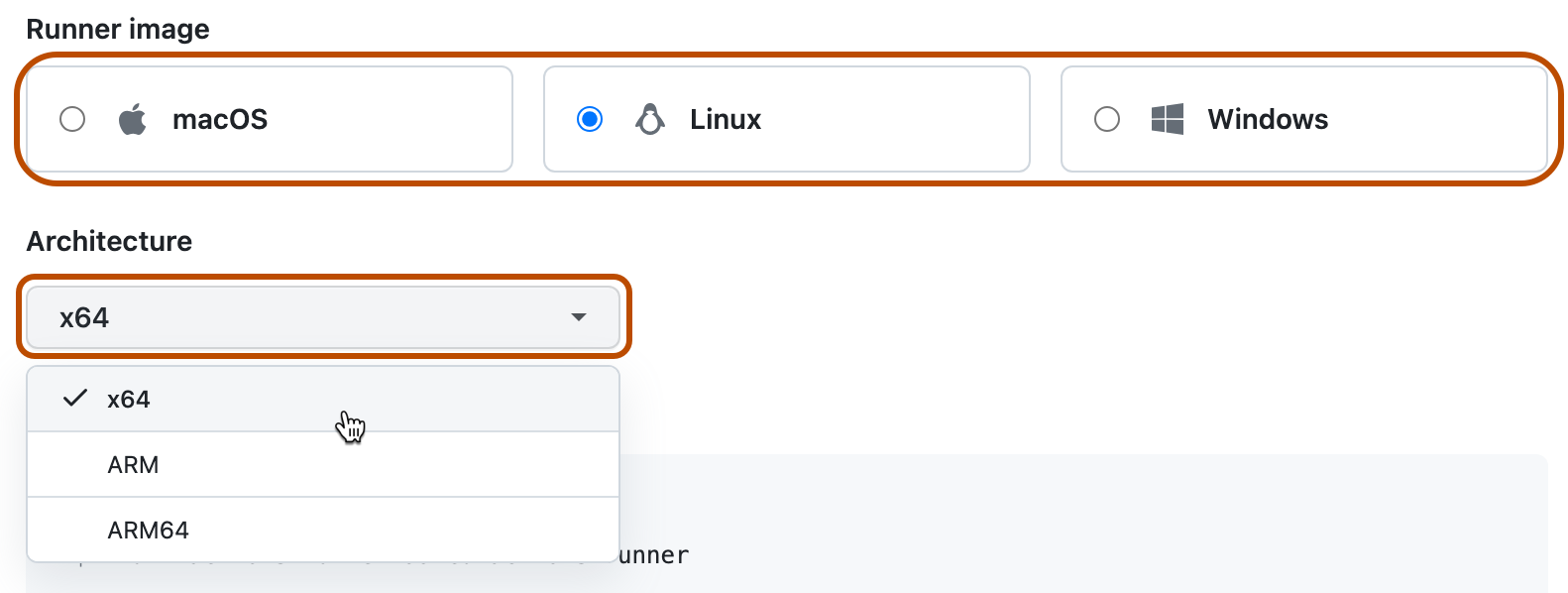
-
You will see instructions showing you how to download the runner application and install it on your self-hosted runner machine.
Open a shell on your self-hosted runner machine and run each shell command in the order shown.
Note
On Windows, if you want to install the self-hosted runner application as a service, you must open a shell with administrator privileges. We also recommend that you use
C:\actions-runneras the directory for the self-hosted runner application so that Windows system accounts can access the runner directory.The instructions walk you through completing these tasks:
- Downloading and extracting the self-hosted runner application.
- Running the
configscript to configure the self-hosted runner application and register it with GitHub Actions. Theconfigscript requires the destination URL and an automatically-generated time-limited token to authenticate the request. The token expires after one hour.- On Windows, the
configscript also asks if you would like to install the self-hosted runner application as a service. For Linux and macOS, you can install a service after you finish adding the runner. For more information, see Configuring the self-hosted runner application as a service.
- On Windows, the
- Running the self-hosted runner application to connect the machine to GitHub Actions.
Checking that your self-hosted runner was successfully added
After completing the steps to add a self-hosted runner, the runner and its status are now listed under "Self-hosted runners".
The self-hosted runner application must be active for the runner to accept jobs. When the runner application is connected to GitHub and ready to receive jobs, you will see the following message on the machine's terminal.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Adding a self-hosted runner to an organization
You can add self-hosted runners at the organization level, where they can be used to process jobs for multiple repositories in an organization. To add a self-hosted runner to an organization, you must be an organization owner or have the "Manage organization runners and runner groups" permission. For information about how to add a self-hosted runner with the REST API, see REST API endpoints for self-hosted runners.
For more information about custom organization roles, see About custom organization roles.
-
On GitHub, navigate to the main page of the organization.
-
Under your organization name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.

-
In the left sidebar, click Actions, then click Runners.
-
Click New runner.
-
Select the operating system image and architecture of your self-hosted runner machine.

-
You will see instructions showing you how to download the runner application and install it on your self-hosted runner machine.
Open a shell on your self-hosted runner machine and run each shell command in the order shown.
Note
On Windows, if you want to install the self-hosted runner application as a service, you must open a shell with administrator privileges. We also recommend that you use
C:\actions-runneras the directory for the self-hosted runner application so that Windows system accounts can access the runner directory.The instructions walk you through completing these tasks:
- Downloading and extracting the self-hosted runner application.
- Running the
configscript to configure the self-hosted runner application and register it with GitHub Actions. Theconfigscript requires the destination URL and an automatically-generated time-limited token to authenticate the request. The token expires after one hour.- On Windows, the
configscript also asks if you would like to install the self-hosted runner application as a service. For Linux and macOS, you can install a service after you finish adding the runner. For more information, see Configuring the self-hosted runner application as a service.
- On Windows, the
- Running the self-hosted runner application to connect the machine to GitHub Actions.
Checking that your self-hosted runner was successfully added
After completing the steps to add a self-hosted runner, the runner and its status are now listed under "Self-hosted runners".
The self-hosted runner application must be active for the runner to accept jobs. When the runner application is connected to GitHub and ready to receive jobs, you will see the following message on the machine's terminal.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Note
For security reasons, public repositories can't use runners in a runner group by default, but you can override this in the runner group's settings. For more information, see Managing access to self-hosted runners using groups.
Adding a self-hosted runner to an enterprise
You can add self-hosted runners to an enterprise, where they can be assigned to multiple organizations. The organization owner can control which repositories can use it.
New runners are assigned to the default group. You can modify the runner's group after you've registered the runner. For more information, see Managing access to self-hosted runners using groups.
To add a self-hosted runner to an enterprise, you must be an enterprise owner. For information about how to add a self-hosted runner with the REST API, see the enterprise endpoints in the GitHub Actions REST API.
-
In the top-right corner of GitHub Enterprise Server, click your profile photo, then click Enterprise settings.

-
On the left side of the page, in the enterprise account sidebar, click Policies.
-
Under " Policies", click Actions.
-
Click the Runners tab.
-
Click New runner.
-
Select the operating system image and architecture of your self-hosted runner machine.

-
You will see instructions showing you how to download the runner application and install it on your self-hosted runner machine.
Open a shell on your self-hosted runner machine and run each shell command in the order shown.
Note
On Windows, if you want to install the self-hosted runner application as a service, you must open a shell with administrator privileges. We also recommend that you use
C:\actions-runneras the directory for the self-hosted runner application so that Windows system accounts can access the runner directory.The instructions walk you through completing these tasks:
- Downloading and extracting the self-hosted runner application.
- Running the
configscript to configure the self-hosted runner application and register it with GitHub Actions. Theconfigscript requires the destination URL and an automatically-generated time-limited token to authenticate the request. The token expires after one hour.- On Windows, the
configscript also asks if you would like to install the self-hosted runner application as a service. For Linux and macOS, you can install a service after you finish adding the runner. For more information, see Configuring the self-hosted runner application as a service.
- On Windows, the
- Running the self-hosted runner application to connect the machine to GitHub Actions.
Checking that your self-hosted runner was successfully added
After completing the steps to add a self-hosted runner, the runner and its status are now listed under "Self-hosted runners".
The self-hosted runner application must be active for the runner to accept jobs. When the runner application is connected to GitHub and ready to receive jobs, you will see the following message on the machine's terminal.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Note
For security reasons, public repositories can't use runners in a runner group by default, but you can override this in the runner group's settings. For more information, see Managing access to self-hosted runners using groups.
Making enterprise runners available to repositories
By default, runners in an enterprise's "Default" self-hosted runner group are available to all organizations in the enterprise, but are not available to all repositories in each organization.
To make an enterprise-level self-hosted runner group available to an organization repository, you might need to change the organization's inherited settings for the runner group to make the runner available to repositories in the organization.
For more information on changing runner group access settings, see Managing access to self-hosted runners using groups.