Toute personne disposant d’une autorisation de lecture pour un dépôt peut voir les annotations d’code scanning sur les demandes de tirage (pull request). Pour plus d’informations, consultez « Triage des alertes d’analyse du code dans les demandes de tirage (pull request) ».
Affichage des alertes pour un dépôt
Vous avez besoin d’une autorisation d’écriture pour voir un récapitulatif de toutes les alertes d’un dépôt sous l’onglet Sécurité.
Par défaut, la page d'alertes code scanning est filtrée pour afficher les alertes pour la branche par défaut du référentiel uniquement.
-
Sur GitHub, accédez à la page principale du référentiel.
-
Sous le nom du dépôt, cliquez sur Sécurité. Si vous ne voyez pas l’onglet « Sécurité », sélectionnez le menu déroulant et cliquez sur Sécurité.

-
Dans la barre latérale gauche, cliquez sur Code scanning.
-
Si vous le souhaitez, utilisez la zone de recherche en texte libre ou les menus déroulants pour filtrer les alertes. Par exemple, vous pouvez filtrer en fonction de l’outil utilisé pour identifier les alertes.
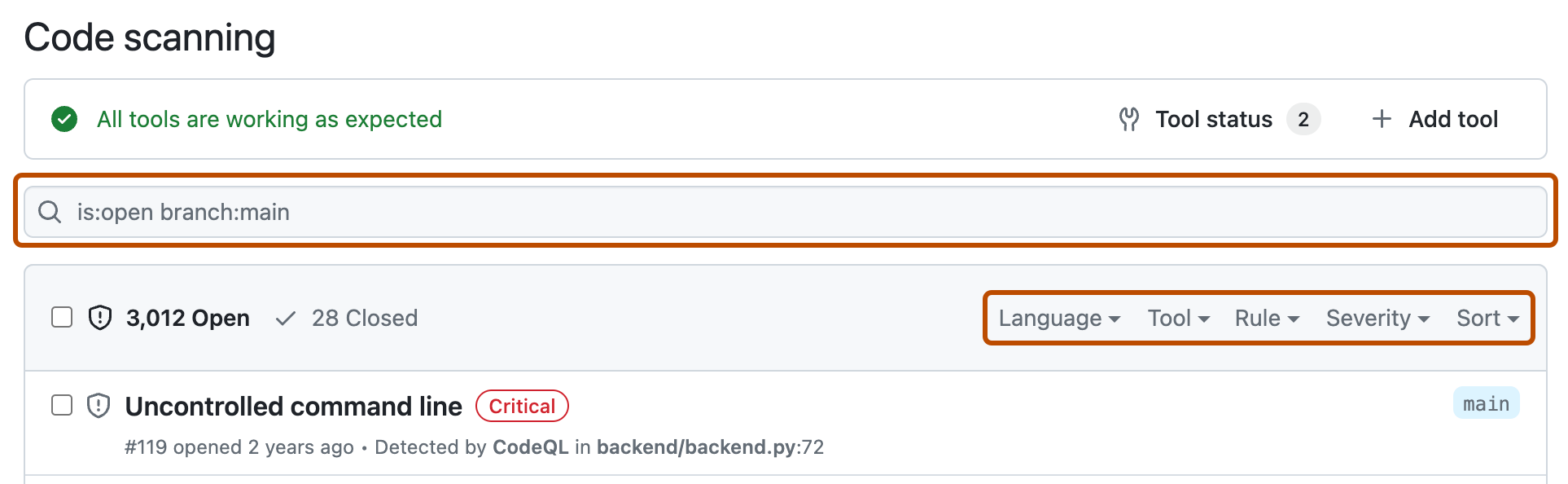
-
Sous « Code scanning », cliquez sur l’alerte à explorer pour afficher la page de l’alerte détaillée. L’état et les détails présentés sur la page de l’alerte reflètent uniquement l’état de l’alerte sur la branche par défaut du référentiel, même si l’alerte existe sur d’autres branches. Vous pouvez consulter l’état de l’alerte sur les branches autres que la branche par défaut dans la section Branches affectées sur le côté droit de la page de l’alerte. Si une alerte n’existe pas sur la branche par défaut, l’état de l’alerte est « dans la demande de tirage » ou « dans la branche », et il est grisé. La section Développement affiche les branches liées et les demandes de tirage qui permettront de corriger l’alerte.
-
Si l’alerte met en évidence un problème avec le flux de données, vous pouvez cliquer sur Afficher les chemins pour afficher le chemin depuis la source de données vers le récepteur où il est utilisé.

-
Les alertes de l’analyse CodeQL incluent une description du problème. Cliquez sur Afficher plus pour obtenir des conseils sur la façon de corriger votre code.
Pour plus d’informations, consultez « À propos des alertes d’analyse du code ».
Remarque
Vous pouvez voir des informations sur la date de la dernière exécution de l’code scanning dans la page d’état de l’outil. Pour plus d’informations, consultez « À propos de la page d’état de l’outil pour l’analyse du code ».
Demander à GitHub Copilot Chat des informations sur les alertes code scanning
Avec une licence GitHub Copilot Enterprise, vous pouvez demander de l’aide à Copilot Chat pour mieux comprendre les alertes de sécurité, y compris les alertes code scanning, dans les référentiels de votre organisation. Pour plus d’informations, consultez « Poser des questions à GitHub Copilot dans GitHub ».
Affichage des métriques pour les alertes de demandes de tirage (pull requests) CodeQL pour une organisation
Pour les alertes code scanning de l'analyse CodeQL, vous pouvez utiliser la vue d'ensemble de la sécurité pour voir comment CodeQL se comporte dans les demandes de tirage dans les référentiels où vous avez un accès en écriture dans votre organisation, et pour identifier les référentiels où vous pourriez avoir besoin de prendre des mesures. Pour plus d’informations, consultez « Affichage des métriques pour les alertes de demande de tirage ».
Filtrage des alertes d’code scanning
Vous pouvez filtrer les alertes affichées dans la vue des alertes d’code scanning. Cela est utile s’il existe de nombreuses alertes, car vous pouvez vous concentrer sur un type particulier d’alerte. Vous disposez de filtres prédéfinis et d’un éventail de mots clés pour affiner la liste des alertes affichées.
Lorsque vous sélectionnez un mot clé dans une liste déroulante ou lorsque vous entrez une mot clé dans le champ de recherche, seules les valeurs avec des résultats s’affichent. Vous évitez ainsi plus facilement de définir des filtres qui ne trouvent aucun résultat.

Si vous entrez plusieurs filtres, l’affichage montre les alertes correspondant à tous ces filtres. Par exemple, is:closed severity:high branch:main affiche uniquement les alertes de gravité élevée fermées qui sont présentes sur la branche main. L’exception concerne les filtres relatifs aux références (ref, branch et pr) : is:open branch:main branch:next vous montre les alertes ouvertes à la fois sur la branche main et sur la branche next.
Veuillez noter que si vous avez filtré les alertes sur une branche autre que celle par défaut, mais que les mêmes alertes existent sur la branche par défaut, la page d’une alerte donnée reflétera uniquement l’état de l’alerte sur la branche par défaut, même si cet état est en conflit avec celui d’une branche autre que celle par défaut. Par exemple, une alerte qui apparaît dans la liste « Ouvertes » dans le résumé des alertes de la branch-x peut présenter l’état « Résolue » sur la page de l’alerte, si l’alerte est déjà résolue sur la branche par défaut. Vous pouvez consulter l’état de l’alerte pour la branche filtrée dans la section Branches affectées sur le côté droit de la page de l’alerte.
Vous pouvez préfixer le filtre tag avec - pour exclure les résultats ayant cette étiquette. Par exemple, -tag:style affiche uniquement les alertes qui n’ont pas la balise style.
Restriction des résultats au code d’application uniquement
Vous pouvez utiliser le filtre « Uniquement les alertes dans le code d’application » ou la paire mot clé/valeur autofilter:true pour restreindre les résultats aux alertes dans le code d’application. Pour plus d’informations sur les types de code qui sont automatiquement étiquetés comme n’étant pas du code d’application, consultez À propos des alertes d’analyse du code.
Exploration des alertes d’code scanning
Vous pouvez explorer la liste des alertes. Cela est utile s’il existe un grand nombre d’alertes dans votre dépôt ou si vous ne connaissez pas le nom exact d’une alerte, par exemple. GitHub effectue la recherche en texte libre dans les éléments suivants :
- Nom de l'alerte
- Détails de l’alerte (comprenant aussi les informations masquées par défaut dans la section réductible Afficher plus)
| Recherche prise en charge | Exemple de syntaxe | Résultats |
|---|---|---|
| Recherche avec un seul mot | injection | Retourne toutes les alertes contenant le mot injection |
| Recherche avec plusieurs mots | sql injection | Retourne toutes les alertes contenant sql ou injection |
| Recherche de correspondance exacte (utilisez des guillemets doubles) | "sql injection" | Retourne toutes les alertes contenant l’expression exacte sql injection |
| Recherche OU | sql OR injection | Retourne toutes les alertes contenant sql ou injection |
| Recherche ET | sql AND injection | Retourne toutes les alertes contenant à la fois les mots sql et injection |
Conseil
- La recherche avec sur plusieurs mots équivaut à une recherche OU.
- La recherche ET retourne des résultats dans lesquels les termes de recherche se trouvent n’importe où, dans n’importe quel ordre dans le nom ou les détails de l’alerte.
- Sur GitHub, accédez à la page principale du référentiel.
- Sous le nom du dépôt, cliquez sur Sécurité. Si vous ne voyez pas l’onglet « Sécurité », sélectionnez le menu déroulant et cliquez sur Sécurité.

- Dans la barre latérale gauche, cliquez sur Code scanning.
- À droite des menus déroulants Filtres, tapez les mots clés à rechercher dans la zone de recherche en texte libre.

- Appuyez sur Entrée. La liste des alertes contient les alertes d’code scanning ouvertes correspondant à vos critères de recherche.
Audit des réponses aux alertes d’code scanning
Vous pouvez auditer les actions effectuées en réponse aux alertes code scanning à l’aide des outils GitHub. Pour plus d’informations, consultez « Audit des alertes de sécurité ».