About problems with SAML authentication
GitHub Enterprise Server logs error messages for failed SAML authentication in the authentication log at /var/log/github/auth.log. You can review responses in this log file, and you can also configure more verbose logging.
For more information about SAML response requirements, see "SAML configuration reference."
Configuring SAML debugging
You can configure GitHub Enterprise Server to write verbose debug logs to /var/log/github/auth.log for every SAML authentication attempt. You may be able to troubleshoot failed authentication attempts with this extra output.
Warnings:
- Only enable SAML debugging temporarily, and disable debugging immediately after you finish troubleshooting. If you leave debugging enabled, the size of your log may increase much faster than usual, which can negatively impact the performance of GitHub Enterprise Server.
- Test new authentication settings for your GitHub Enterprise Server instance in a staging environment before you apply the settings in your production environment. For more information, see "Setting up a staging instance."
-
在 GitHub Enterprise Server 的右上角,单击� 的个人资料照片,然后单击“企业设置”。
-
在企业边� �中,单击 “策略”。

-
在 “策略” 下,单击“选项” 。
-
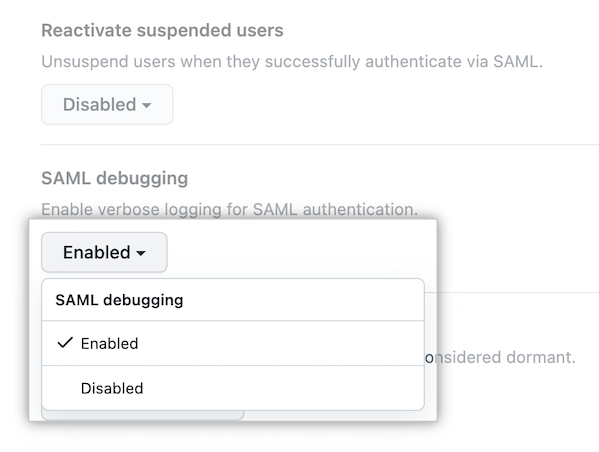
Under "SAML debugging", select the drop-down and click Enabled.
-
Attempt to sign into your GitHub Enterprise Server instance through your SAML IdP.
-
Review the debug output in /var/log/github/auth.log on your GitHub Enterprise Server instance.
-
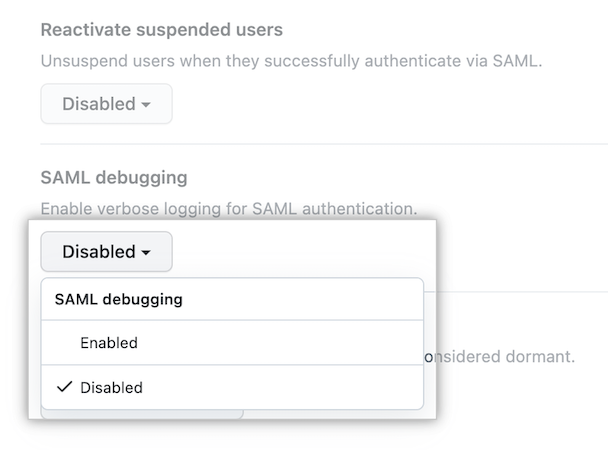
When you're done troubleshooting, select the drop-down and click Disabled.
Decoding responses in auth.log
Some output in auth.log may be Base64-encoded. You can access the administrative shell and use the base64 utility on your GitHub Enterprise Server instance to decode these responses. For more information, see "Accessing the administrative shell (SSH)."
$ base64 --decode ENCODED_OUTPUTError: "Another user already owns the account"
When a user signs into your GitHub Enterprise Server instance for the first time with SAML authentication, GitHub Enterprise Server creates a user account on the instance and maps the SAML NameID to the account.
When the user signs in again, GitHub Enterprise Server compares the account's NameID mapping to the IdP's response. If the NameID in the IdP's response no longer matches the NameID that GitHub Enterprise Server expects for the user, the sign-in will fail. The user will see the following message.
Another user already owns the account. Please have your administrator check the authentication log.
The message typically indicates that the person's username or email address has changed on the IdP. Ensure that the NameID mapping for the user account on GitHub Enterprise Server matches the user's NameID on your IdP. For more information, see "Updating a user's SAML NameID."
Error: Recipient in SAML response was blank or not valid
If the Recipient does not match the ACS URL for your GitHub Enterprise Server instance, one of the following two error messages will appear in the authentication log when a user attempts to authenticate.
Recipient in the SAML response must not be blank.
Recipient in the SAML response was not valid.
Ensure that you set the value for Recipient on your IdP to the full ACS URL for your GitHub Enterprise Server instance. For example, https://ghe.corp.example.com/saml/consume.
Error: "SAML Response is not signed or has been modified"
If your IdP does not sign the SAML response, or the signature does not match the contents, the following error message will appear in the authentication log.
SAML Response is not signed or has been modified.
Ensure that you configure signed assertions for the GitHub Enterprise Server application on your IdP.
Error: "Audience is invalid" or "No assertion found"
If the IdP's response has a missing or incorrect value for Audience, the following error message will appear in the authentication log.
Audience is invalid. Audience attribute does not match https://<em>YOUR-INSTANCE-URL</em>
Ensure that you set the value for Audience on your IdP to the EntityId for your GitHub Enterprise Server instance, which is the full URL to your instance. For example, https://ghe.corp.example.com.
错误:“当前时间早于 NotBefore 条件”
当 IdP 与 GitHub Enterprise Server 之间的时间差太大时可能会发生此错误,这通常发生在自托管 IdP 中。
为防止此问题,我们建议将设备指向与 IdP 相同的网络时间协议 (NTP) 源(如果可能)。 如果遇到此错误,请确保 设备 上的时间与 NTP 服务器正确同步。
如果使用 ADFS 作为 IdP,则对于 GitHub,也将 ADFS 中的 NotBeforeSkew 设置为 1 分钟。 如果 NotBeforeSkew 设置为 0,即使非常小的时间差(包括� 毫秒)也会导致身份验证问题。