About SAML SSO
SAML SSO allows you to centrally control and secure access to your GitHub Enterprise Server instance from your SAML IdP. When an unauthenticated user visits your GitHub Enterprise Server instance in a browser, GitHub Enterprise Server will redirect the user to your SAML IdP to authenticate. After the user successfully authenticates with an account on the IdP, the IdP redirects the user back to your GitHub Enterprise Server instance. GitHub Enterprise Server validates the response from your IdP, then grants access to the user.
After a user successfully authenticates on your IdP, the user's SAML session for your GitHub Enterprise Server instance is active in the browser for 24 hours. After 24 hours, the user must authenticate again with your IdP.
如果将某个用户从 IdP 中移除,还必须手动挂起他们。 否则,帐户的所有者可以继续使用访问令牌或 SSH 密钥进行身份验证。 有关详细信息,请参阅“挂起和取消挂起用户”。
Supported identity providers
GitHub Enterprise Server 支持 SAML SSO 与采用 SAML 2.0 � �准的 IdP 一起使用。 有关详细信息,请参阅 OASIS 网站上的 SAML Wiki。
GitHub 官方支持和内部测试以下 IdP。
- Active Directory 联合身份验证服务 (AD FS)
- Azure Active Directory (Azure AD)
- Okta
- OneLogin
- PingOne
- Shibboleth
Configuring SAML SSO
You can enable or disable SAML authentication for your GitHub Enterprise Server instance, or you can edit an existing configuration. You can view and edit authentication settings for GitHub Enterprise Server in the management console. For more information, see "Accessing the management console."
Note: GitHub strongly recommends that you verify any new configuration for authentication in a staging environment. An incorrect configuration could result in downtime for your GitHub Enterprise Server instance. For more information, see "Setting up a staging instance."
-
从 GitHub Enterprise Server 上的管理帐户任意页面的右上角,单击 。
-
如果� 尚未在“站点管理员”页上,请在左上角单击“站点管理员”。
-
在左侧边� �中,单击“管理控制台”。
-
在左侧边� �中,单击“身份验证”。
-
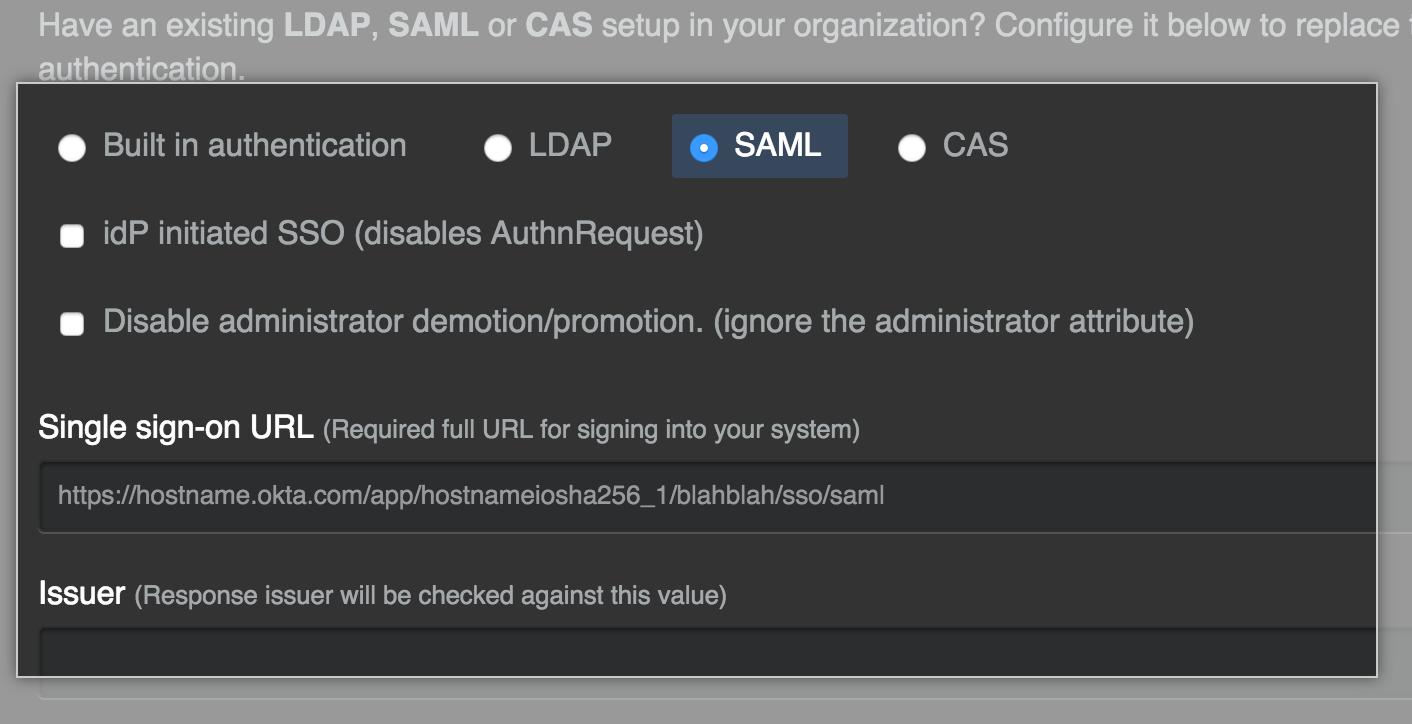
Select SAML.
-
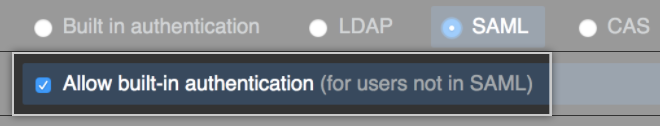
(可选)若要允许外部身份验证系统上没有帐户的人员使用内置身份验证登录,请选择“允许内置身份验证”。 有关详细信息,请参阅“允许对提供者外部的用户使用内置身份验证”。
-
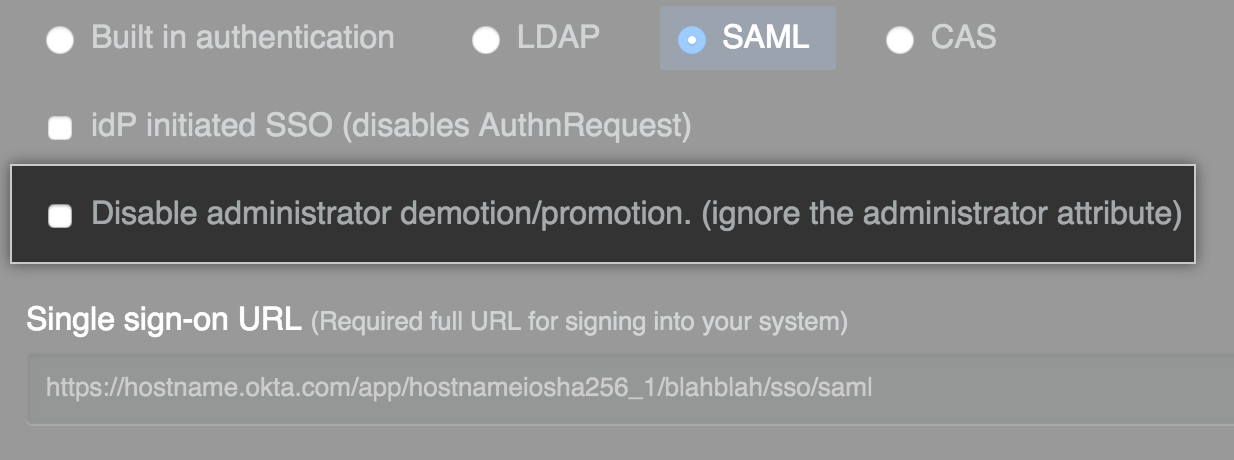
Optionally, to enable unsolicited response SSO, select IdP initiated SSO. By default, GitHub Enterprise Server will reply to an unsolicited Identity Provider (IdP) initiated request with an
AuthnRequestback to the IdP.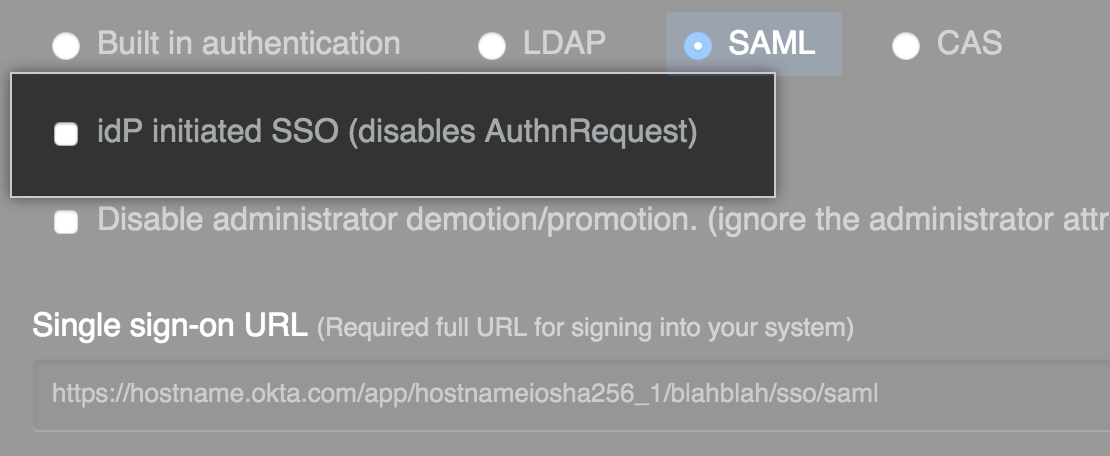
Note: We recommend keeping this value unselected. You should enable this feature only in the rare instance that your SAML implementation does not support service provider initiated SSO, and when advised by GitHub Enterprise 支持.
-
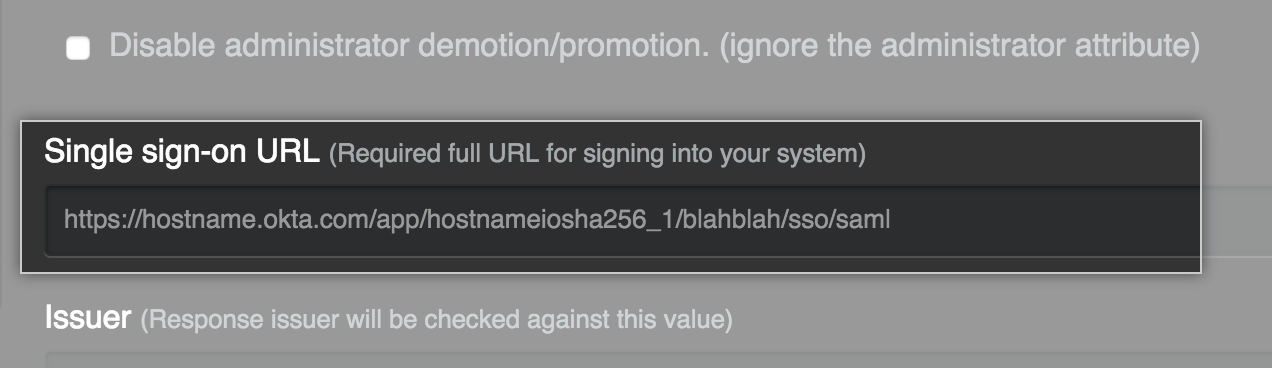
Select Disable administrator demotion/promotion if you do not want your SAML provider to determine administrator rights for users on your GitHub Enterprise Server instance.
-
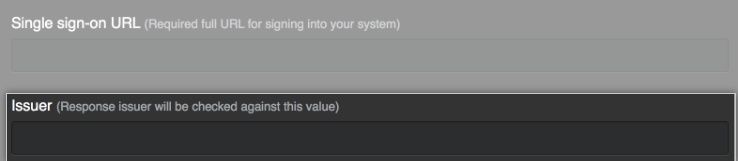
In the Single sign-on URL field, type the HTTP or HTTPS endpoint on your IdP for single sign-on requests. This value is provided by your IdP configuration. If the host is only available from your internal network, you may need to configure your GitHub Enterprise Server instance to use internal nameservers.
-
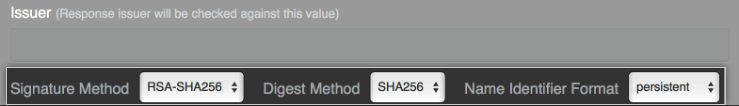
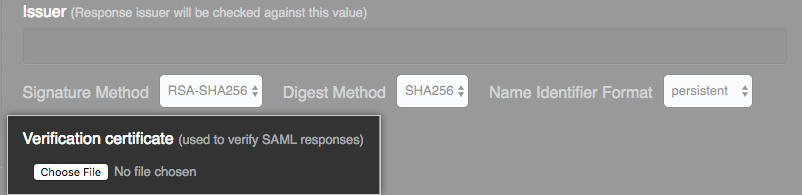
Optionally, in the Issuer field, type your SAML issuer's name. This verifies the authenticity of messages sent to your GitHub Enterprise Server instance.
-
In the Signature Method and Digest Method drop-down menus, choose the hashing algorithm used by your SAML issuer to verify the integrity of the requests from your GitHub Enterprise Server instance. Specify the format with the Name Identifier Format drop-down menu.
-
Under Verification certificate, click Choose File and choose a certificate to validate SAML responses from the IdP.
-
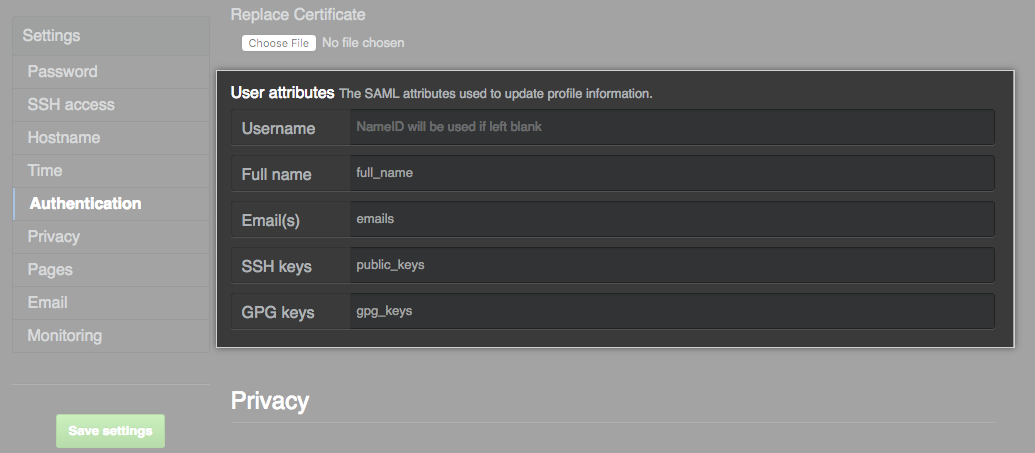
Modify the SAML attribute names to match your IdP if needed, or accept the default names.