About management of security and analysis settings
GitHub can help secure the repositories in your organization. You can manage the security and analysis features for all existing or new repositories that members create in your organization.
Displaying the security and analysis settings
-
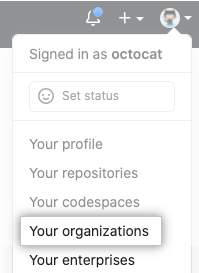
在 GitHub Enterprise Server 的右上角,单击您的头像,然后单击 Your organizations(您的组织)。
-
在组织旁边,单击 Settings(设置)。

-
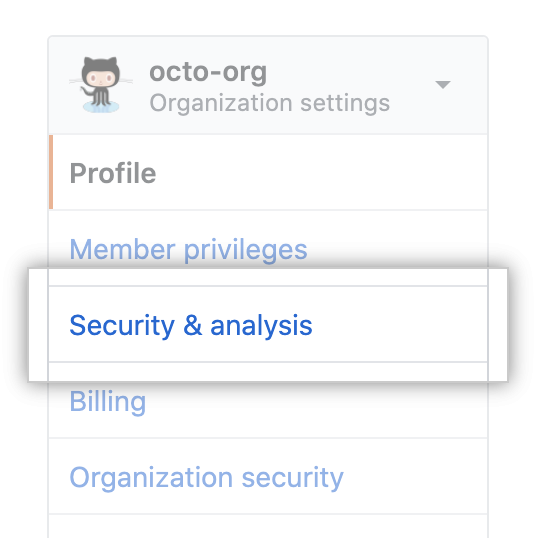
在左侧边� �中,单击 Security & analysis(安全和分析)。
The page that's displayed allows you to enable or disable all security and analysis features for the repositories in your organization.
If you have a license for GitHub Advanced Security, the page will also contain options to enable and disable Advanced Security features. Any repositories that use GitHub Advanced Security are listed at the bottom of the page.
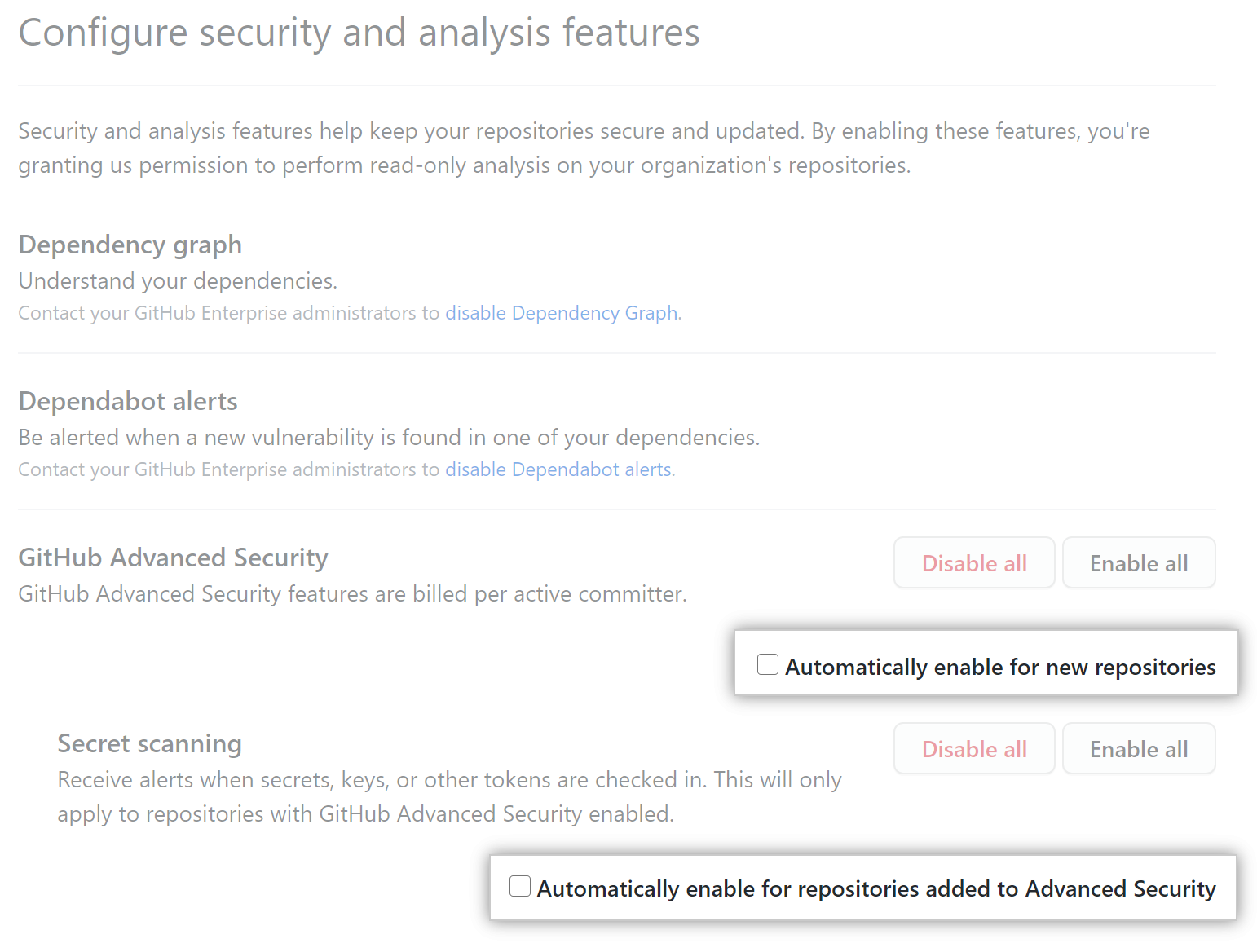
Enabling or disabling a feature for all existing repositories
You can enable or disable features for all repositories.
GitHub Advanced Security,这些仓库的提交者将使用您的 GitHub Advanced Security 许可上的席位。 如果您已超出许可证容量,此选项将被禁用。
-
Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
-
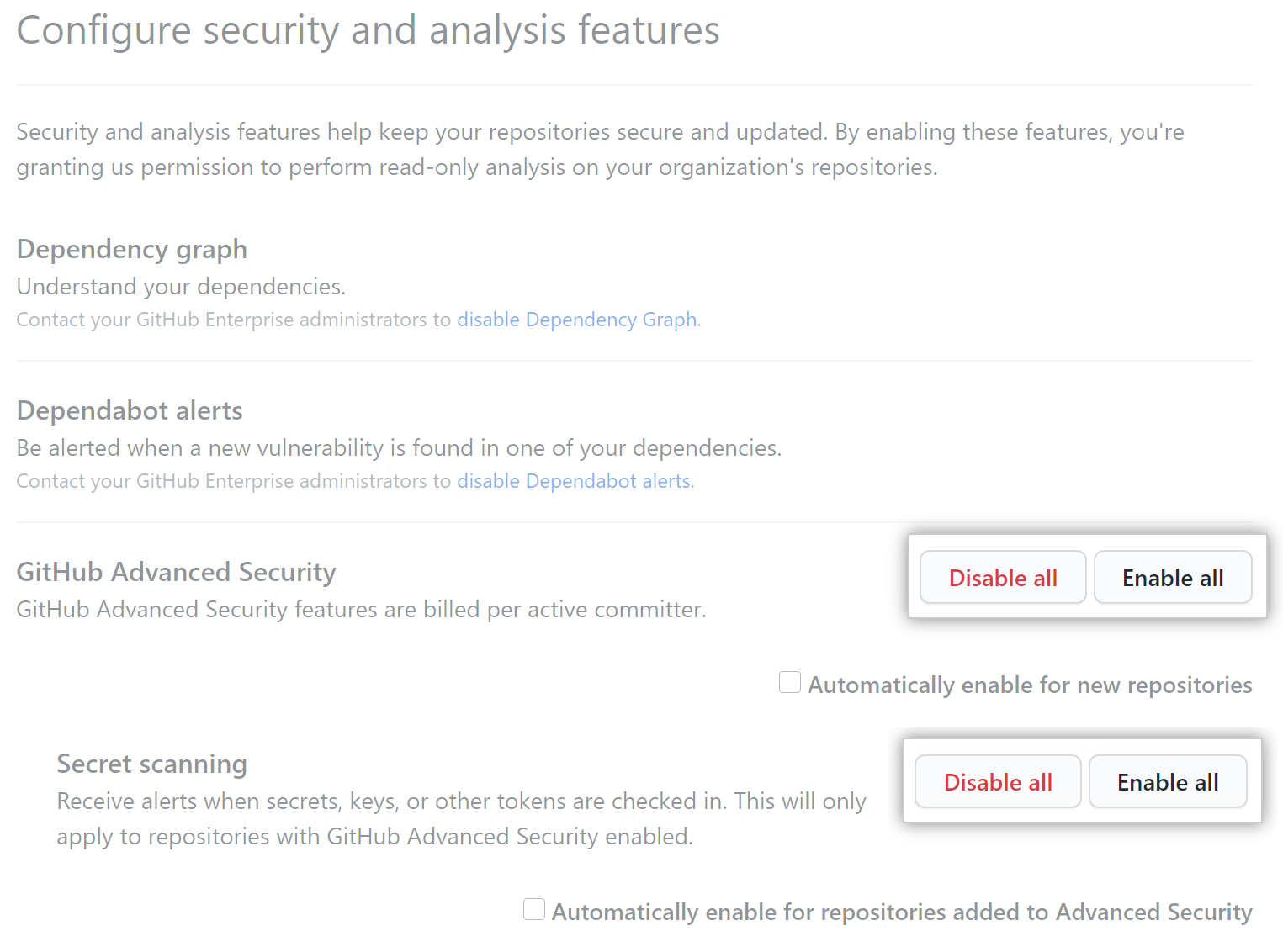
Under "Code security and analysis", to the right of the feature, click Disable all or Enable all. The control for "GitHub Advanced Security" is disabled if you have no available seats in your GitHub Advanced Security license.
-
Click Enable/Disable all or Enable/Disable for eligible repositories to confirm the change.
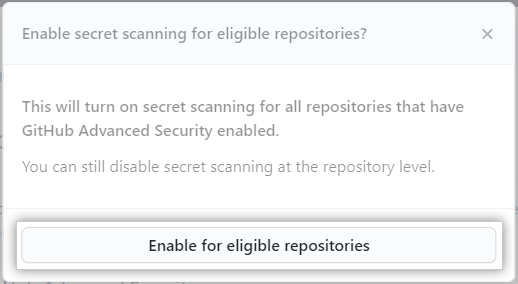
当您为现有仓库启用一个或多个安全和分析功能时,您将在� 分钟内看到 GitHub 上显示的任何结果:
- 所有现有仓库将具有选定的配置。
- 如果启用了新仓库的复选框,则新仓库将遵循所选配置。
Enabling or disabling a feature automatically when new repositories are added
-
Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
-
Under "Code security and analysis", to the right of the feature, enable or disable the feature by default for new repositories in your organization.
Removing access to GitHub Advanced Security from individual repositories in an organization
You can manage access to GitHub Advanced Security features for a repository from its "Settings" tab. For more information, see "Managing security and analysis settings for your repository." However, you can also disable GitHub Advanced Security features for a repository from the "Settings" tab for the organization.
- Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
- To see a list of all the repositories in your organization with GitHub Advanced Security enabled, scroll to the "GitHub Advanced Security repositories" section.
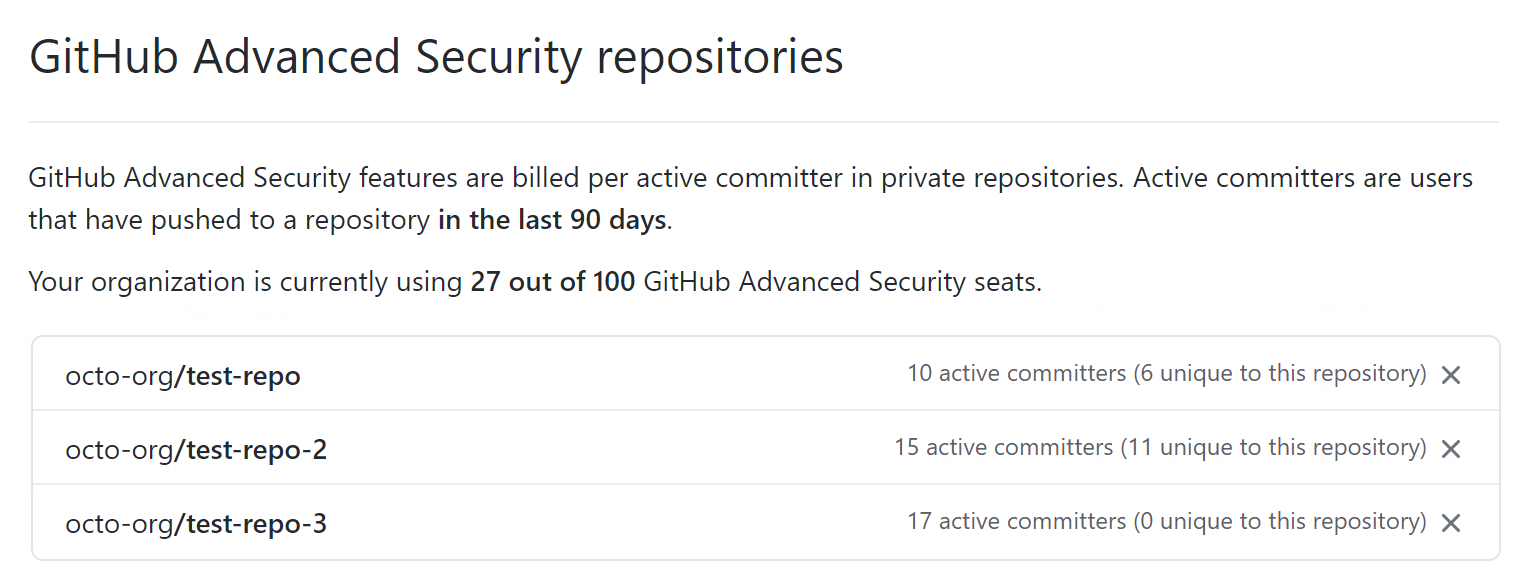 The table lists the number of unique committers for each repository. This is the number of seats you could free up on your license by removing access to GitHub Advanced Security. For more information, see "About billing for GitHub Advanced Security."
The table lists the number of unique committers for each repository. This is the number of seats you could free up on your license by removing access to GitHub Advanced Security. For more information, see "About billing for GitHub Advanced Security." - To remove access to GitHub Advanced Security from a repository and free up seats used by any committers that are unique to the repository, click the adjacent .
- In the confirmation dialog, click Remove repository to remove access to the features of GitHub Advanced Security.
Note: If you remove access to GitHub Advanced Security for a repository, you should communicate with the affected development team so that they know that the change was intended. This ensures that they don't waste time debugging failed runs of code scanning.