Versão do artigo: Enterprise Server 2.17
Usar CAS
O CAS é um protocolo de logon único (SSO) para vários aplicativos da web. Uma conta de usuário CAS não consome uma licença de até o usuário fazer login.
If you want to authenticate users without adding them to your identity provider, you can configure built-in authentication. Para obter mais informações, consulte "Permitir a autenticação integrada para usuários de fora do provedor de identidade".
Considerações de nome de usuário no CAS
GitHub Enterprise Server usernames can only contain alphanumeric characters and dashes (-). GitHub Enterprise Server will normalize any non-alphanumeric character in your account's username into a dash. For example, a username of gregory.st.john will be normalized to gregory-st-john. Note that normalized usernames also can't start or end with a dash. They also can't contain two consecutive dashes.
Usernames created from email addresses are created from the normalized characters that precede the @ character.
If multiple accounts are normalized into the same GitHub Enterprise Server username, only the first user account is created. Subsequent users with the same username won't be able to sign in.
This table gives examples of how usernames are normalized in GitHub Enterprise Server:
| Username | Normalized username | Resultado |
|---|---|---|
| Ms.Bubbles | ms-bubbles | This username is created successfully. |
| !Ms.Bubbles | -ms-bubbles | This username is not created, because it starts with a dash. |
| Ms.Bubbles! | ms-bubbles- | This username is not created, because it ends with a dash. |
| Ms!!Bubbles | ms--bubbles | This username is not created, because it contains two consecutive dashes. |
| Ms!Bubbles | ms-bubbles | This username is not created. Although the normalized username is valid, it already exists. |
| Ms.Bubbles@example.com | ms-bubbles | This username is not created. Although the normalized username is valid, it already exists. |
Autenticação de dois fatores
When using SAML or CAS, two-factor authentication is not supported or managed on the GitHub Enterprise Server appliance, but may be supported by the external authentication provider. Two-factor authentication enforcement on organizations is not available. For more information about enforcing two-factor authentication on organizations, see "Requiring two-factor authentication in your organization."
Atributos CAS
Os atributos a seguir estão disponíveis.
| Nome do atributo | Tipo | Descrição |
|---|---|---|
username | Obrigatório | Nome do usuário no GitHub Enterprise Server. |
Configurar o CAS
Aviso: antes de configurar o CAS na sua instância do GitHub Enterprise Server, observe que os usuários não poderão usar seus nomes e senhas do CAS para autenticar solicitações de API ou operações do Git por HTTP/HTTPS. Para isso, eles deverão criar tokens de acesso.
- In the upper-right corner of any page, click .

- In the left sidebar, click Console de gerenciamento.

- In the left sidebar, click Authentication.

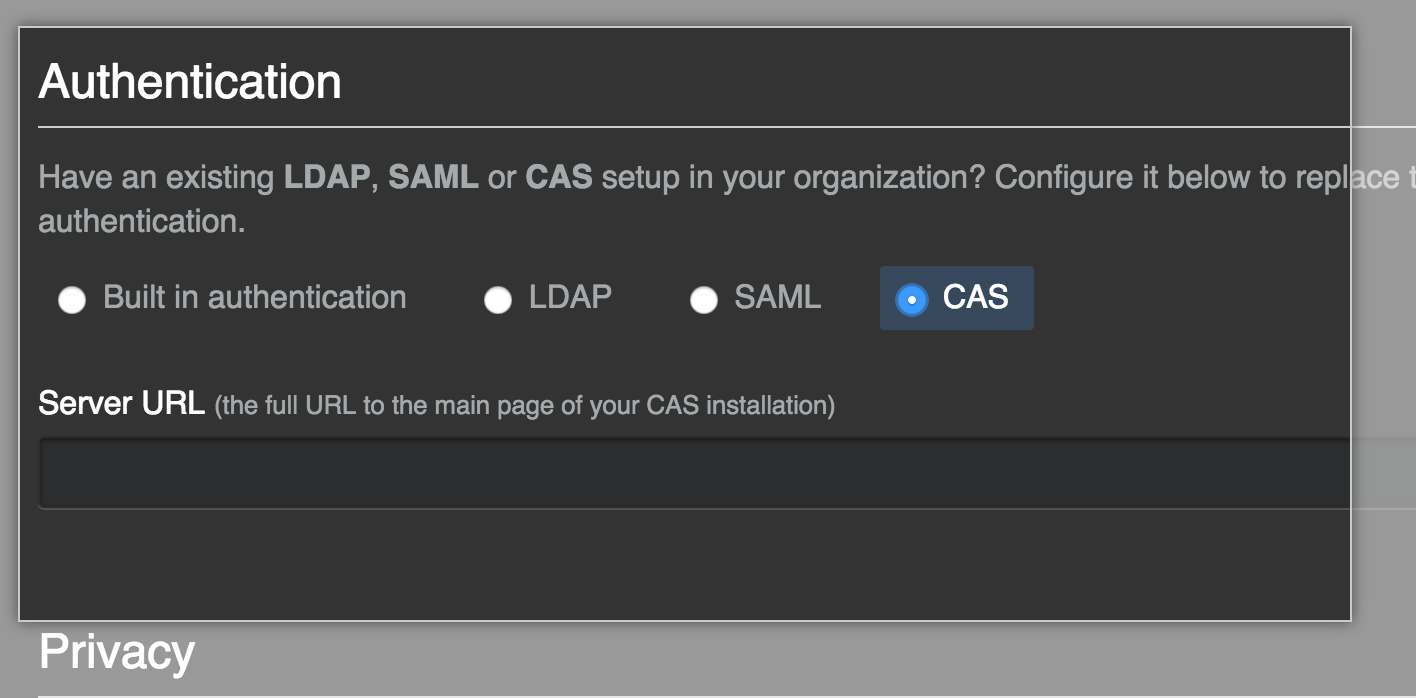
- Selecione CAS.
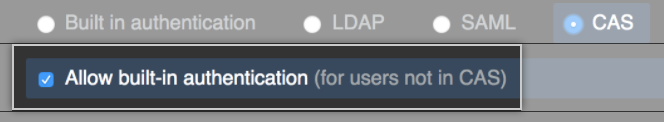
- Optionally, select Allow built-in authentication to invite users to use built-in authentication if they don’t belong to sua instância do GitHub Enterprise Server's identity provider.
- No campo Server URL (URL do servidor), digite a URL completa do seu servidor CAS. Se o servidor CAS usar um certificado que não pode ser validado pelo GitHub Enterprise Server, você poderá usar o comando
ghe-ssl-ca-certificate-installpara instalá-lo como certificado confiável.