Warnung
Es wird empfohlen, nur selbstgehostete Runner mit privaten Repositorys zu verwenden. Der Grund hierfür liegt darin, dass Forks deines öffentlichen Repositorys möglicherweise gefährlichen Code auf deinem selbstgehosteten Runnercomputer ausführen können, indem sie einen Pull Request erstellen, der den Code in einem Workflow ausführt.
For more information, see Secure use reference.
Hinweis
Auf GitHub gehostete Runner werden aktuell nicht auf GitHub Enterprise Server unterstützt. Weitere Informationen zur geplanten zukünftigen Unterstützung findest Du in der GitHub public roadmap.
Prerequisites
Before you add a self-hosted runner, you should understand what they are and how they work. See Informationen zu selbstgehosteten Runnern.
Additionally, you must meet the following requirements:
-
GitHub Actions muss für GitHub Enterprise Server aktiviert sein. Ein Websiteadministrator kann GitHub Actions für deine Instanz aktivieren und konfigurieren. Weitere Informationen finden Sie unter Erste Schritte mit GitHub Actions für GitHub Enterprise Server.
-
Du musst Zugriff auf den Computer haben, den du als selbst gehosteten Runner in deiner Umgebung verwendest.
- Die Verbindung zwischen selbstgehosteten Runnern und GitHub verläuft über HTTP (Port 80) oder HTTPS (Port 443). Um die Konnektivität über HTTPS sicherzustellen, konfigurieren Sie TLS für GitHub Enterprise Server. Weitere Informationen findest du unter TLS konfigurieren.
Adding a self-hosted runner to a repository
You can add self-hosted runners to a single repository. To add a self-hosted runner to a user repository, you must be the repository owner. For an organization repository, you must be an organization owner, have admin access to the repository, or have the “Manage organization runners and runner groups” permission.
For more information about custom organization roles, see Informationen zu benutzerdefinierten Organisationsrollen.
For information about how to add a self-hosted runner with the REST API, see REST-API-Endpunkte für selbst gehostete Runner.
Hinweis
Unternehmens- und Organisationsbesitzer*innen können wählen, für welche Repositorys die Erstellung selbstgehosteter Runner auf Repositoryebene erlaubt ist. Benutzer mit der Berechtigung „Verwalten von Organisationsrunnern und Runnergruppen“ können nur auswählen, welche Repositorys selbstgehostete Runner auf Repositoryebene für Repositorys in deiner Organisation erstellen dürfen.
Weitere Informationen zu benutzerdefinierten Organisationsrollen findest du unter Informationen zu benutzerdefinierten Organisationsrollen.
Weitere Informationen findest du unter Erzwingen von Richtlinien für GitHub Actions in deinem Unternehmen und unter GitHub Actions für deine Organisation Deaktivieren oder Einschränken.
-
Navigieren Sie auf GitHub zur Hauptseite des Repositorys.
-
Wähle unter dem Namen deines Repositorys die Option Einstellungen aus. Wenn die Registerkarte „Einstellungen“ nicht angezeigt wird, wähle im Dropdownmenü die Option Einstellungen aus.

-
Klicke in der linken Seitenleiste auf Aktionen und dann auf Runner.
-
Click New self-hosted runner.
-
Wähle das Betriebssystemimage und die Architektur deines selbstgehosteten Runnercomputers aus.
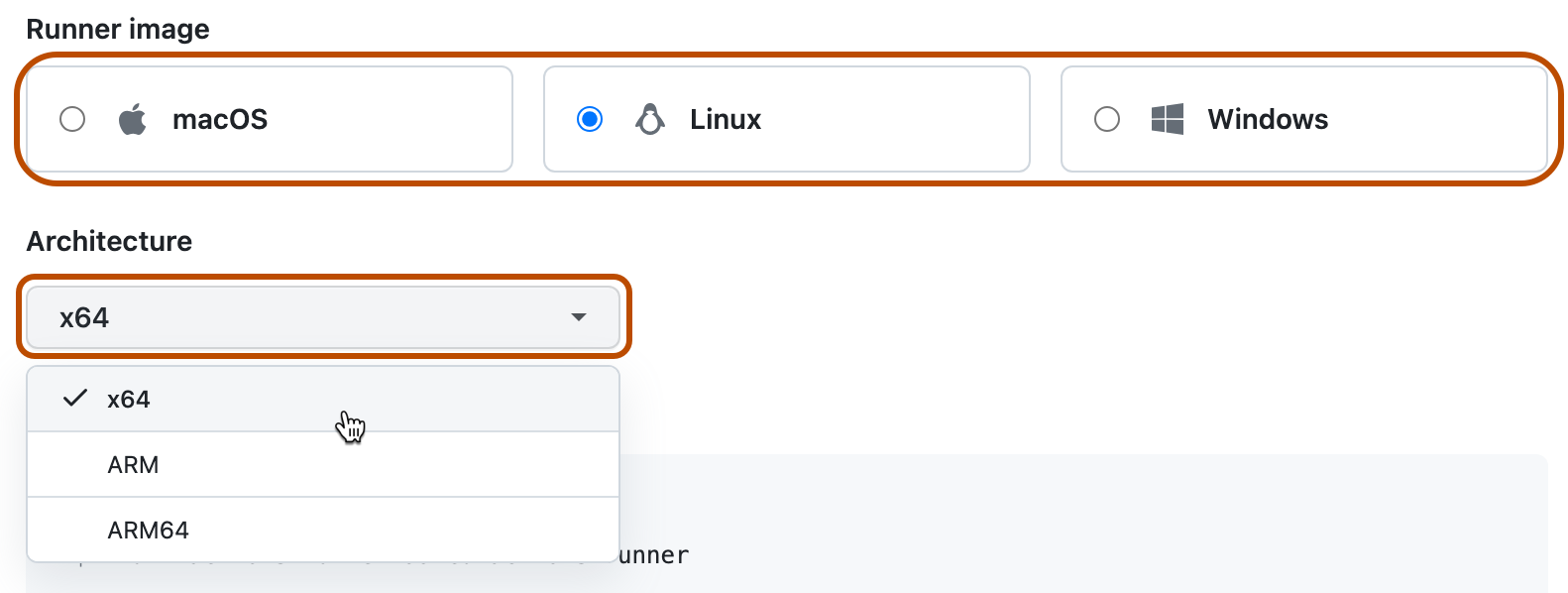
-
Du wirst Anweisungen sehen, wie Du die Läuferanwendung herunterlädst und sie auf Deiner selbst-gehosteten Läufermaschine installierst.
Öffne eine Shell auf Deiner selbst-gehosteten Läufermaschine und führe jeden Shell-Befehl in der angezeigten Reihenfolge aus.
Hinweis
Wenn du unter Windows die selbstgehostete Runneranwendung als Dienst installieren möchtest, musst du eine Shell mit Administratorberechtigungen öffnen. Auch wird empfohlen, dass du
C:\actions-runnerals Verzeichnis für die selbstgehostete Runneranwendung verwendest, damit Windows-Systemkonten auf das Runnerverzeichnis zugreifen können.Die Anweisungen führen Dich durch die Vervollständigung dieser Aufgaben:
- Herunterladen und Extrahieren der selbst-gehosteten Läuferanwendung.
- Ausführen des
config-Skripts zum Konfigurieren der selbstgehosteten Runneranwendung und die Registrierung mit GitHub Actions Dasconfig-Skript benötigt die Ziel-URL und ein automatisch generiertes, zeitlich begrenztes Token, um die Anforderung zu authentifizieren. Das Token läuft nach einer Stunde ab.- Unter Windows fragt das
config-Skript auch, ob du die selbstgehostete Runneranwendung als Dienst installieren möchtest. Für Linux und macOS kannst Du einen Dienst installieren, nachdem Du das Hinzufügen des Läufers beendet hast. Weitere Informationen finden Sie unter Configuring the self-hosted runner application as a service.
- Unter Windows fragt das
- Ausführen der selbst-gehosteten Läuferanwendung zum Verbinden der Maschine mit GitHub Actions.
Überprüfung dass dein selbst-gehosteter Läufer erfolgreich hinzugefügt wurde
Nach Abschluss der Schritte zum Hinzufügen eines selbst gehosteten Runners werden der Runner und sein Status jetzt unter „Selbst-gehostete Runner“ aufgeführt.
Die selbst-gehostete Läuferanwendung muss aktiv sein, damit der Läufer Aufträge annehmen kann. Wenn die Runner-Anwendung mit GitHub verbunden und bereit ist, Aufträge zu empfangen, siehst du die folgende Meldung auf dem Terminal des Computers.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Adding a self-hosted runner to an organization
You can add self-hosted runners at the organization level, where they can be used to process jobs for multiple repositories in an organization. To add a self-hosted runner to an organization, you must be an organization owner or have the "Manage organization runners and runner groups" permission. For information about how to add a self-hosted runner with the REST API, see REST-API-Endpunkte für selbst gehostete Runner.
For more information about custom organization roles, see Informationen zu benutzerdefinierten Organisationsrollen.
-
Navigieren Sie auf GitHub zur Hauptseite der Organisation.
-
Klicke unter deinem Organisationsnamen auf die Option Einstellungen. Wenn die Registerkarte „Einstellungen“ nicht angezeigt wird, wähle im Dropdownmenü die Option Einstellungen aus.

-
Klicke in der linken Seitenleiste auf Aktionen und dann auf Runner.
-
Click New runner.
-
Wähle das Betriebssystemimage und die Architektur deines selbstgehosteten Runnercomputers aus.

-
Du wirst Anweisungen sehen, wie Du die Läuferanwendung herunterlädst und sie auf Deiner selbst-gehosteten Läufermaschine installierst.
Öffne eine Shell auf Deiner selbst-gehosteten Läufermaschine und führe jeden Shell-Befehl in der angezeigten Reihenfolge aus.
Hinweis
Wenn du unter Windows die selbstgehostete Runneranwendung als Dienst installieren möchtest, musst du eine Shell mit Administratorberechtigungen öffnen. Auch wird empfohlen, dass du
C:\actions-runnerals Verzeichnis für die selbstgehostete Runneranwendung verwendest, damit Windows-Systemkonten auf das Runnerverzeichnis zugreifen können.Die Anweisungen führen Dich durch die Vervollständigung dieser Aufgaben:
- Herunterladen und Extrahieren der selbst-gehosteten Läuferanwendung.
- Ausführen des
config-Skripts zum Konfigurieren der selbstgehosteten Runneranwendung und die Registrierung mit GitHub Actions Dasconfig-Skript benötigt die Ziel-URL und ein automatisch generiertes, zeitlich begrenztes Token, um die Anforderung zu authentifizieren. Das Token läuft nach einer Stunde ab.- Unter Windows fragt das
config-Skript auch, ob du die selbstgehostete Runneranwendung als Dienst installieren möchtest. Für Linux und macOS kannst Du einen Dienst installieren, nachdem Du das Hinzufügen des Läufers beendet hast. Weitere Informationen finden Sie unter Configuring the self-hosted runner application as a service.
- Unter Windows fragt das
- Ausführen der selbst-gehosteten Läuferanwendung zum Verbinden der Maschine mit GitHub Actions.
Überprüfung dass dein selbst-gehosteter Läufer erfolgreich hinzugefügt wurde
Nach Abschluss der Schritte zum Hinzufügen eines selbst gehosteten Runners werden der Runner und sein Status jetzt unter „Selbst-gehostete Runner“ aufgeführt.
Die selbst-gehostete Läuferanwendung muss aktiv sein, damit der Läufer Aufträge annehmen kann. Wenn die Runner-Anwendung mit GitHub verbunden und bereit ist, Aufträge zu empfangen, siehst du die folgende Meldung auf dem Terminal des Computers.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Hinweis
Aus Sicherheitsgründen können öffentliche Repositorys standardmäßig keine Runner in einer Runnergruppe verwenden, aber du kannst dies in den Einstellungen der Runnergruppe außer Kraft setzen. Weitere Informationen finden Sie unter Managing access to self-hosted runners using groups.
Adding a self-hosted runner to an enterprise
You can add self-hosted runners to an enterprise, where they can be assigned to multiple organizations. The organization owner can control which repositories can use it.
New runners are assigned to the default group. You can modify the runner's group after you've registered the runner. For more information, see Managing access to self-hosted runners using groups.
To add a self-hosted runner to an enterprise, you must be an enterprise owner. For information about how to add a self-hosted runner with the REST API, see the enterprise endpoints in the GitHub Actions REST API.
-
Klicken Sie in der oberen rechten Ecke von GitHub Enterprise Server auf Ihr Profilfoto und dann auf Unternehmenseinstellungen.

-
Klicke links auf der Seite in der Randleiste für das Enterprise-Konto auf Policies.
-
Klicke unter „ Richtlinien“ auf Actions.
-
Klicke auf die Registerkarte Runner.
-
Klicke auf Neuer Runner. 1. Wähle das Betriebssystemimage und die Architektur deines selbstgehosteten Runnercomputers aus.

-
Du wirst Anweisungen sehen, wie Du die Läuferanwendung herunterlädst und sie auf Deiner selbst-gehosteten Läufermaschine installierst.
Öffne eine Shell auf Deiner selbst-gehosteten Läufermaschine und führe jeden Shell-Befehl in der angezeigten Reihenfolge aus.
Hinweis
Wenn du unter Windows die selbstgehostete Runneranwendung als Dienst installieren möchtest, musst du eine Shell mit Administratorberechtigungen öffnen. Auch wird empfohlen, dass du
C:\actions-runnerals Verzeichnis für die selbstgehostete Runneranwendung verwendest, damit Windows-Systemkonten auf das Runnerverzeichnis zugreifen können.Die Anweisungen führen Dich durch die Vervollständigung dieser Aufgaben:
- Herunterladen und Extrahieren der selbst-gehosteten Läuferanwendung.
- Ausführen des
config-Skripts zum Konfigurieren der selbstgehosteten Runneranwendung und die Registrierung mit GitHub Actions Dasconfig-Skript benötigt die Ziel-URL und ein automatisch generiertes, zeitlich begrenztes Token, um die Anforderung zu authentifizieren. Das Token läuft nach einer Stunde ab.- Unter Windows fragt das
config-Skript auch, ob du die selbstgehostete Runneranwendung als Dienst installieren möchtest. Für Linux und macOS kannst Du einen Dienst installieren, nachdem Du das Hinzufügen des Läufers beendet hast. Weitere Informationen finden Sie unter Configuring the self-hosted runner application as a service.
- Unter Windows fragt das
- Ausführen der selbst-gehosteten Läuferanwendung zum Verbinden der Maschine mit GitHub Actions.
Überprüfung dass dein selbst-gehosteter Läufer erfolgreich hinzugefügt wurde
Nach Abschluss der Schritte zum Hinzufügen eines selbst gehosteten Runners werden der Runner und sein Status jetzt unter „Selbst-gehostete Runner“ aufgeführt.
Die selbst-gehostete Läuferanwendung muss aktiv sein, damit der Läufer Aufträge annehmen kann. Wenn die Runner-Anwendung mit GitHub verbunden und bereit ist, Aufträge zu empfangen, siehst du die folgende Meldung auf dem Terminal des Computers.
√ Connected to GitHub
2019-10-24 05:45:56Z: Listening for Jobs
For more information, see Monitoring and troubleshooting self-hosted runners.
Hinweis
Aus Sicherheitsgründen können öffentliche Repositorys standardmäßig keine Runner in einer Runnergruppe verwenden, aber du kannst dies in den Einstellungen der Runnergruppe außer Kraft setzen. Weitere Informationen finden Sie unter Managing access to self-hosted runners using groups.
Making enterprise runners available to repositories
By default, runners in an enterprise's "Default" self-hosted runner group are available to all organizations in the enterprise, but are not available to all repositories in each organization.
To make an enterprise-level self-hosted runner group available to an organization repository, you might need to change the organization's inherited settings for the runner group to make the runner available to repositories in the organization.
For more information on changing runner group access settings, see Managing access to self-hosted runners using groups.
Next steps
You can set up automation to scale the number of self-hosted runners. For more information, see Self-hosted runners reference.