Perguntar a GitHub Copilot Chat sobre alertas de code scanning
Com uma licença do GitHub Copilot Enterprise, você pode pedir ajuda ao Copilot Chat para entender melhor os alertas de segurança, incluindo alertas do code scanning, em repositórios em sua organização. Para saber mais, confira Como fazer perguntas ao GitHub Copilot no GitHub.
Gerar correções sugeridas para alertas de code scanning
O GitHub Copilot Autofix pode gerar correções para alertas identificados pela análise code scanning. A maioria dos tipos de alerta CodeQL é compatível, assim como alguns alertas de ferramentas de terceiros. Para saber mais, confira Uso responsável da Correção Automática do Copilot para verificação de código.
Note
Você não precisa de uma assinatura do GitHub Copilot para usar o GitHub Copilot Autofix. O Copilot Autofix está disponível para todos os repositórios públicos em GitHub.com, bem como repositórios privados em empresas no GitHub Enterprise Cloud que tenham uma licença para GitHub Advanced Security.
- Em GitHub, acesse a página principal do repositório.
- Abaixo do nome do repositório, clique em Segurança. Caso não consiga ver a guia "Segurança", selecione o menu suspenso e clique em Segurança.

- Na barra lateral, clique em Code scanning.
- Clique no nome de um alerta.
- Se o Copilot Autofix pode sugerir uma correção, na parte superior da página, clique em Generate fix.
- Depois que a correção sugerida for gerada, na parte inferior da página, você poderá clicar em Criar PR com correção para gerar automaticamente uma solicitação de pull com a correção sugerida. Um novo branch é criado a partir do branch padrão, a correção gerada é confirmada e uma solicitação de pull de rascunho é criada. Você pode testar e editar a correção sugerida como faria com qualquer outra correção.
Você também pode usar a API de Correção Automática em pontos de extremidade de alertas históricos para gerar e obter as correções sugeridas, além de fazer commit delas.
- Criar uma correção automática para um alerta da digitalização de código
- Obter o status de uma correção automática para um alerta da digitalização de código
- Confirmar uma correção automática para um alerta da digitalização de código
Para obter informações sobre as limitações das correções geradas automaticamente, confira Limitações das sugestões.
Corrigir um alerta manually
Qualquer pessoa com permissão de gravação para um repositório pode corrigir um alerta, fazendo o commit de uma correção do código. Se o repositório tiver code scanning agendado para ser executado em pull requests, recomenda-se registrar um pull request com sua correção. Isso ativará a análise de code scanning referente às alterações e irá testar se sua correção não apresenta nenhum problema novo. Para saber mais, confira Alertas de varredura de código de triagem em pull requests.
Você pode usar a pesquisa de texto livre ou os filtros para ver um subconjunto de alertas e depois marcar todos os alertas correspondentes como fechados.
Alertas podem ser corrigidos em um branch, mas não em outro. Você pode usar o filtro "Branch", no resumo dos alertas, para verificar se um alerta é corrigido em um branch específico.

Observe que, se você tiver filtrado os alertas em um branch não padrão, mas os mesmos alertas existirem no branch padrão, a página de qualquer alerta especificado ainda refletirá apenas o status do alerta no branch padrão, mesmo que esse status entre em conflito com o status em um branch não padrão. Por exemplo, um alerta exibido na lista "Abrir" no resumo dos alertas de branch-x pode mostrar o status "Corrigido" na página do alerta, caso o alerta já esteja corrigido no branch padrão. Veja o status do alerta para o branch na seção Branches afetados no lado direito da página de alerta.
Note
Se você executar code scanning usando várias configurações, o mesmo alerta poderá ser gerado por mais de uma configuração. A menos que você execute todas as configurações regularmente, talvez você veja os alertas corrigidos em uma configuração, mas não em outra. Essas configurações e alertas obsoletos podem ser removidos de um branch. Para obter mais informações, confira Como remover configurações e alertas obsoletos de um branch.
Ignorar alertas
Há duas formas de fechar um alerta. Você pode corrigir o problema no código ou pode ignorar o alerta.
Ignorar um alerta é uma maneira de fechar um alerta que você não acha que precisa ser corrigido. Por exemplo, um erro no código que é usado apenas para testes ou quando o esforço de corrigir o erro é maior do que o benefício potencial de melhorar o código. Você pode ignorar alertas de anotações da code scanning no código ou na lista de resumo na guia Segurança.
Ao descartar um alerta:
- Ele é ignorado em todos os branches.
- O alerta é removido do número de alertas atuais para o seu projeto.
- O alerta é movido para a lista "Fechado" no resumo dos alertas, onde você pode reabri-lo, se necessário.
- O motivo pelo qual você fechou o alerta é registrado.
- Opcionalmente, você pode fazer um comentário para registrar o contexto de um alerta ignorado.
- Da próxima vez que code scanning for executado, o mesmo código não gerará um alerta.
Para ignorar alertas:
-
Em GitHub, acesse a página principal do repositório.
-
Abaixo do nome do repositório, clique em Segurança. Caso não consiga ver a guia "Segurança", selecione o menu suspenso e clique em Segurança.

-
Na barra lateral, clique em Code scanning.
-
Se você deseja ignorar um alerta, é importante explorar primeiro o alerta para que você possa escolher o motivo correto para ignorá-lo. Clique no alerta que você deseja explorar.
-
Revise o alerta, clique em Ignorar alerta e escolha ou digite um motivo para fechá-lo.
É importante escolher o motivo apropriado no menu suspenso, pois isso pode afetar se uma consulta continua sendo incluída em análise futura. Opcionalmente, você pode fazer um comentário para registrar o contexto de um alerta ignorado. O comentário sobre o alerta ignorado é adicionado à linha do tempo do alerta e pode ser usado como justificativa em auditorias e relatórios. Você pode recuperar ou definir um comentário usando a API REST de verificação de código. O comentário está contido no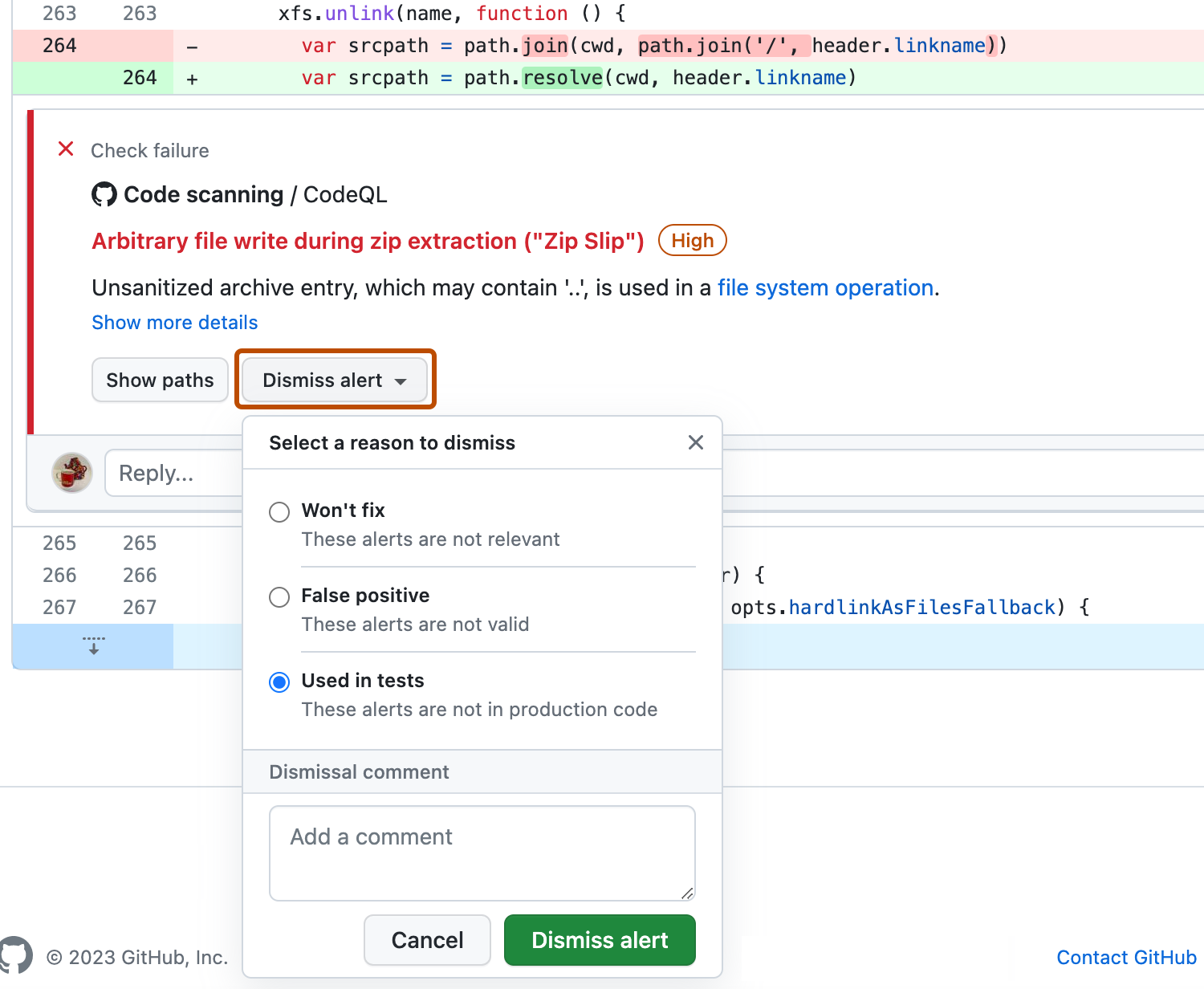
dismissed_commentdo ponto de extremidadealerts/{alert_number}. Para saber mais, confira Pontos de extremidade da API REST para varredura de código.Se você ignorar um alerta de CodeQL como um falso resultado positivo, por exemplo, porque o código usa uma biblioteca de sanitização incompatível, considere contribuir para o repositório de CodeQL e melhorar a análise. Para obter mais informações sobre CodeQL, confira Contribuir para CodeQL.
Ignorar múltiplos alertas de uma vez
Se um projeto tem vários alertas que você deseja ignorar pelo mesmo motivo, você pode ignorá-los em massa do resumo de alertas. Normalmente, você pode querer filtrar a lista e, em seguida, ignorar todos os alertas correspondentes. Por exemplo, você pode querer ignorar todos os alertas atuais no projeto que foram marcados para uma vulnerabilidade específica de Enumeração de Fraqueza Comum (CWE).
Reabertura de alertas descartados
Se você descartar um alerta, mas depois perceber que precisa corrigi-lo, poderá reabri-lo e corrigir o problema com o código. Exiba a lista de alertas fechados, localize o alerta, exiba-o e abra-o novamente. Em seguida, você pode corrigir o alerta da mesma forma que qualquer outro alerta.
Como remover configurações obsoletas e alertas de um branch
Você pode ter várias configurações de verificação de código em um repositório individual. Quando executadas, várias configurações podem gerar o mesmo alerta. Além disso, se as configurações forem executadas em agendamentos diferentes, os status do alerta poderão ficar desatualizados para configurações pouco frequentes ou obsoletas. Para obter mais informações sobre alertas de várias configurações, confira Sobre alertas de digitalização de códigos.
-
Em GitHub, acesse a página principal do repositório.
-
Abaixo do nome do repositório, clique em Segurança. Caso não consiga ver a guia "Segurança", selecione o menu suspenso e clique em Segurança.

-
Na barra lateral, clique em Code scanning.
-
Em "Code scanning", clique em um alerta da code scanning.
-
Na seção "Branches afetados" da barra lateral, clique no branch desejado.
-
Na caixa de diálogo "Análise de configurações", revise os detalhes das configurações que relataram esse alerta no branch selecionado. Para excluir uma configuração indesejada para o branch desejado, clique em .
Se você excluir uma configuração por engano, clique em Cancelar para evitar aplicar as alterações.

-
Depois de remover as configurações indesejadas e confirmar que as configurações esperadas são exibidas, clique em Salvar alterações.
Se você salvar as alterações depois de excluir acidentalmente uma configuração, execute novamente a configuração para atualizar o alerta. Para obter mais informações sobre como executar novamente as configurações que usam o GitHub Actions, confira Reexecutando fluxos de trabalho e trabalhos.
Note
- Se você remover todas as configurações da code scanning para o branch padrão do repositório, o branch padrão permanecerá na barra lateral "Branches afetados", mas não será analisado por nenhuma configuração.
- Se você remover todas as configurações da code scanning para qualquer branch diferente do branch padrão do repositório, esse branch será removido da barra lateral "Branches afetados".