GitHub 호스트형 실행기에 대한 Azure 개인 네트워킹 정보
Azure VNET에서 GitHub 호스트형 실행기를 사용할 수 있습니다. 이렇게 하면 실행기 네트워킹 정책의 모든 권한을 제공하면서 CI/CD의 GitHub관리 인프라를 사용할 수 있습니다. Azure VNET에 대한 자세한 내용은 Azure 문서의 Azure Virtual Network란?을 참조하세요.
여러 VNET 서브넷을 GitHub.com에 연결하고 실행기 그룹을 통해 실행기에 대한 프라이빗 리소스 액세스를 관리할 수 있습니다. 실행기 그룹에 대한 자세한 내용은 "더 큰 실행기 액세스 제어"을(를) 참조하세요.
Azure VNET 내에서 GitHub 호스트 실행기를 사용하면 다음 작업을 할 수 있습니다.
- 인터넷 포트를 열지 않고 실행기를 Azure VNET 내의 리소스에 비공개로 연결하며, 여기에는 Azure VNET에서 액세스할 수 있는 온-프레미스 리소스도 포함됩니다.
- GitHub 호스트 실행기의 액세스를 비롯해, 아웃바운드 네트워크 정책 완전 제어가 가능한 연결을 제한합니다.
- GitHub 호스트 실행기 네트워크 로그를 모니터링하고 실행기와의 모든 연결을 확인합니다.
Azure VNET에서 대형 러너 사용 정보
Azure VNET에서는 2-64 vCPU Ubuntu 및 Windows 실행기가 지원됩니다. 이러한 실행기 유형에 대한 자세한 내용은 "대규모 실행기 정보"을 참조하세요.
GitHub-호스트형 실행기용 개인 네트워킹은 대형 실행기에 고정 IP 주소를 지원하지 않습니다. 대형 실행기를 위한 기본 구성인 동적 IP 주소를 사용해야 합니다. 대형 실행기의 네트워킹에 대한 자세한 내용은 "대규모 실행기 정보"을 참조하세요.
네트워크 통신 정보
GitHub 네트워크와 VNET 간의 통신을 용이하게 하기 위해 GitHub 호스트 실행기의 NIC(네트워크 인터페이스 카드)가 Azure VNET에 배포됩니다.
NIC는 VNET 내에 있으므로 GitHub는 인바운드 연결을 차단할 수 없습니다. 기본적으로 Azure 가상 머신은 동일한 VNET의 인바운드 연결을 허용합니다. 자세한 내용은 Microsoft Learn의 AllowVNetInBound를 참조하세요. 실행기에서 모든 인바운드 연결을 명시적으로 차단하는 것이 좋습니다. GitHub는 이러한 컴퓨터에 대한 인바운드 연결이 필요하지 않습니다.
NIC를 사용하면 Azure VM(가상 머신)에서 인터넷, Azure 및 온-프레미스 리소스와 통신할 수 있습니다. 이렇게 하면 모든 통신이 네트워크 경계 내에서 비공개로 유지되고 VNET에 적용된 네트워킹 정책도 실행기에 적용됩니다. 네트워크 인터페이스를 관리하는 방법에 대한 자세한 내용은 Microsoft Learn의 네트워크 인터페이스 설정 변경을 참조하세요.
Note
GitHub Actions 서비스가 작업을 실행하기 위해 리소스를 과도하게 프로비전하므로 구독에서 단일 작업에 대해 여러 NIC가 나타날 수 있습니다. 실행기를 유휴 상태로 설정하면 GitHub Actions 서비스가 자동으로 리소스 프로비저닝을 해제하고 해당 NIC를 제거합니다.
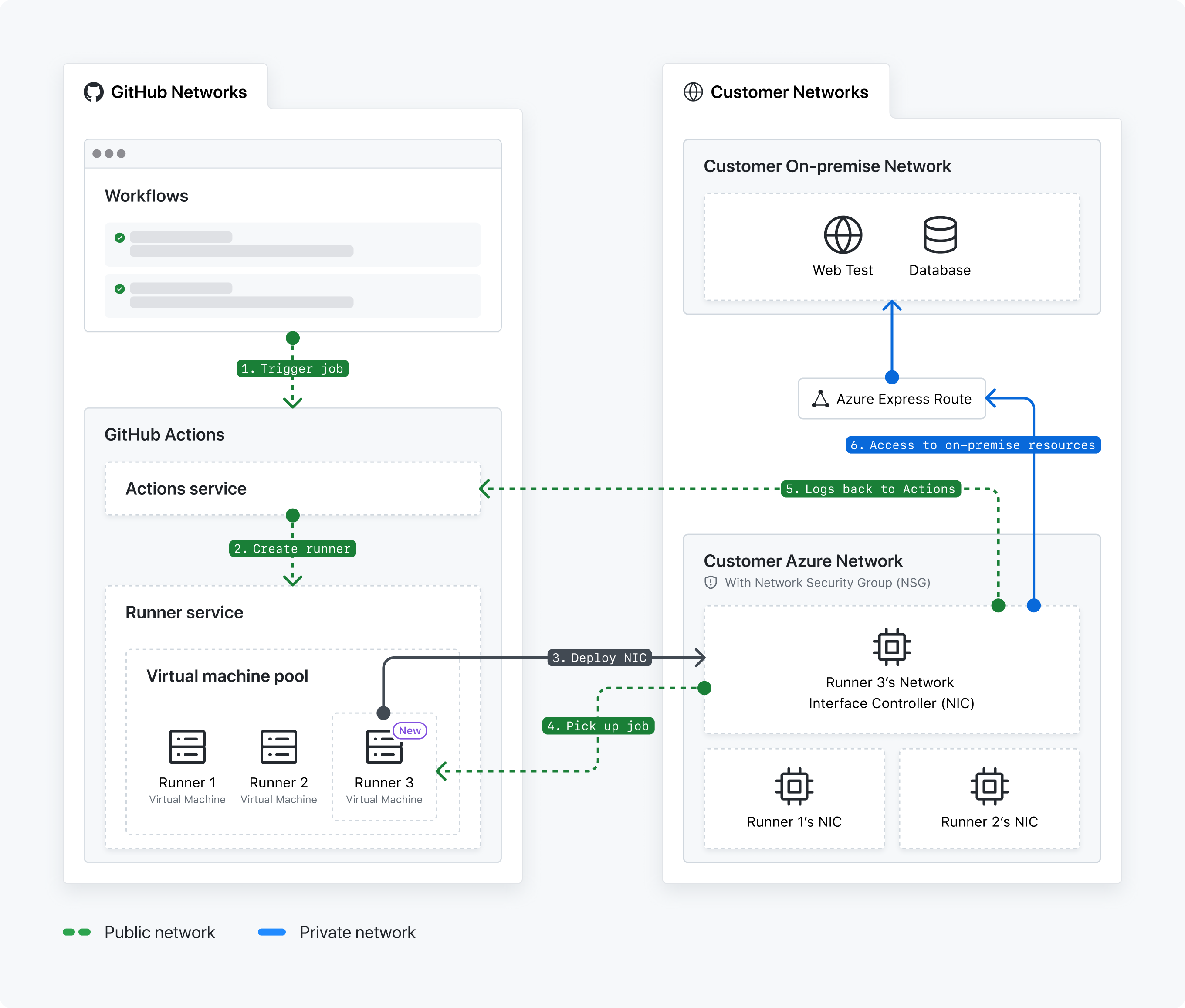
- GitHub Actions 워크플로가 트리거됩니다.
- GitHub Actions 서비스는 실행기를 만듭니다.
- 실행기 서비스는 GitHub 호스트 실행기기의 NIC(네트워크 인터페이스 카드)를 Azure VNET에 배포합니다.
- 실행기 에이전트가 워크플로 작업을 선택합니다. GitHub Actions 서비스는 작업을 큐에 대기합니다.
- 실행기는 GitHub Actions 서비스로 로그를 다시 보냅니다.
- NIC는 온-프레미스 리소스에 액세스합니다.
지원되는 지역 정보
GitHub Actions 서비스는 Azure에서 제공하는 모든 지역의 하위 집합을 지원합니다. GitHub Actions 서비스와 서브넷 간의 통신을 용이하게 하려면 서브넷이 지원되는 다음 지역 중 하나에 있어야 합니다.
EastUsEastUs2WestUs2AustraliaEastCentralUsFranceCentralNorthEuropeNorwayEastSoutheastAsiaSwitzerlandNorthUkSouth
Azure 프라이빗 네트워킹은 다음 지역에서 GPU 실행기를 지원합니다.
EastUsWestUsNorthCentralUsSouthCentralUs
또한 글로벌 가상 네트워크 피어링을 사용하여 Azure 지역 간에 가상 네트워크를 연결할 수도 있습니다. 자세한 내용은 Azure 설명서의 가상 네트워크 피어링을 참조하세요.
GitHub Actions 서비스 권한 정보
NIC를 성공적으로 배포하고 서브넷에 NIC를 조인하기 위해 GitHub Actions 서비스는 Azure 구독에서 다음 Azure RBAC(역할 기반 액세스 제어) 권한을 유지합니다. Azure 리소스의 세분화된 액세스 관리에 대한 자세한 내용은 Azure 설명서에서 Azure RBAC를 참조하세요.
GitHub.Network/operations/readGitHub.Network/networkSettings/readGitHub.Network/networkSettings/writeGitHub.Network/networkSettings/deleteMicrosoft.Network/locations/operations/readMicrosoft.Network/locations/operationResults/readMicrosoft.Network/locations/usages/readMicrosoft.Network/networkInterfaces/readMicrosoft.Network/networkInterfaces/writeMicrosoft.Network/networkInterfaces/deleteMicrosoft.Network/networkInterfaces/join/actionMicrosoft.Network/networkSecurityGroups/join/actionMicrosoft.Network/networkSecurityGroups/readMicrosoft.Network/publicIpAddresses/readMicrosoft.Network/publicIpAddresses/writeMicrosoft.Network/publicIPAddresses/join/actionMicrosoft.Network/routeTables/join/actionMicrosoft.Network/virtualNetworks/readMicrosoft.Network/virtualNetworks/subnets/join/actionMicrosoft.Network/virtualNetworks/subnets/readMicrosoft.Network/virtualNetworks/subnets/writeMicrosoft.Network/virtualNetworks/subnets/serviceAssociationLinks/deleteMicrosoft.Network/virtualNetworks/subnets/serviceAssociationLinks/readMicrosoft.Network/virtualNetworks/subnets/serviceAssociationLinks/writeMicrosoft.Network/virtualNetworks/subnets/serviceAssociationLinks/details/readMicrosoft.Network/virtualNetworks/subnets/serviceAssociationLinks/validate/actionMicrosoft.Resources/subscriptions/resourceGroups/readMicrosoft.Resources/subscriptions/resourcegroups/deployments/readMicrosoft.Resources/subscriptions/resourcegroups/deployments/writeMicrosoft.Resources/subscriptions/resourcegroups/deployments/operations/readMicrosoft.Resources/deployments/readMicrosoft.Resources/deployments/writeMicrosoft.Resources/deployments/operationStatuses/read
다음 권한은 Azure 테넌트에 있는 두 엔터프라이즈 애플리케이션에 있습니다. Azure 프라이빗 네트워킹을 구성한 후 Azure 테넌트에 엔터프라이즈 애플리케이션이 표시됩니다.
GitHub CPS Network ServiceID:85c49807-809d-4249-86e7-192762525474GitHub Actions APIID:4435c199-c3da-46b9-a61d-76de3f2c9f82
VNET의 네트워크 정책 사용
GitHub 호스트 실행기 NIC가 Azure VNET에 배포되므로 VNET에 적용된 네트워킹 정책도 실행기에 적용됩니다.
예를 들어 VNET이 Azure ExpressRoute를 사용하여 온-프레미스 리소스(예: Artifactory)에 대한 액세스를 제공하도록 구성되거나 다른 클라우드 기반 리소스에 대한 액세스를 제공하기 위해 VPN 터널에 연결된 경우, 해당 액세스 정책도 실행기에도 적용됩니다. 또한 VNET의 NSG(네트워크 보안 그룹)에 적용되는 모든 아웃바운드 규칙도 적용되므로 실행기에서 아웃바운드 액세스를 제어할 수 있습니다.
VNET에 대한 네트워크 로그 모니터링을 사용하도록 설정한 경우 실행기 네트워크 트래픽을 모니터링할 수도 있습니다.
Azure VNET에서 GitHub 호스트 실행기 사용
Azure VNET에서 GitHub 호스트형 실행기를 사용하려면 Azure 리소스를 구성한 다음 GitHub에서 네트워킹 구성을 만들어야 합니다.
Enterprise 수준에서 Azure 개인 네트워킹을 구성하는 절차는 "엔터프라이즈의 GitHub 호스트형 실행기에 대한 개인 네트워킹 구성”을 참조하세요.