Acerca de los errores del Dependabot
El Dependabot levanta solicitudes de extracción para actualizar las dependencias. En función de la configuración del repositorio, Dependabot podría generar solicitudes de incorporación de cambios para las actualizaciones de versión o de seguridad. Administrarás estas solicitudes de la misma forma que cualquier otra solicitud de extracción, pero también hay comandos extra disponibles. Para más información sobre cómo habilitar las actualizaciones de dependencias de Dependabot, consulta "Configuración de actualizaciones de seguridad de Dependabot" y "Configuración de las actualizaciones de versiones de Dependabot".
Si existe algo que impida que el Dependabot levante una solicitud de cambios, esto se reporta como un error.
Nota: Dependabot no crea solicitudes de incorporación de cambios para repositorios inactivos. Para información sobre los criterios de inactividad, consulta "Sobre las actualizaciones de seguridad de Dependabot" y para información sobre las actualizaciones de seguridad y versiones, consulta "Acerca de las actualizaciones a la versión del Dependabot".
Para obtener más información sobre cómo solucionar problemas al ejecutar Dependabot en ejecutores de on GitHub Actions, vea "Acerca de Dependabot en ejecutores de Acciones de GitHub".
Investigar los errores de las Dependabot security updates
Cuando se bloquea al Dependabot y no puede crear una solicitud de cambios para arreglar una alerta del Dependabot, éste publica el mensaje de error en la alerta. La vista de Dependabot alerts muestra una lista de cualquier alerta que aún no se haya resuelto. Para acceder a la vista de alertas, haga clic en Dependabot alerts en la pestaña Security (Seguridad) del repositorio. Donde sea que se genere una solicitud de cambios que arregle una dependencia vulnerable, la alerta incluirá un enlace a dicha solicitud.

Hay varias razones por las cuales una alerta podría no tener un enlace a una solicitud de incorporación de cambios:
- No se han habilitado las Dependabot security updates en el repositorio.
- La alerta es para una dependencia transitoria o indirecta que no se definió explícitamente en un archivo de bloqueo.
- Un error bloqueó al Dependabot y éste no puede crear una solicitud de cambios.
Si existe un error que bloqueó al Dependabot y éste no puede crear una solicitud de cambios, puedes mostrar los detalles del error si das clic en la alerta.
Investigar los errores de las Dependabot version updates
Cuando se impide que Dependabot cree una solicitud de incorporación de cambios para actualizar una dependencia en un ecosistema, puede ver la lista de registros de trabajos para obtener más información sobre el error .
La lista de registros de trabajos es accesible desde el gráfico de dependencias de un repositorio. En el gráfico de dependencias, haga clic en la pestaña Dependabot y, a continuación, a la derecha del archivo de manifiesto afectado, haga clic en Trabajos de actualización recientes.
Para ver los archivos de registros completos de un trabajo determinado, a la derecha de la entrada de registro que le interesa, haga clic en ver registros.
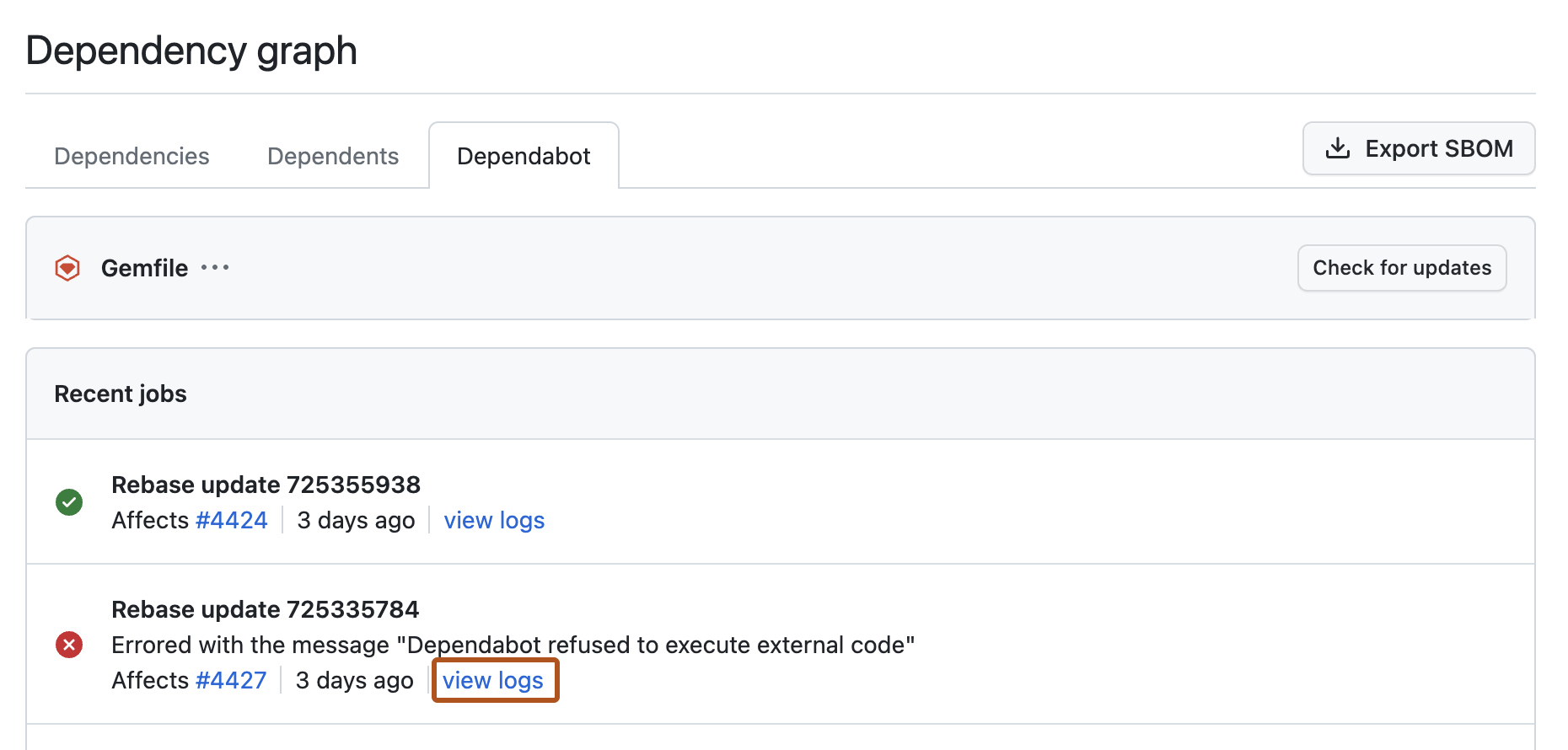
Para obtener más información, vea «Visualización de registros de trabajos de Dependabot».
Entender los errores del Dependabot
Las solicitudes de cambios para las actualizaciones de seguridad actúan para mejorar una dependencia vulnerable a la versión mínima que incluya un arreglo de la vulnerabilidad. Por el contrario, las solicitudes de cambios para las actualizaciones de versión actúan para mejorar una dependencia a la última versión que permite el paquete de archivos de manifiesto y de configuración del Dependabot. Como consecuencia, algunos errores son específicos de un tipo de actualización.
El Dependabot no puede actualizar la DEPENDENCIA a una versión no-vulnerable
Únicamente actualizaciones de seguridad. Dependabot no puede crear una solicitud de incorporación de cambios a fin de actualizar la dependencia vulnerable a una versión segura sin interrumpir otras dependencias del gráfico de dependencias para este repositorio.
Cada aplicación que tenga dependencias tiene una gráfica de dependencias, esto es, una gráfica acíclica dirigida de cada versión de paquete de la cual depende la aplicación directa o indirectamente. Cada vez que se actualiza una dependencia, esta gráfica debe resolverse o la aplicación no se compilará. Cuando un ecosistema tiene una gráfica de dependencias profunda y compleja, por ejemplo, npm y RubyGems, es a menudo imposible mejorar una sola dependencia sin mejorar todo el ecosistema.
La mejor forma de evitar este problema es mantenerse actualizado con los lanzamientos de versiones más recientes, por ejemplo, habilitando las actualizaciones de versión. Esto aumenta la probabilidad de que una vulnerabilidad en alguna dependencia pueda resolverse con una mejora simple que no afecte la gráfica de dependencias. Para más información, consulta "Configuración de las actualizaciones de versiones de Dependabot".
Dependabot intenta actualizar las dependencias sin una alerta
Únicamente actualizaciones de seguridad. Dependabot actualiza las dependencias transitivas definidas explícitamente como vulnerables para todos los ecosistemas. En el caso de npm, Dependabot generará una solicitud de incorporación de cambios que también actualiza la dependencia primaria si es la única manera de corregir la dependencia transitiva.
Por ejemplo, un proyecto con una dependencia de A versión ~2.0.0 que tiene una dependencia transitiva de B versión ~1.0.0 que se ha resuelto en 1.0.1.
my project
|
--> A (2.0.0) [~2.0.0]
|
--> B (1.0.1) [~1.0.0]
Si se publica una vulnerabilidad de seguridad para B versiones <2.0.0 y hay una revisión disponible en 2.0.0, Dependabot intentará actualizar B, pero se encontrará con que no es posible debido a la restricción implementada por A, que solo permite versiones vulnerables más bajas. Para corregir la vulnerabilidad, Dependabot buscará actualizaciones de la dependencia de A que permitan usar la versión fija de B.
Dependabot genera automáticamente una solicitud de incorporación de cambios que actualiza las dependencias transitivas primarias y secundarias bloqueadas.
Dependabot no puede cerrar una solicitud de incorporación de cambios abierta para una actualización que ya se ha aplicado en la rama predeterminada
Dependabot cerrará las solicitudes de incorporación de cambios para las actualizaciones de dependencias, una vez que detecte que estas actualizaciones se han confirmado en la rama predeterminada. Sin embargo, en raras circunstancias, la solicitud de incorporación de cambios puede permanecer abierta. Si observas que has confirmado una actualización de una dependencia manualmente y que la solicitud de incorporación de cambios para esa misma actualización sigue abierta, puedes usar uno de los siguientes comandos en un comentario en la solicitud de incorporación de cambios:
@dependabot recreateo@dependabot rebase.
Cualquier comentario desencadenará Dependabot para comprobar si la dependencia ya no es actualizable o vulnerable. Si Dependabot detecta que la solicitud de incorporación de cambios ya no es necesaria, cerrará la solicitud de incorporación de cambios en este caso concreto.
Para más información sobre los comandos de comentario Dependabot, consulta "Administrar las solicitudes de extracción para las actualizaciones de dependencia".
El Dependabot no puede actualizar a la versión requerida porque ya existe una solicitud de cambios abierta para la última versión
Únicamente actualizaciones de seguridad. Dependabot no creará una solicitud de incorporación de cambios a fin de actualizar la dependencia vulnerable a una versión segura porque ya hay una solicitud de incorporación de cambios abierta para actualizar esta dependencia. Verás éste error cuando se detecte una vulnerabilidad en una dependencia específica y ya exista una solicitud de cambios abierta para actualizar dicha dependencia a la última versión disponible.
Existen dos opciones: puedes revisar la solicitud de cambios abierta y fusionarla tan pronto como puedas garantizar que el cambio es seguro, o cerrar la solicitud de cambios y activar una solicitud nueva de actualización de seguridad. Para obtener más información, vea "Desencadenamiento manual de una solicitud de incorporación de cambios de Dependabot".
No se necesita ninguna actualización de seguridad, ya que la DEPENDENCIA ya no es vulnerable
Únicamente actualizaciones de seguridad. Dependabot no puede cerrar una solicitud de incorporación de cambios para actualizar una dependencia que no sea o haya dejado de ser vulnerable. Puede vea este error si los datos del gráfico de dependencias están obsoletos o cuando el gráfico de dependencias y Dependabot no coincidan en determinar si una versión determinada de una dependencia es vulnerable.
Para depurar el problema, se recomienda examinar primero el gráfico de dependencias del repositorio, revisar la versión que ha detectado para la dependencia y comprobar si la versión identificada coincide con lo que se usa en el repositorio.
Si sospecha que los datos del gráfico de dependencias no están actualizados, es posible que tenga que actualizar manualmente el gráfico de dependencias para el repositorio o investigar la información de la dependencia más adelante. Para obtener más información, vea «Solución de problemas del gráfico de dependencias».
Si puede confirmar que la versión de dependencia ya no es vulnerable, puede cerrar la solicitud de incorporación de cambios de Dependabot.
El Dependabot agotó el tiempo de espera durante su actualización
El Dependabot tardó más del límite de tiempo máximo permitido para valorar la actualización requerida y preparar una solicitud de cambios. Este error normalmente se ve únicamente en los repositorios de gran tamaño con muchos archivos de manifiesto, por ejemplo, en los proyectos de npm o yarn de un repositorio, que tienen cientos de archivos package.json. Las actualizaciones en el ecosistema de Composer también llevan más tiempo para su valoración y podrían exceder el tiempo de espera.
Es difícil tratar a este error. Si una actualización de versión agota el tiempo de espera, podría especificar las dependencias más importantes que se van a actualizar mediante el parámetro allow o, como alternativa, utilizar el parámetro ignore para excluir algunas de las dependencias de estas actualizaciones. El actualizar tu configuración podría permitir que el Dependabot revise la actualización de versión y genere la solicitud de cambios en el tiempo disponible.
Si una actualización de seguridad excede el tiempo de espera, puedes reducir la probabilidad de que esto suceda si mantienes las dependencias actualizadas, por ejemplo, habilitando las actualizaciones de versión. Para obtener más información, vea «Configuración de las actualizaciones de versiones de Dependabot».
El Dependabot no puede abrir más solicitudes de cambios
Hay un límite en la cantidad de solicitudes de cambios abiertas que el Dependabot puede generar. Cuando se llega a éste límite, no se podrán abrir más solicitudes de cambios y se reportará este error. La mejor forma de resolver este error es revisar y fusionar algunas de las solicitudes de cambios abiertas.
Hay límites separados para las solicitudes de cambios de actualización de seguridad y de versión, y esto es para que aquellas de actualización de versión no bloqueen la creación de las de actualización de seguridad. El límite para las solicitudes de cambios de actualizaciones de seguridad es de 10. De manera predeterminada, el límite de las actualizaciones de versión es 5, pero puede cambiarlo mediante el parámetro open-pull-requests-limit en el archivo de configuración. Para obtener más información, vea «Opciones de configuración para el archivo dependabot.yml».
La mejor forma de resolver este error es fusionar o cerrar algunas de las solicitudes de cambios existentes y activar una solicitud de cambios nueva manualmente. Para obtener más información, vea "Desencadenamiento manual de una solicitud de incorporación de cambios de Dependabot".
El Dependabot no puede resolver o acceder a tus dependencias
Si el Dependabot intenta verificar si las referencias de la dependencia necesitan actualizarse en un repositorio, pero no puede acceder a uno o más de los archivos referenciados, la operación fallará con el mensaje de error "Dependabot can't resolve your LANGUAGE dependency files". El tipo de error de la API es git_dependencies_not_reachable.
De forma similar, si el Dependabot no puede acceder a un registro de un paquete privado en el cual se ubica la dependencia, se generará alguno de los siguientes errores:
- "Dependabot can't reach a dependency in a private package registry" (Dependabot no puede acceder a una dependencia en un registro de paquete privado)
(Tipo de error de la API:private_source_not_reachable) - "Dependabot can't authenticate to a private package registry" (Dependabot no se puede autenticar en un registro de paquetes privado)
(Tipo de error de la API:private_source_authentication_failure) - "Dependabot timed out while waiting for a private package registry" (Dependabot agota el tiempo de espera mientras espera un registro de paquete privado)
(Tipo de error de la API:private_source_timed_out) - "Dependabot couldn't validate the certificate for a private package registry" (Dependabot no ha podido validar el certificado para un registro de paquete privado)
(Tipo de error de la API:private_source_certificate_failure)
Para permitir añ Dependabot actualizar las referencias de dependencia exitosamente, asegúrate que todas las dependencias referencias se hospeden en ubicaciones accesibles.
Únicamente actualizaciones de versiones. Cuando ejecutas actualizaciones de versión o de seguridad, algunos ecosistemas deberán poder resolver todas las dependencias de su fuente para verificar que las actualizaciones sean exitosas. Si tus archivos de manifiesto o de bloqueo contienen cualquier dependencia privada, el Dependabot deberá poder acceder a la ubicación en la que se hospedan dichas dependencias. Los propietarios de las organizaciones pueden otorgar acceso al Dependabot para los repositorios privados que contengan dependencias para un proyecto dentro de la misma organización. Para obtener más información, vea «Administrar la configuración de seguridad y análisis de su organización». Puede configurar el acceso a los registros privados en el archivo de configuración dependabot.yml de un repositorio. Para obtener más información, vea «Opciones de configuración para el archivo dependabot.yml». Adicionalmente, el Dependabot no es compatible con dependencias privadas de GitHub para todos los administradores de paquetes. Para obtener más información, vea «Acerca de las actualizaciones a la versión del Dependabot».
El Dependabot no puede agrupar un conjunto de dependencias en una única solicitud de cambios para Dependabot version updates.
Las opciones de configuración groups del archivo dependabot.yml se pueden aplicar a las actualizaciones de versión y a las actualizaciones de seguridad. Use la clave applies-to para especificar dónde (actualizaciones de versión o actualizaciones de seguridad) se aplica un conjunto de reglas de agrupación.
No se puede aplicar un único conjunto de reglas de agrupación a las actualizaciones de versión y a las actualizaciones de seguridad. En su lugar, si desea agrupar las actualizaciones de versiones y las actualizaciones de seguridad con los mismos criterios, debe definir dos conjuntos de reglas de agrupación con nombre por separado.
Al configurar las actualizaciones de versiones agrupadas, debe configurar grupos por ecosistema de paquetes. Para depurar el problema, te recomendamos que examines los registros. Para obtener información sobre cómo obtener acceso a los registros de un manifiesto, consulta "Investigación de errores con Dependabot version updates" más arriba.
Es posible que hayas creado grupos vacíos sin querer. Por ejemplo, esto sucede cuando se define un dependency-type en la clave allow para todo el trabajo.
allow:
dependency-type: production
# this restricts the entire job to production dependencies
groups:
development-dependencies:
dependency-type: "development"
# this group will always be empty
En este ejemplo, el Dependabot hará lo siguiente:
- Examinará la lista de dependencias y restringirá el trabajo a las dependencias usadas solo en
production. - Intentará crear un grupo denominado
development-dependencies, que es un subconjunto de esta lista reducida. - Descubrirá que el grupo
development-dependenciesestá vacío, ya que todas las dependencias dedevelopmentse quitaron en el paso 1. - Actualizará individualmente todas las dependencias que no están en el grupo. Puesto que el grupo de dependencias de producción está vacío, el Dependabot omitirá el grupo y creará una solicitud de incorporación de cambios independiente para cada dependencia.
Debes asegurarte de que las opciones de configuración no se cancelen entre sí y actualizarlas adecuadamente en el archivo de configuración.
Para obtener más información sobre la configuración de grupos para Dependabot version updates, consulta "Opciones de configuración para el archivo dependabot.yml".
El Dependabot no puede agrupar un conjunto de dependencias en una única solicitud de cambios para Dependabot security updates.
Las opciones de configuración groups del archivo dependabot.yml se pueden aplicar a las actualizaciones de versión y a las actualizaciones de seguridad. Use la clave applies-to para especificar dónde (actualizaciones de versión o actualizaciones de seguridad) se aplica un conjunto de reglas de agrupación. Compruebe que tiene la agrupación configurada para aplicar a las actualizaciones de seguridad. Si la clave applies-to no existe en un conjunto de reglas de agrupación en la configuración, las reglas de grupo solo se aplicarán de forma predeterminada a las actualizaciones de versión.
No se puede aplicar un único conjunto de reglas de agrupación a las actualizaciones de versión y a las actualizaciones de seguridad. En su lugar, si desea agrupar las actualizaciones de versiones y las actualizaciones de seguridad con los mismos criterios, debe definir dos conjuntos de reglas de agrupación con nombre por separado.
Para las actualizaciones de seguridad agrupadas, Dependabot usa las instrucciones siguientes para crear solicitudes de incorporación de cambios agrupadas.
- Dependabot agrupará las dependencias del mismo ecosistema de paquetes que se encuentran en directorios diferentes. La agrupación entre directorios solo se produce para directorios no configurados en el archivo
dependabot.yml. - Dependabot aplicará otras opciones de personalización pertinentes del archivo
dependabot.ymla las solicitudes de cambios para las actualizaciones de seguridad agrupadas. Las reglas de grupo configuradas en un archivodependabot.ymlinvalidarán la configuración de la interfaz de usuario para habilitar o deshabilitar las actualizaciones de seguridad agrupadas en el nivel de organización o repositorio. - Dependabot no agrupará las dependencias de diferentes ecosistemas de paquetes.
- Dependabot no agrupará las actualizaciones de seguridad con las actualizaciones de versión.
Para obtener más información, vea «Personalizar las actualizaciones de las dependencias» y «Sobre las actualizaciones de seguridad de Dependabot».
Dependabot no consigue actualizar una de las dependencias de una solicitud de incorporación de cambios agrupada
Hay diferentes técnicas de solución de problemas que puede usar para las actualizaciones de versión con errores y las actualizaciones de seguridad con errores.
Control de errores en actualizaciones de versiones agrupadas
Únicamente actualizaciones de versiones. Dependabot mostrará la actualización errónea en los registros, así como en el resumen del trabajo al final de los registros. Debes usar el comentario @dependabot recreate en la solicitud de incorporación de cambios para volver a compilar el grupo. Para obtener más información, vea «Administrar las solicitudes de extracción para las actualizaciones de dependencia».
Si la dependencia sigue sin actualizarse, debes usar la configuración exclude-patterns para que la dependencia se excluya del grupo. Dependabot generará una solicitud de incorporación de cambios independiente para actualizar la dependencia.
Si la dependencia sigue sin actualizarse, puede haber un problema con la propia dependencia, o con Dependabot para ese ecosistema específico.
Si deseas omitir las actualizaciones de la dependencia, debes realizar una de las acciones siguientes.
- Configura una regla
ignorepara la dependencia en el archivodependabot.yml. Para obtener más información, consulta "Opciones de configuración para el archivo dependabot.yml". - Usa el comando de comentario
@dependabot ignorepara la dependencia en la solicitud de incorporación de cambios para las actualizaciones agrupadas. Para obtener más información, vea «Administrar las solicitudes de extracción para las actualizaciones de dependencia».
Control de errores en actualizaciones de seguridad agrupadas
Únicamente actualizaciones de seguridad. Si se produce un error en una solicitud de incorporación de cambios agrupada para las actualizaciones de seguridad o no se puede combinar, se recomienda abrir manualmente las solicitudes de incorporación de cambios para aumentar las versiones de cambios importantes. Al actualizar manualmente un paquete que se incluye en una solicitud de incorporación de cambios agrupada, Dependabot volverá a base de la solicitud de incorporación de cambios para que no incluya el paquete actualizado manualmente.
Si deseas omitir las actualizaciones de la dependencia, debes realizar una de las acciones siguientes.
- Configura una regla
ignorepara la dependencia en el archivodependabot.yml. Para obtener más información, consulta "Opciones de configuración para el archivo dependabot.yml". - Usa el comando de comentario
@dependabot ignorepara la dependencia en la solicitud de incorporación de cambios para las actualizaciones agrupadas. Para obtener más información, vea «Administrar las solicitudes de extracción para las actualizaciones de dependencia».
Se produce un error en la integración continua (CI) en la solicitud de incorporación de cambios agrupada
Únicamente actualizaciones de versiones. Si el error se debe a una sola dependencia, debes usar la configuración exclude-patterns para que la dependencia se excluya del grupo. Dependabot generará una solicitud de incorporación de cambios independiente para actualizar la dependencia.
Si deseas omitir las actualizaciones de la dependencia, debes realizar una de las acciones siguientes.
- Configura una regla
ignorepara la dependencia en el archivodependabot.yml. Para obtener más información, consulta "Opciones de configuración para el archivo dependabot.yml". - Usa el comando de comentario
@dependabot ignorepara la dependencia en la solicitud de incorporación de cambios para las actualizaciones agrupadas. Para obtener más información, vea «Administrar las solicitudes de extracción para las actualizaciones de dependencia».
Si sigues viendo errores de CI, debes quitar la configuración de grupo para que Dependabot vuelva a generar solicitudes de incorporación de cambios individuales para cada dependencia. A continuación, debes comprobar y confirmar que la actualización de cada solicitud de incorporación de cambios individual funciona correctamente.
Activar una solicitud de cambios del Dependabot manualmente
Si desbloqueas al Dependabot, puedes activar manualmente un nuevo intento de crear una solicitud de cambios.
- Actualizaciones de seguridad: muestre la alerta de Dependabot que indica el error que ha corregido y haga clic en Crear actualización de seguridad de Dependabot .
- Actualizaciones de versión: en la pestaña Insights (Información) del repositorio, haga clic en Dependency graph (Gráfico de dependencias) y luego en la pestaña Dependabot. Haga clic en Last checked TIME ago (Última comprobación hace TIME) para ver el archivo de registro que Dependabot ha generado durante la última comprobación de actualizaciones de versión. Haga clic en Buscar actualizaciones.