关于拉取请求上的 code scanning 结果
在仓库中,如果 code scanning 被配置为拉取请求检查,则 code scanning 将检查拉取请求中的代码。 默认情况下,这仅限于针对默认分支的拉取请求,但是您可以在 GitHub Actions 或第三方 CI/CD 系统中更改此配置。
如果拉取请求中更改的代码行生成 code scanning 警报,则会在拉取请求上的以下位置报告警报。
- 检查拉取请求 中的结果
- 拉取请求的“对话”选项卡是拉取请求审查的一部分
- 拉取请求的“已更改的文件”选项卡
注意: 仅当警报标识的所有代码行都存在于拉取请求差异中时,Code scanning 才会在拉取请求中显示警报。 有关详细信息,请参阅“对代码扫描的 SARIF 支持”。
如果你拥有存储库的写入权限,可以在“安全性”选项卡上看到任何现有的 code scanning 警报。有关存储库警报的信息,请参阅“管理存储库的代码扫描警报”。
在 code scanning 配置为在每次推送代码时扫描的存储库中,code scanning 还会将结果映射到任何打开的拉取请求,并将警报作为注释添加到与其他拉取请求检查相同的位置。 有关详细信息,请参阅“自定义 代码扫描的高级设置”。
如果拉取请求针对使用 code scanning 的受保护分支,并且存储库所有者已配置所需的状态检查,则“Code scanning 结果”检查必须先通过,然后才能合并拉取请求。 有关详细信息,请参阅“关于受保护分支”。
关于 code scanning 作为拉取请求检查
有许多选项可将 code scanning 配置为拉取请求检查,因此每个存储库的确切配置会有所不同,有些存储库还会有多个检查。
Code scanning 结果检查
对于 code scanning 的所有配置,包含 code scanning 结果的检查为:Code scanning 结果。 所使用的每个分析工具的结果将单独显示。 拉取请求中更改的代码行上的任何新警报都显示为注释。
要查看所分析分支的完整警报集,请单击“查看所有分支警报”。 这将打开完整的警报视图,你可以在其中按类型、严重性、标记等筛选分支上的所有警报。有关详细信息,请参阅“管理存储库的代码扫描警报”。

Code scanning 结果检查失败
如果 code scanning 结果检查发现严重性为 error``critical 或 high 的问题,检查将失败并在检查结果中报告错误。 如果 code scanning 发现的所有结果的严重性都较低,则警报将被视为警告或通知,检查成功。

你可以通过指定会导致拉取请求检查失败的严重级别和安全严重性来覆盖仓库设置中的默认行为。 有关详细信息,请参阅“自定义 代码扫描的高级设置”。
其他 code scanning 检查
根据您的配置,您可能会看到在配置了 code scanning 的拉取请求上运行其他检查。 这些通常是分析代码或上传 code scanning 结果的工作流程。 当分析出现问题时,这些检查对于故障排除非常有用。
例如,如果存储库使用 CodeQL 分析工作流程,则在结果检查运行之前,将针对每种语言运行 CodeQL / Analyze (LANGUAGE) 检查。 如果存在配置问题,或者拉取请求中断了分析编译的语言(例如 C/C++、C#、 Go、 Java 以及 Swift)的构建,则分析检查可能会失败。
与其他拉取请求检查一样,你可以在“检查”选项卡上查看检查失败的完整详细信息。有关配置和故障排除的详细信息,请参阅“自定义 代码扫描的高级设置”或“代码扫描疑难解答”。
查看拉取请求上的警报
通过查看“对话”选项卡,可以看到拉取请求中引入的更改差异中的任何 code scanning 警报。Code scanning 会发布拉取请求审查,该审查将每个警报作为触发警报的代码行上的注释显示。 可以对警报进行注释、关闭警报并直接从注释中查看警报的路径。 可以通过单击“显示更多详细信息”链接来查看警报的完整详细信息,该链接将带你进入警报详细信息页面。

您还可以查看所有 code scanning 警报 ,这些警报位于拉取请求的“文件已更改”选项卡。
如果在拉取请求中添加了新的代码扫描配置,则会在拉取请求上看到一条注释,该注释会将你定向到存储库的“安全”选项卡,以便你查看拉取请求分支上的所有警报。 有关查看存储库警报的详细信息,请参阅“管理存储库的代码扫描警报”。
如果您拥有仓库的写入权限,则某些注释将包含警报额外上下文的链接。 在上例中,可以在 CodeQL 分析中单击“用户提供的值”,以查看不受信任的数据进入数据流的位置(这称为源)。 在此例中,还可以通过单击“显示路径”来查看从源到使用数据的代码(池)的完整路径。 这样就很容易检查数据是否不受信任,或者分析是否无法识别源与池之间的数据净化步骤。 有关使用 CodeQL 分析数据流的信息,请参阅“关于数据流分析”。
要查看有关警报的更多信息,拥有写入权限的用户可单击注释中所示的“显示更多详情”链接。 这允许您在警报视图中查看工具提供的所有上下文和元数据。 在下例中,您可以查看显示问题的严重性、类型和相关通用缺陷枚举 (CWE) 的标记。 该视图还显示哪个提交引入了问题。
警报页面上的状态和详细信息仅反映存储库默认分支上的警报状态,即使警报存在于其他分支中也是如此。 可以在警报页右侧的“受影响的分支”部分查看非默认分支上的警报状态。 如果默认分支中不存在警报,则警报的状态将显示为“在拉取请求中”或“在分支中”,并将变为灰色。
在警报的详细视图中,有些 code scanning 工具(例如 CodeQL 分析)还包括问题描述和“显示更多”链接以指导你如何修复代码。

对拉取请求中的警报进行注释
可以对拉取请求上出现的任何 code scanning 警报 进行注释。 警报在拉取请求的“对话”选项卡中显示为注释,作为拉取请求审查的一部分,也显示在“已更改的文件”选项卡中。
可以选择要求拉取请求中的所有对话(包括 code scanning 警报上的对话),以在合并拉取请求之前被解析。 有关详细信息,请参阅“关于受保护分支”。
修复拉取请求上的警报
任何对拉取请求具有推送权限的人都可以修复在该拉取请求上已识别的 code scanning 警报。 如果将更改提交到拉取请求,这将触发拉取请求检查的新运行。 如果您的更改修复了问题,则警报将被关闭,注释将被删除。
忽略拉取请求上的警报
关闭警报的另一种办法是忽略它。 您可以忽略您认为不需要修复的警报。 例如,仅用于测试的代码中有错误,或者修复错误的工作超过改进代码的潜在益处。 如果你拥有存储库的写入权限,则“关闭警报”按钮在代码注释和警报摘要中可用。 单击“关闭警报”时,系统会提示你选择关闭警报的原因。
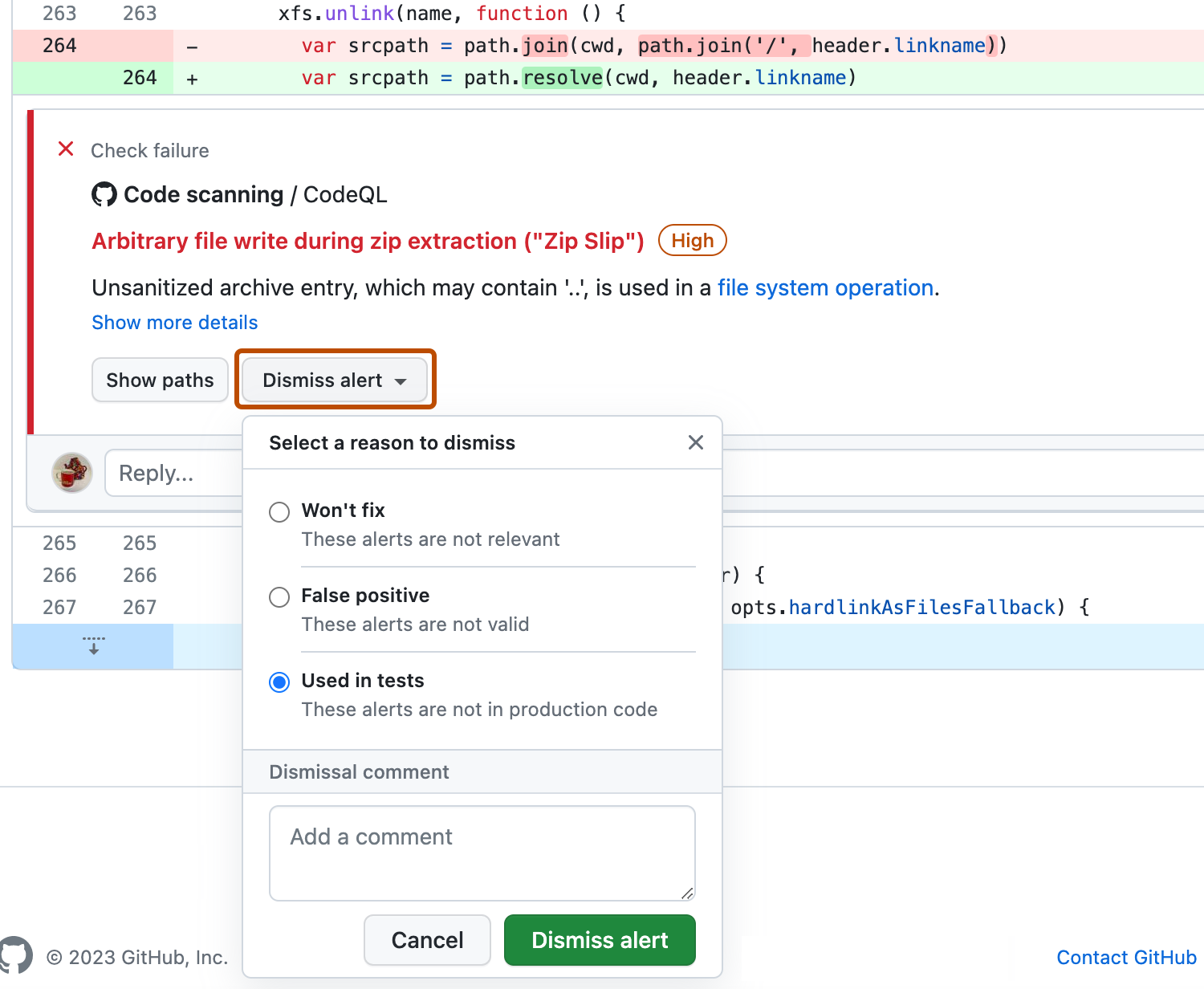
alerts/{alert_number} 终结点的 dismissed_comment 中。 有关详细信息,请参阅“适用于代码扫描的 REST API 终结点”。
如果将 CodeQL 警报作为误报予以忽略,例如因为代码使用了不受支持的清理库,请考虑参与 CodeQL 存储库并改进分析。 有关 CodeQL 的详细信息,请参阅“参与 CodeQL”。
有关消除警报的详细信息,请参阅“管理存储库的代码扫描警报”。