After you configure 2FA via a TOTP mobile app, you can add a security key that supports the FIDO U2F standard to use for two-factor authentication on GitHub Enterprise.
Note: FIDO U2F authentication is currently only available for the Chrome browser.
Warning for users in organizations that require two-factor authentication:
- If you're a member or outside collaborator to a private repository of an organization that requires two-factor authentication, you must leave the organization before you can disable 2FA on your GitHub Enterprise instance.
- If you disable 2FA you will automatically lose access to the organization and any private forks you have of the organization's private repositories. To regain access to the organization and your forks, re-enable two-factor authentication and contact an organization owner.
- You must have already configured 2FA via a TOTP mobile app.
- Ensure that you have a FIDO U2F compatible security key inserted into your computer.
 In the upper-right corner of any page, click your profile photo, then click Settings.
In the upper-right corner of any page, click your profile photo, then click Settings.
 In the user settings sidebar, click Security.
In the user settings sidebar, click Security.
 Under two-factor authentication, click Edit.
Under two-factor authentication, click Edit.
 Under Security keys, click Register new device.
Under Security keys, click Register new device.
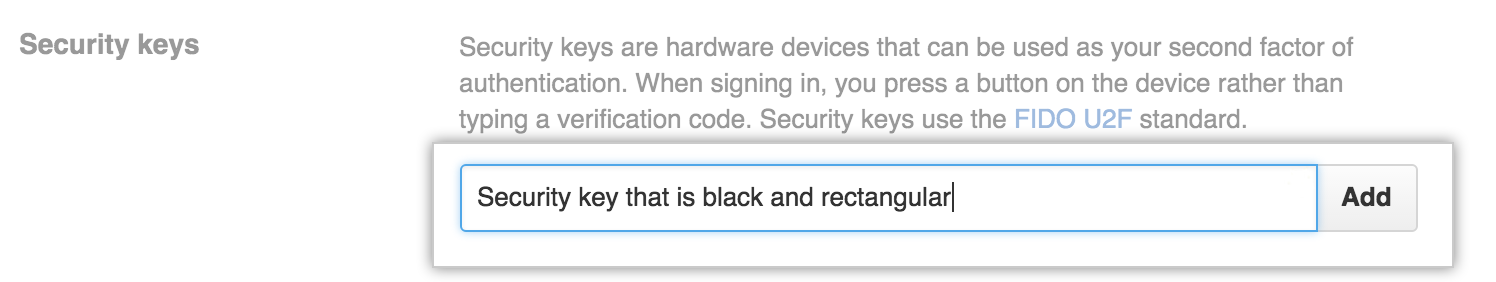 Type a nickname for the security key, then click Add.
Type a nickname for the security key, then click Add.
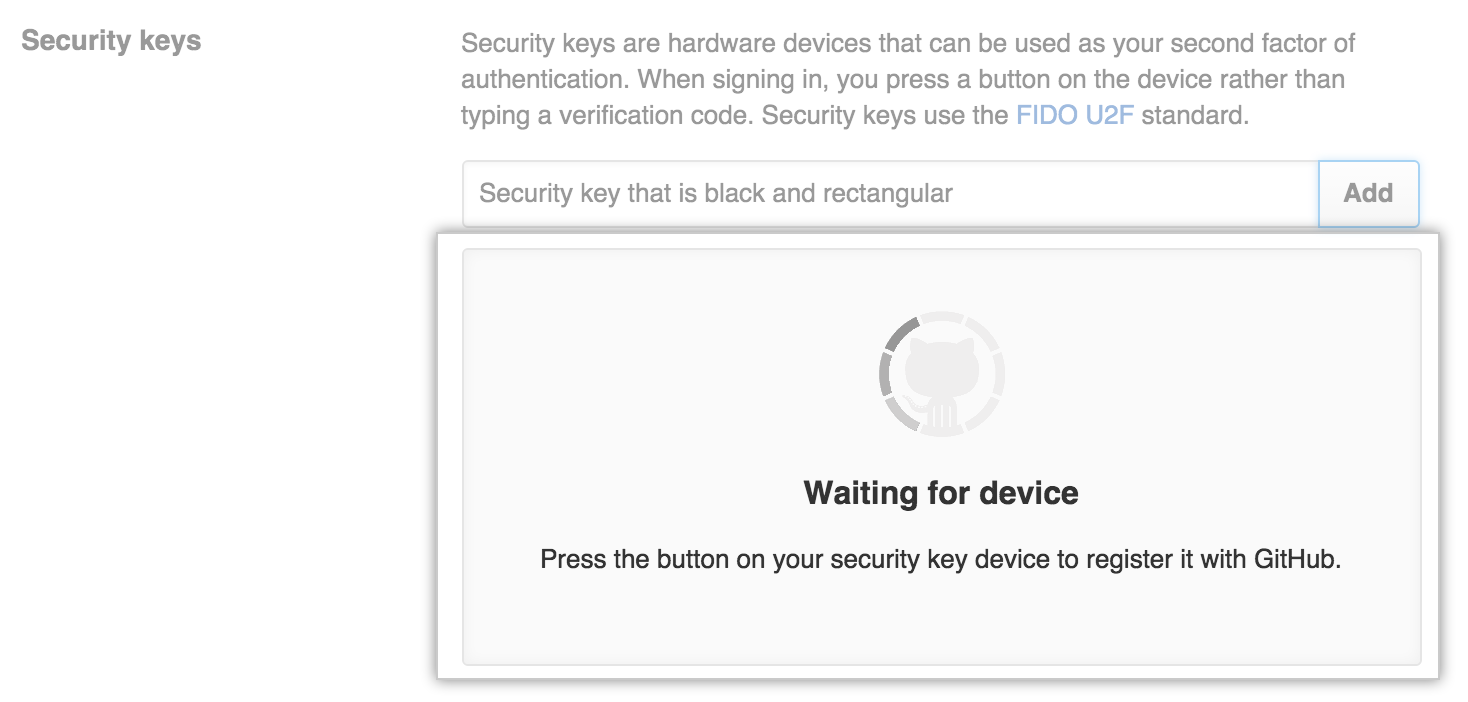 When prompted, touch your security key to have it authenticate against GitHub Enterprise.
When prompted, touch your security key to have it authenticate against GitHub Enterprise.
- If you're authenticating to GitHub Enterprise on an Android phone, you can use your FIDO U2F compatible security key and Google Authenticator to sign into your account with Near Field Communication (NFC).
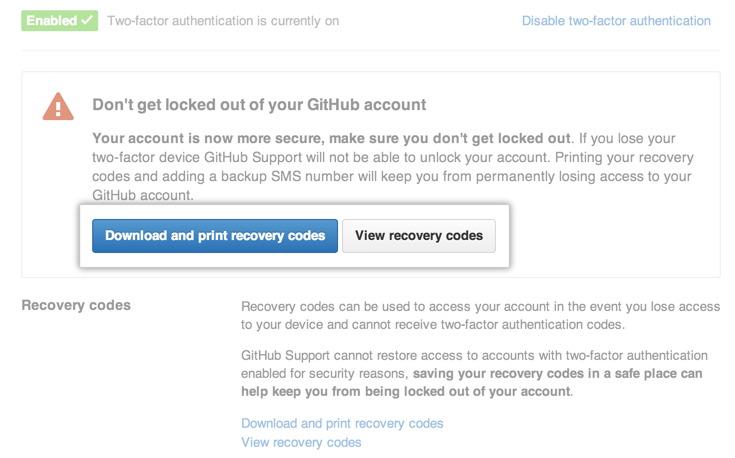 Download your recovery codes and save them in a safe place, such as a password manager. Your recovery codes are to be used in the event you lose access to your account.
Download your recovery codes and save them in a safe place, such as a password manager. Your recovery codes are to be used in the event you lose access to your account.
After 2FA has been enabled and you've saved your recovery codes, we recommend you sign out and back in to your account. In case of problems, such as a forgotten password or typo in your email address, you can use recovery codes to access your account and correct the problem.