Any Admin user can initiate an installation-wide SSH key audit. Once initiated, it disables all existing SSH keys and forces users to approve or reject them before they're able to clone/pull/push to any repositories. This is useful in situations where an employee or contractor leaves the company and you need to ensure that all keys are verified.
Initiating an Audit
You can initiate an SSH Key Audit from the "All users" tab of the Admin Tools dashboard:

After you click the "Start Public Key Audit" button, you'll be taken to a confirmation screen explaining what will happen next:
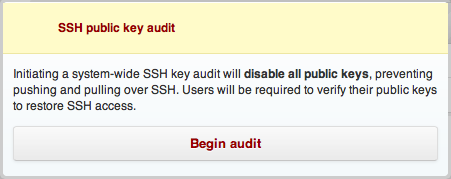
After you click the new "Start Public Key Audit" button, all SSH keys are invalidated and will require approval. You'll see a notification indicating the audit has begun.
What Users See
If a user attempts to perform any git operation over SSH, it will fail and provide them with the following message:
ERROR: Hi username. We're doing an SSH key audit. Please visit http(s)://hostname/settings/ssh/audit/2 to approve this key so we know it's safe. Fingerprint: ed:21:60:64:c0:dc:2b:16:0f:54:5f:2b:35:2a:94:91 fatal: The remote end hung up unexpectedly
When they follow the link, they're asked to approve the keys on their account:
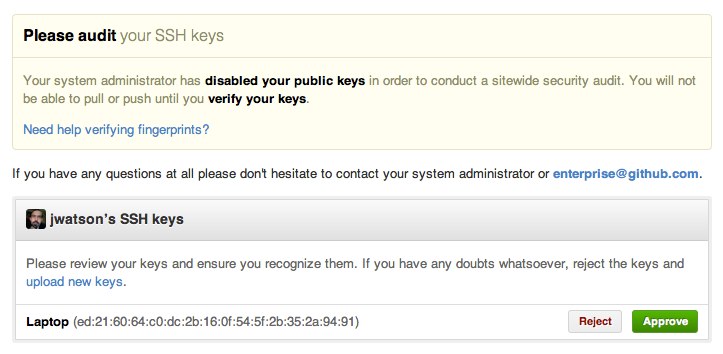
After they approve or reject their keys, they'll be able interact with repositories as usual.
Other SSH Key-related Improvements
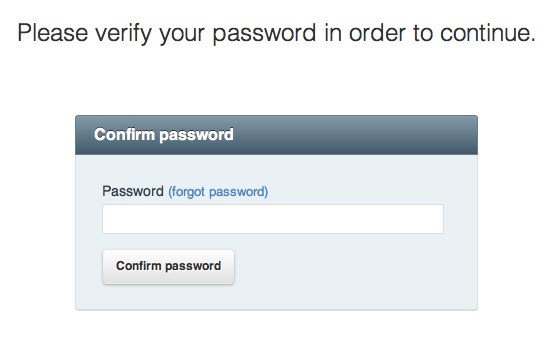
New users will be prompted for their password when adding an SSH key:
When a user adds a key, they'll receive a notification email that will look something like this:
The following SSH key was added to your account:
[title]
ed:21:60:64:c0:dc:2b:16:0f:54:5f:2b:35:2a:94:91
If you believe this key was added in error, you can remove the key and disable access at the following location:
http(s)://[hostname]/settings/ssh
Questions
If you have any questions about this process, please feel free to contact us.
