关于 secret scanning 警报页
在为存储库启用 secret scanning 或将提交推送到启用了 secret scanning 的存储库时,GitHub 会扫描内容,以查找与服务提供商定义的模式以及企业、组织或存储库中定义的任何自定义模式匹配的机密。
当 secret scanning 检测到机密时,GitHub 将生成警报。 GitHub 在存储库的“安全性”选项卡中显示警报。
为了帮助你更有效地对警报进行会审,GitHub 将警报分为两个列表:
- 高置信度警报。
- 其他警报。
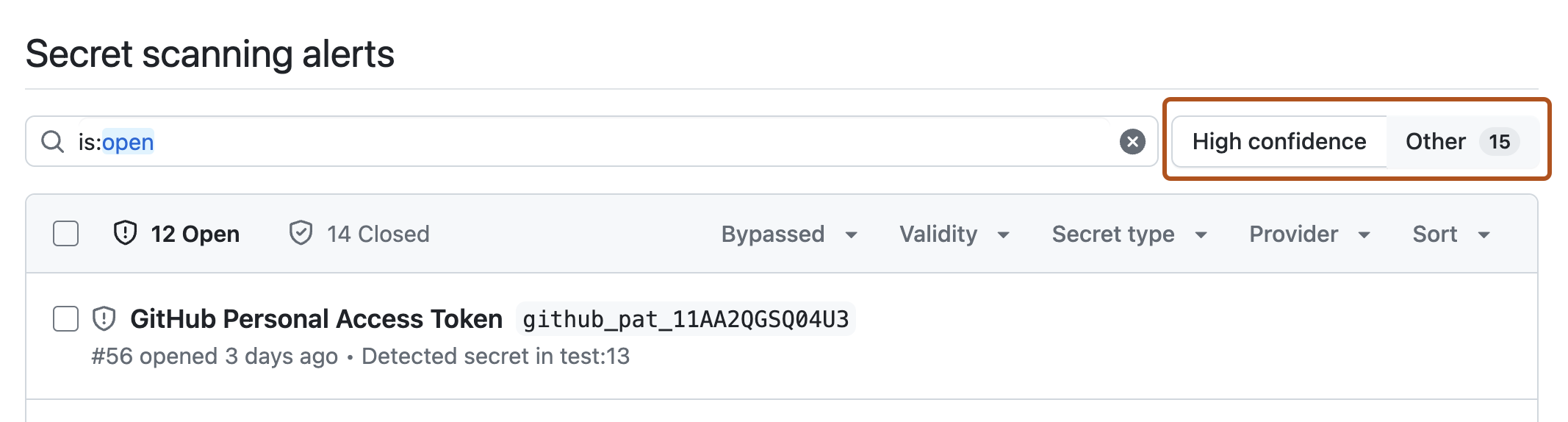
高置信度警报列表
“高置信度”警报列表显示与支持的模式和指定的自定义模式相关的警报。 此列表始终是警报页面的默认视图。
“其他”警报列表
“其他”警报列表显示与非提供程序模式(如私钥)相关的警报,或使用 AI 检测到的通用机密(如密码)。 这些类型警报的误报率较高。
此外还显示属于以下类别的警报:
- 每个存储库的数量限制为 5000 个警报(这包括打开和关闭的警报)。
- 不显示在安全概览的摘要视图中,仅在“Secret scanning”视图中显示。
- 对于非提供程序模式 ,仅在 GitHub 上显示前五个检测到的位置,对于 AI 检测到的通用机密 ,仅显示第一个检测到的位置。
若要让 GitHub 扫描非提供程序模式 和通用机密 ,必须为存储库或组织启用 。 有关详细信息,请参阅“为存储库配置机密扫描”和“启用 AI 支持的通用机密检测”。
查看警报
-
在 GitHub.com 上,导航到存储库的主页。
-
在存储库名称下,单击“ 安全性”。 如果看不到“安全性”选项卡,请选择 下拉菜单并单击“安全性” 。

-
在左边栏的“漏洞警报”下,单击“Secret scanning”。
-
(可选)切换到“其他”警报,可查看非提供程序模式的警报,或使用 AI 检测到的通用机密的警报。
-
在“Secret scanning”下,单击要查看的警报。
注意:只有对包含已泄露机密的存储库具有管理员权限的人员才能查看安全警报详细信息和警报的令牌元数据。 企业所有者可以出于此目的请求对存储库的临时访问权限。
筛选警报
可将各种筛选器应用于警报列表,帮助找到你要查看的警报。 可以使用警报列表上方的下拉菜单,或在搜索栏中输入表中列出的限定符。
| Qualifier | 说明 |
|---|---|
is:open | 显示打开的警报。 |
is:closed | 显示关闭的警报。 |
bypassed: true | 显示已绕过推送保护的机密的警报。 有关详细信息,请参阅“存储库和组织的推送保护”。 |
validity:active | 显示仍处于活动状态的机密的警报。 有关有效性状态的详细信息,请参阅“检查机密的有效性”。 |
validity:inactive | 显示不再处于活动状态的机密的警报。 |
validity:unknown | 显示有效性状态未知的机密的警报。 |
secret-type:SECRET-NAME | 显示特定机密类型的警报,例如 secret-type:github_personal_access_token。 有关支持的机密类型的列表,请参阅“机密扫描模式”。 |
provider:PROVIDER-NAME | 显示特定提供程序的警报,例如 provider:github。 有关支持的合作伙伴的列表,请参阅“机密扫描模式”。 |
confidence:high | 显示与支持的机密和自定义模式相关的高置信度机密的警报。 有关支持的高置信度模式的列表,请参阅“机密扫描模式”。 |
confidence:other | 显示非提供程序模式(如私钥)的警报,或使用 AI 检测到的通用机密(如密码)的警报。 有关支持的非提供程序模式的列表,请参阅“机密扫描模式”。 有关 AI 检测到的通用机密的详细信息,请参阅“关于使用机密扫描检测通用机密”。 |
评估警报
有一些其他功能可以帮助你评估警报,以便更好地排列警报优先级和管理警报。 可以:
- 检查机密的有效性,了解机密是否仍处于活动状态。 有关详细信息,请参阅“检查机密的有效性”。
- 执行“按需”验证检查,以获取最新的验证状态。 有关详细信息,请参阅“执行按需有效性检查”。
- 查看令牌的元数据。 仅适用于 GitHub 令牌。 例如查看上次使用令牌的时间。 有关详细信息,请参阅“查看 GitHub 令牌元数据"。
检查机密的有效性
注意: 合作伙伴模式的验证检查目前为 beta 版,可能会发生更改。
验证检查让您知道哪些机密属于 active 或 inactive 机密,帮助你排列 警报优先级。 active 机密是仍可能被利用的机密,因此应该优先审查和修正它们的警报。
默认情况下,GitHub 检查 GitHub 令牌的有效性,并在警报视图中显示令牌的验证状态。
另外,还可以选择为合作伙伴模式启用验证检查。 启用后,GitHub 将定期检查已检测到的凭据的有效性,方法是将机密直接发送到提供程序,作为 GitHub 的正式机密扫描伙伴关系计划的一部分。 GitHub 通常会发出 GET 请求,以检查凭据的有效性,挑选最不易入侵的终结点,并选择不返回任何个人信息的终结点。
GitHub 在警报视图中显示机密的验证状态。
| 有效期 | 结果 |
|---|---|
| 活动机密 | GitHub 确认此机密处于活动状态 |
| 活动机密 | GitHub 向此机密的提供者进行了核实,发现此机密处于活动状态 |
| 可能处于活动状态的机密 | GitHub 尚不支持对此令牌类型进行验证检查 |
| 可能处于活动状态的机密 | GitHub 无法验证此机密 |
| 机密显示为非活动状态 | 应确保未发生未经授权的访问 |
GitHub.com 上所有类型的存储库都提供针对合作伙伴模式的有效性检查。 若要使用此功能,必须具有 GitHub Advanced Security 的授权许可。
有关如何为合作伙伴模式启用验证检查的信息,请参阅“AUTOTITLE”,有关当前支持哪些合作伙伴模式的信息,请参阅“机密扫描模式”。
可以使用 REST API 检索每个令牌的最新验证状态的列表。 有关详细信息,请参阅 REST API 文档中的“适用于机密扫描的 REST API 终结点”。 还可以使用 Webhook 来通知与 secret scanning 警报相关的活动。 有关详细信息,请参阅“Webhook 事件和有效负载”中的 secret_scanning_alert 事件。
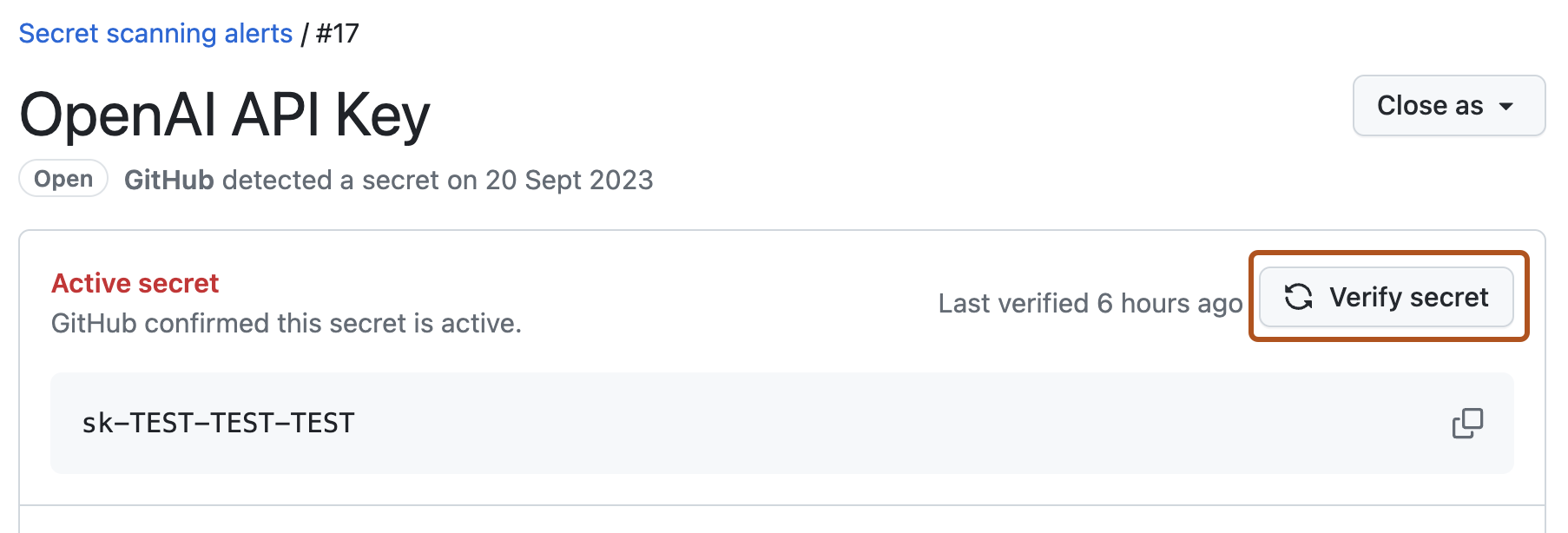
执行按需验证检查
如果为存储库启用了合作伙伴模式的验证检查,则可通过单击警报视图中的 “验证机密”****,对任何受支持的机密执行“按需”验证检查。 GitHub 将模式发送给相关合作伙伴,并在警报视图中显示机密的验证状态。
查看 GitHub 令牌元数据
注意:GitHub 令牌的元数据目前为公共 beta 版本,可能会有变动。
在活动的 GitHub 令牌警报视图中,可以查看有关令牌的某些元数据。 此元数据可以帮助你识别令牌,并确定要采取的修正步骤。
令牌(如personal access token和其他凭据)被视为个人信息。 有关使用 GitHub令牌的详细信息,请参阅 GitHub 的隐私声明和可接受的使用政策。
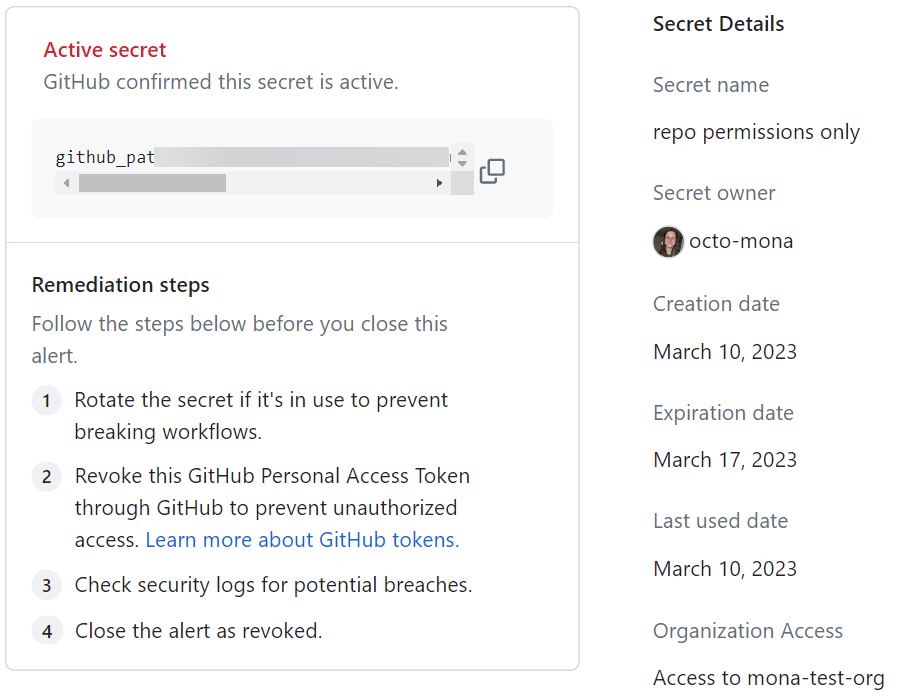
GitHub 令牌的元数据可用于任何启用了机密扫描的存储库的活动令牌。 如果令牌已被撤销或无法验证其状态,则元数据将不可用。 GitHub 会自动撤销公共存储库中的 GitHub 令牌,因此公共存储库中 GitHub 令牌的元数据极有可能不可用。 以下元数据可用于活动的 GitHub 令牌:
| 元数据 | 描述 |
|---|---|
| 机密名称 | GitHub 令牌的创建者为该令牌提供的名称 |
| 机密所有者 | 令牌所有者的 GitHub 句柄 |
| 创建时间 | 令牌的创建日期 |
| 过期日期 | 令牌的过期日期 |
| 上次使用时间 | 上次使用令牌的日期 |
| 访问 | 令牌是否具有组织访问权限 |
只有对包含已泄露机密的存储库具有管理员权限的人员才能查看安全警报详细信息和警报的令牌元数据。 企业所有者可以出于此目的请求对存储库的临时访问权限。如果授予访问权限,GitHub 将通知包含已泄露机密的存储库的所有者,在存储库所有者和企业审核日志中报告该操作,并将访问权限启用 2 小时。有关详细信息,请参阅“访问企业中用户拥有的存储库”。
修复警报
只要密码被提交到仓库,便应视为受到威胁。 GitHub 建议对受到威胁的密码执行以下操作:
- 对于受到威胁的 GitHub personal access token,请删除受到威胁的令牌,创建新令牌,然后更新使用旧令牌的任何服务。 有关详细信息,请参阅“管理个人访问令牌”。
- 如果组织属于企业帐户,请标识已泄露令牌对企业资源采取的任何操作。 有关详细信息,请参阅“标识由访问令牌执行的审核日志事件”。
- 对于所有其他机密,请先确认提交到 GitHub Enterprise Cloud 的机密是有效的。 如果有效,请创建新机密,更新使用旧机密的所有服务,然后删除旧机密。
注意:如果在 GitHub.com 上的公共存储库中检测到机密,并且该机密也与合作伙伴模式匹配,则会生成警报,并将潜在的机密报告给服务提供商。 有关合作伙伴模式的详细信息,请参阅“机密扫描模式”。
关闭警报
-
在 GitHub.com 上,导航到存储库的主页。
-
在存储库名称下,单击“ 安全性”。 如果看不到“安全性”选项卡,请选择 下拉菜单并单击“安全性” 。

-
在左边栏的“漏洞警报”下,单击“Secret scanning”。
-
在“Secret scanning”下,单击要查看的警报。
-
若要消除警报,请选择“关闭原因”下拉菜单,然后单击原因以解决警报。

-
(可选)在“注释”字段中,添加消除注释。 消除操作注释将添加到警报时间线,可在审核和报告期间用作理由。 可以在警报时间线中查看所有已消除警报和消除注释的历史记录。 还可以使用 Secret scanning API 检索或设置注释。 注释包含在
resolution_comment字段中。 有关详细信息,请参阅 REST API 文档中的“适用于机密扫描的 REST API 终结点”。 -
单击“关闭警报”。
配置 机密扫描警报
的通知
增量扫描和历史扫描的通知不同。
增量扫描
当检测到新的机密时,GitHub Enterprise Cloud 会根据用户的通知首选项,通知对存储库安全警报具有访问权限的所有用户。 这些用户包括:
- 存储库管理员
- 安全管理员
- 拥有自定义角色(具有读取/写入访问权限)的用户
- 组织所有者和企业所有者(如果他们是机密泄露的存储库的管理员)
注意:意外提交机密的提交作者将收到通知(无论其通知首选项如何)。
你将收到电子邮件通知,前提是:
- 你正在监视存储库。
- 你已启用存储库上“所有活动”或自定义“安全警报”的通知。
- 在通知设置中,在“订阅”下,然后在“监视”下,你已选择通过电子邮件接收通知。
-
在 GitHub.com 上,导航到存储库的主页。
-
若要开始监视存储库,请选择“监视”。

-
在下拉菜单中,单击“所有活动”。 或者,若要仅订阅安全警报,请单击“自定义”,然后单击“安全警报”。
-
导航到个人帐户的通知设置。 这些可在 https://github.com/settings/notifications 中找到。
-
在通知设置页上,在“订阅”下,然后在“正在监视”下,选择“通知我”下拉列表。
-
选择“电子邮件”作为通知选项,然后单击“保存”。

有关设置通知首选项的详细信息,请参阅“管理存储库的安全和分析设置”和“为单个存储库配置监视设置”。
历史扫描
对于历史扫描,GitHub Enterprise Cloud 通知以下用户:
- 组织所有者、企业所有者和安全管理者 - 每当历史扫描完成时,即使找不到任何机密,也会发送通知。
- 存储库管理员、安全管理者和拥有自定义角色(具有读/写访问权限)的用户 - 每当历史扫描检测到机密时,根据他们的通知首选项发送通知。
我们不会通知提交作者。
有关设置通知首选项的详细信息,请参阅“管理存储库的安全和分析设置”和“为单个存储库配置监视设置”。
审核对机密扫描警报的响应
可以使用 GitHub 工具审核为响应secret scanning警报而执行的操作。 有关详细信息,请参阅“审核安全警报”。