About management of security and analysis settings
GitHub can help you to secure the repositories in your organization. You can manage the security and analysis features for all existing or new repositories that members create in your organization. Organizations that use GitHub Enterprise Cloud with a license for GitHub Advanced Security can also manage access to these features. For more information, see the GitHub Enterprise Cloud documentation.
Note: You can't disable some security and analysis features that are enabled by default for public repositories.
You can quickly enable security features at scale with the GitHub-recommended security configuration, a collection of security enablement settings you can apply to repositories in an organization. You can then further customize GitHub Advanced Security features at the organization level with global settings. See "About enabling security features at scale."
Note: Security configurations and global settings are in beta and subject to change.
If you enable security and analysis features, GitHub performs read-only analysis on your repository.
Displaying the security and analysis settings
-
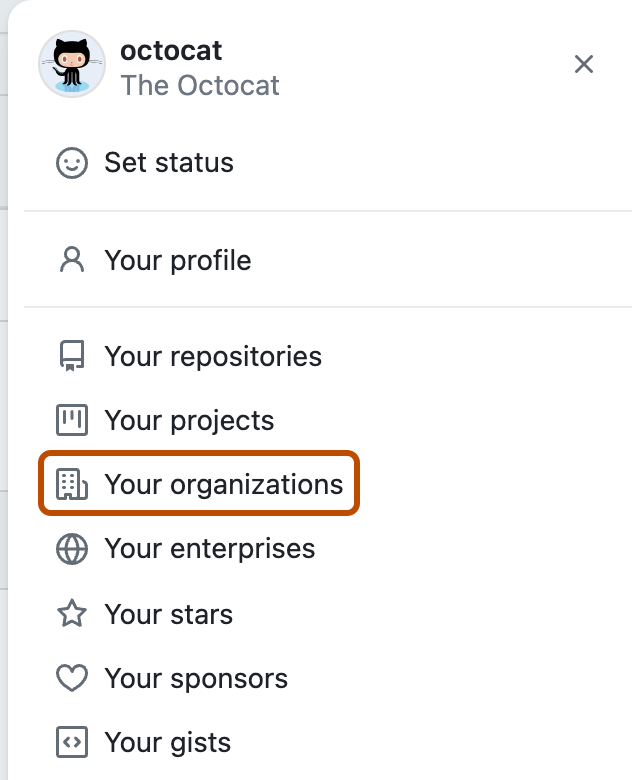
In the upper-right corner of GitHub.com, select your profile photo, then click Your organizations.
-
Next to the organization, click Settings.
-
In the "Security" section of the sidebar, click Code security and analysis.
Note
If your organization is enrolled in the security configurations and global settings public beta, instead of "Code security and analysis", you will see a Code security dropdown menu. You can manage your repository-level security settings with security configurations, and your organization-level security settings with global settings. See "Applying the GitHub-recommended security configuration in your organization" and "Configuring global security settings for your organization."
The page that's displayed allows you to enable or disable all security and analysis features for the repositories in your organization.
Enabling or disabling a feature for all existing repositories
You can enable or disable features for all repositories. The impact of your changes on repositories in your organization is determined by their visibility:
- Private vulnerability reporting - Your changes affect public repositories only.
- Dependency graph - Your changes affect only private repositories because the feature is always enabled for public repositories.
- Dependabot alerts - Your changes affect all repositories.
- Dependabot security updates - Your changes affect all repositories.
- Secret scanning - Your changes affect public repositories and public npm packages these repositories may depend on. This option controls whether or not secret scanning alerts for users are enabled. Secret scanning alerts for partners always runs on all public repositories.
- Code scanning - Your changes affect public repositories. For information about eligible repositories, see "Configuring default setup for code scanning at scale." For repositories that are not eligible for default setup, you can configure advanced setup at the repository level. For more information, see "Configuring advanced setup for code scanning."
-
Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
-
Under "Code security and analysis", to the right of the feature, click Disable all or Enable all to display a confirmation dialog box.
-
Review the information in the dialog box.
-
Optionally, if you are enabling private vulnerability reporting, dependency graph, or Dependabot, select Enable by default for new private repositories.

-
When you are ready to make the changes, click Disable FEATURE or Enable FEATURE to disable or enable the feature for all the repositories in your organization.
-
Optionally, in your feature's section of the security and analysis settings, select additional enablement settings. Additional enablement settings may include:
- Automatic enablement for a specific type of repository
- Feature-specific settings, such as recommending the extended query suite for code scanning default setup throughout your organization, or automatic secret validation for secret scanning
Notes:
- If you disable CodeQL code scanning for all repositories this change is not reflected in the coverage information shown in security overview for the organization. The repositories will still appear to have code scanning enabled in the "Security Coverage" view.
- Enabling code scanning for all eligible repositories in an organization will not override existing code scanning configurations. For information on configuring default setup with different settings for specific repositories, see "Configuring default setup for code scanning."
When you enable one or more security and analysis features for existing repositories, you will see any results displayed on GitHub within minutes:
- All the existing repositories will have the selected configuration.
- New repositories will follow the selected configuration if you've enabled the checkbox for new repositories.
- We use the permissions to scan for manifest files to apply the relevant services.
- If enabled, you'll see dependency information in the dependency graph.
- If enabled, GitHub will generate Dependabot alerts for vulnerable dependencies or malware.
- If enabled, Dependabot security updates will create pull requests to upgrade vulnerable dependencies when Dependabot alerts are triggered.
Enabling or disabling a feature automatically when new repositories are added
- Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
- Under "Code security and analysis", locate the feature, enable or disable the feature by default for new repositories, or all new private repositories, in your organization.
Allowing Dependabot to access private dependencies
Dependabot can check for outdated dependency references in a project and automatically generate a pull request to update them. To do this, Dependabot must have access to all of the targeted dependency files. Typically, version updates will fail if one or more dependencies are inaccessible. For more information, see "About Dependabot version updates."
By default, Dependabot can't update dependencies that are located in private repositories, or private package registries. However, if a dependency is in a private GitHub repository within the same organization as the project that uses that dependency, you can allow Dependabot to update the version successfully by giving it access to the host repository.
If your code depends on packages in a private registry, you can allow Dependabot to update the versions of these dependencies by configuring this at the repository level. You do this by adding authentication details to the dependabot.yml file for the repository. For more information, see "Configuration options for the dependabot.yml file."
To allow Dependabot to access a private GitHub repository:
-
Go to the security and analysis settings for your organization. For more information, see "Displaying the security and analysis settings."
-
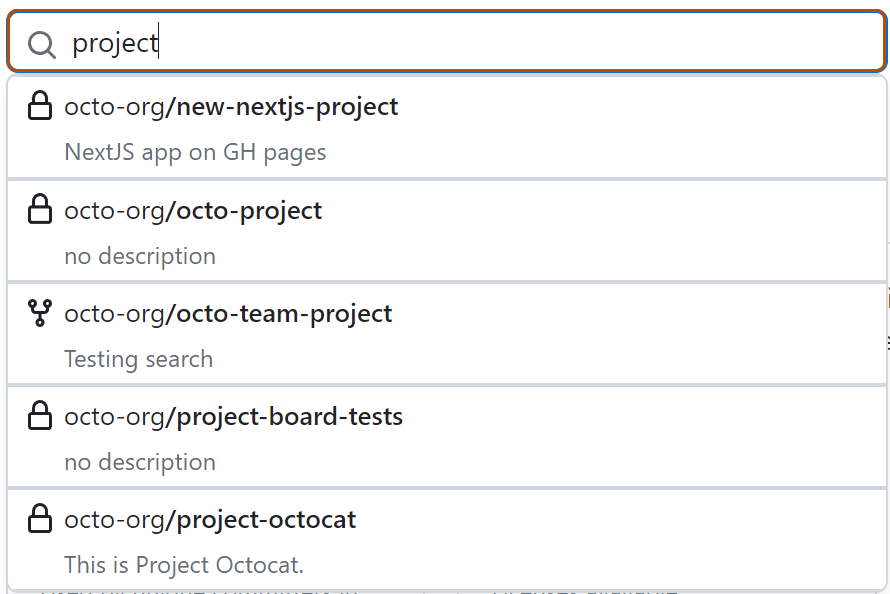
Under "Grant Dependabot private repository access", click Add private repositories to display a repository search field.
-
Start typing the name of the repository you want to grant Dependabot access to.
-
A list of matching repositories in the organization is displayed, click the repository you want to to allow access to and this adds the repository to the allowed list.
-
Optionally, to remove a repository from the list, to the right of the repository, click .