Sobre padrões personalizados para secret scanning
Você pode definir padrões personalizados para identificar segredos que não são detectados pelos padrões padrão compatíbeis com secret scanning. Por exemplo, você pode ter um padrão de segredo que é interno da sua organização. Para obter detalhes dos segredos e provedores de serviços com suporte, confira "Padrões de digitalização de segredo".
É possível definir padrões personalizados para sua empresa, organização ou repositório. Os Secret scanning dão suporte para até 500 padrões personalizados para cada organização ou conta corporativa e até 100 padrões personalizados por repositório.
Também é possível habilitar a proteção de push para padrões personalizados. Para obter mais informações sobre a proteção por push, confira "Proteção por push para repositórios e organizações".
Sobre o uso de expressões regulares para padrões personalizados
É possível especificar padrões personalizados para o secret scanning como uma ou mais expressões regulares.
Os Secret scanning usam a biblioteca Hyperscan e só dão suporte a constructos regex do Hyperscan, que são um subconjunto da sintaxe PCRE. Os modificadores de opções de huperscan não são compatíveis. Para obter mais informações sobre os constructos de padrão do Hyperscan, confira "Suporte a padrões" na documentação do Hyperscan.
As expressões regulares podem ser inseridas manualmente ou geradas usando o gerador de expressões regulares.
Sintaxe de expressão regular para definir manualmente padrões personalizados
A seção Mais opções na interface do usuário ajuda você a escrever expressões regulares manualmente.
- Formato do segredo: uma expressão que descreve o formato do próprio segredo.
- Antes do segredo: uma expressão que descreve os caracteres que vêm antes do segredo. Por padrão, isso é definido como
\A|[^0-9A-Za-z], o que significa que o segredo precisa estar no início de uma linha ou ser precedido por um caractere não alfanumérico. - Após o segredo: uma expressão que descreve os caracteres que vêm após o segredo. Por padrão, isso é definido como
\z|[^0-9A-Za-z], o que significa que o segredo precisa ser seguido por uma nova linha ou por um caractere não alfanumérico. - Requisitos adicionais de correspondência: uma ou mais expressões opcionais às quais o próprio segredo precisa ou não corresponder.
Para tokens simples você normalmente só precisa especificar um formato de segredo. Os outros campos proporcionam flexibilidade para que você possa especificar segredos mais complexos sem criar expressões regulares complexas. Para ver um exemplo de padrão personalizado, confira "Exemplo de um padrão personalizado especificado com requisitos adicionais" abaixo.
Usar o gerador de expressões regulares
O gerador usa um modelo de IA generativa em que você insere uma descrição de texto do tipo de padrão que deseja detectar, incluindo cadeias de caracteres de exemplo opcionais que devem ser detectadas. O modelo retorna até três expressões regulares para revisão. Para obter mais informações, confira "Sobre o gerador de expressões regulares para padrões personalizados e "Gerar expressões regulares para padrões personalizados com IA".
Definindo um padrão personalizado para um repositório
Antes de definir um padrão personalizado, você deve garantir que secret scanning está habilitado no seu repositório. Para obter mais informações, confira "Configurar a verificação de segredo para seus repositórios".
-
No GitHub.com, navegue até a página principal do repositório.
-
Abaixo do nome do repositório, clique em Configurações. Caso não consiga ver a guia "Configurações", selecione o menu suspenso , clique em Configurações.
-
Na seção "Segurança" da barra lateral, clique em Segurança de código e análise.
-
Em "Segurança e análise de código", encontre o "GitHub Advanced Security".
-
Em "Secret scanning", em "Padrões personalizados", clique em Novo padrão.
-
Insira as informações para o novo padrão personalizado. Você deve fornecer, pelo menos, o nome para o seu padrão e uma expressão regular para o formato do seu padrão de segredo.
- No campo "Nome do padrão", digite um nome para o seu padrão.
- No campo "Formato de segredo", digite uma expressão regular para o formato do seu padrão de segredo. Como alternativa, você pode usar o gerador para gerar uma expressão regular para você. Para obter mais informações, confira "Gerar expressões regulares para padrões personalizados com IA".
- Clique em Mais opções para fornecer outro conteúdo complementar ou requisitos de correspondência adicionais para o formato secreto.
- Forneça um exemplo de cadeia de caracteres de teste para verificar se a sua configuração está correspondendo aos padrões esperados.

-
Quando estiver pronto para testar seu novo padrão personalizado, a fim de identificar correspondências no repositório sem criar alertas, clique em Salvar e executar uma simulação.
-
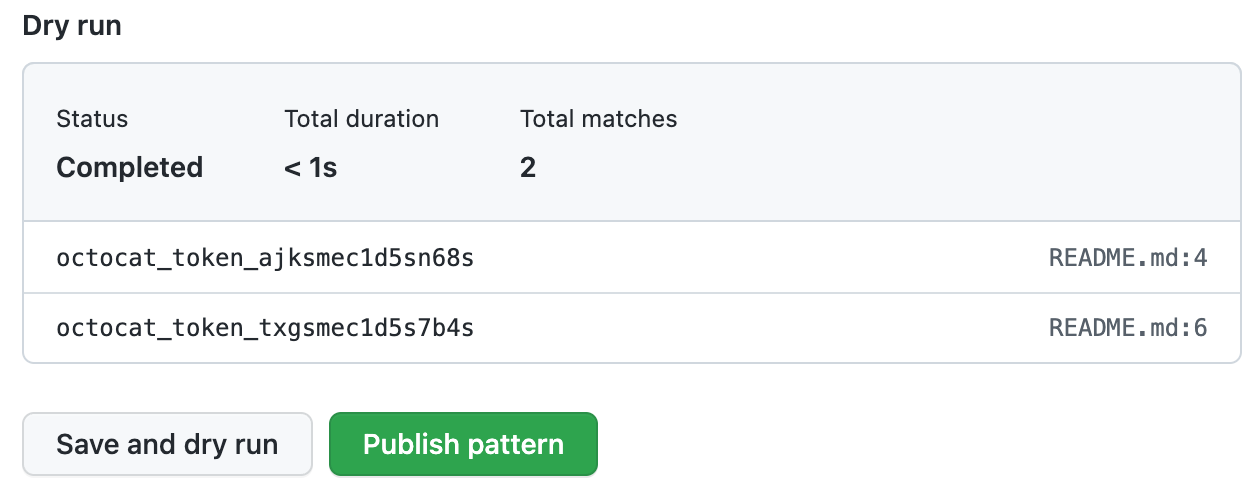
Quando o teste terminar, você verá uma amostra de resultados (até 1.000). Revise os resultados e identifique quaisquer resultados falso-positivos.
-
Edite o novo padrão personalizado para corrigir problemas com os resultados e testar suas alterações e clique em Salvar e executar uma simulação.
-
Quando estiver satisfeito com o novo padrão personalizado, clique em Publicar padrão.
-
Opcionalmente, para habilitar a proteção push para seu padrão personalizado, clique em Habilitar.
Observação: o botão "Habilitar" não estará disponível até que a simulação seja bem-sucedida e você publique o padrão.
Para obter mais informações sobre a proteção por push, confira "Proteção por push para repositórios e organizações".
Depois que o padrão for criado, secret scanning verifica todos segredos em todo o histórico do Git em todos os branches presentes no repositório GitHub. Para saber mais sobre como exibir alertas de verificação de segredo, confira "Gerenciar alertas da verificação de segredo".
Exemplo de um padrão personalizado especificado usando requisitos adicionais
Uma empresa tem um token interno com cinco características. Eles usam os diferentes campos para especificar como identificar tokens da seguinte forma:
| Característica | Campo e expressão regular |
|---|---|
| Comprimento entre 5 e 10 caracteres | Formato do segredo: [$#%@AA-Za-z0-9]{5,10} |
Não termina com um . | Após o segredo: [^\.] |
| Contém números e letras maiúsculas | Requisitos adicionais: o segredo precisa corresponder a [A-Z] e a [0-9] |
| Não inclui mais de uma letra minúscula consecutiva | Requisitos adicionais: o segredo não deve corresponder a [a-z]{2,} |
Contém um destes caracteres: $%@! | Requisitos adicionais: o segredo precisa corresponder a [$%@!] |
Esses tokens iriam corresponder ao padrão personalizado descrito acima:
a9@AAfT! # Secret string match: a9@AAfT
ee95GG@ZA942@aa # Secret string match: @ZA942@a
a9@AA!ee9 # Secret string match: a9@AA
Estas strings não correspondem ao padrão personalizado descrito acima:
a9@AA.!
a@AAAAA
aa9@AA!ee9
aAAAe9
Definindo um padrão personalizado para uma organização
Antes de definir um padrão personalizado, você deverá habilitar secret scanning para os repositórios que você deseja fazer a digitalização na organização. Para habilitar o secret scanning em todos os repositórios da sua organização, confira "Gerenciando as configurações de segurança e de análise da sua organização".
-
No canto superior direito do GitHub.com, selecione sua foto do perfil e em Suas organizações.
-
Ao lado da organização, clique em Configurações.
-
Na seção "Segurança" da barra lateral, clique em Segurança de código e análise.
-
Em "Segurança e análise de código", encontre o "GitHub Advanced Security".
-
Em "Secret scanning", em "Padrões personalizados", clique em Novo padrão.
-
Insira as informações para o novo padrão personalizado. Você deve fornecer, pelo menos, o nome para o seu padrão e uma expressão regular para o formato do seu padrão de segredo.
- No campo "Nome do padrão", digite um nome para o seu padrão.
- No campo "Formato de segredo", digite uma expressão regular para o formato do seu padrão de segredo. Como alternativa, você pode usar o gerador para gerar uma expressão regular para você. Para obter mais informações, confira "Gerar expressões regulares para padrões personalizados com IA".
- Clique em Mais opções para fornecer outro conteúdo complementar ou requisitos de correspondência adicionais para o formato secreto.
- Forneça um exemplo de cadeia de caracteres de teste para verificar se a sua configuração está correspondendo aos padrões esperados.

-
Se estiver pronto para testar seu novo padrão personalizado e quiser identificar correspondências em repositórios específicos sem criar alertas, clique em Salvar e executar uma simulação.
-
Selecione os repositórios em que deseja realizar a simulação.
- Para realizar a simulação em toda a organização, selecione Todos os repositórios da organização.
- Para especificar os repositórios nos quais você deseja realizar a simulação, selecione Repositórios selecionados, pesquise e selecione até dez repositórios.
-
Quando tudo estiver pronto para testar seu novo padrão personalizado, clique em Executar.
-
Quando o teste terminar, você verá uma amostra de resultados (até 1.000). Revise os resultados e identifique quaisquer resultados falso-positivos.

-
Edite o novo padrão personalizado para corrigir problemas com os resultados e testar suas alterações e clique em Salvar e executar uma simulação.
-
Quando estiver satisfeito com o novo padrão personalizado, clique em Publicar padrão.
-
Opcionalmente, a fim de habilitar a proteção de push para o padrão personalizado, clique em Habilitar. Para obter mais informações, confira "Proteção por push para repositórios e organizações".
Observações:
- A opção para ativar a proteção por push é visível apenas para padrões publicados.
- A proteção de push para padrões personalizados será aplicada somente a repositórios em sua organização que tenham o secret scanning como uma proteção de push habilitada. Para obter mais informações, confira "Proteção por push para repositórios e organizações".
- Habilitar a proteção de push para padrões personalizados comumente encontrados pode ser prejudicial para os colaboradores.
Depois que o padrão for criado, secret scanning irá verificar todos os segredos nos repositórios na sua organização, incluindo todo seu histórico do Git em todos os branches. Os proprietários da organização e administradores do repositório receberão um alerta sobre todos os segredos encontrados e poderão revisar o alerta no repositório onde o segredo for encontrado. Para obter mais informações sobre a visualização de alertas de verificação de segredo, confira "Gerenciar alertas da verificação de segredo".
Definir um padrão personalizado para uma conta corporativa
Antes de definir um padrão personalizado, você deverá garantir que você habilite a digitalização de segredo para a sua conta corporativa. Para obter mais informações, confira "Como habilitar o GitHub Advanced Security para sua empresa".
Notes:
- No nível da empresa, somente o criador de um padrão personalizado pode editar o padrão e usá-lo em uma simulação.
- Você só pode executar uma simulação em repositórios aos quais você tem acesso de administração. Se um proprietário da empresa quiser acesso para executar simulações em qualquer repositório em uma organização, ele deverá receber a função de proprietário da organização. Para obter mais informações, confira "Gerenciando sua função em uma organização pertencente à sua empresa".
-
No canto superior direito do GitHub.com, clique na foto do seu perfil e em Suas empresas.
-
Na lista de empresas, clique na empresa que você deseja visualizar.
-
Na barra lateral da empresa, clique em Políticas. 1. Em "Políticas", clique em Segurança e análise de código.
-
Em "Segurança e análise de código", clique em Recursos de segurança.
-
Em "Padrões personalizados de verificação de segredo", clique em Novo padrão.
-
Insira as informações para o novo padrão personalizado. Você deve fornecer, pelo menos, o nome para o seu padrão e uma expressão regular para o formato do seu padrão de segredo.
- No campo "Nome do padrão", digite um nome para o seu padrão.
- No campo "Formato de segredo", digite uma expressão regular para o formato do seu padrão de segredo. Como alternativa, você pode usar o gerador para gerar uma expressão regular para você. Para obter mais informações, confira "Gerar expressões regulares para padrões personalizados com IA".
- Clique em Mais opções para fornecer outro conteúdo complementar ou requisitos de correspondência adicionais para o formato secreto.
- Forneça um exemplo de cadeia de caracteres de teste para verificar se a sua configuração está correspondendo aos padrões esperados.

-
Quando estiver pronto para testar o novo padrão personalizado, clique em Salvar e executar uma simulação para identificar correspondências na empresa sem criar alertas.
-
Pesquise e selecione até 10 repositórios em que você deseja executar a simulação.
-
Quando tudo estiver pronto para testar seu novo padrão personalizado, clique em Executar.
-
Quando o teste terminar, você verá uma amostra de resultados (até 1.000). Revise os resultados e identifique quaisquer resultados falso-positivos.

-
Edite o novo padrão personalizado para corrigir problemas com os resultados e testar suas alterações e clique em Salvar e executar uma simulação.
-
Quando estiver satisfeito com o novo padrão personalizado, clique em Publicar padrão.
-
Opcionalmente, a fim de habilitar a proteção de push para o padrão personalizado, clique em Habilitar. Para obter mais informações, confira "Proteção por push para repositórios e organizações".
Observações:
- Para habilitar a proteção de push para padrões personalizados, é preciso habilitar o secret scanning como a proteção de push no nível corporativo. Para obter mais informações, confira "Proteção por push para repositórios e organizações".
- Habilitar a proteção de push para padrões personalizados comumente encontrados pode ser prejudicial para os colaboradores.
Depois que o seu padrão for criado, secret scanning irá digitalizar qualquer segredo em repositórios nas organizações da sua empresa com GitHub Advanced Security habilitado, incluindo todo seu histórico do Git em todos os branches. Os proprietários da organização e administradores do repositório receberão um alerta sobre todos os segredos encontrados e poderão revisar o alerta no repositório onde o segredo for encontrado. Para obter mais informações sobre a visualização de alertas de verificação de segredo, confira "Gerenciar alertas da verificação de segredo".
Editando um padrão personalizado
Ao salvar uma alteração em um padrão personalizado, isso fecha todos os alertas de verificação de segredo criados usando a versão anterior do padrão.
-
Acesse o local onde o padrão personalizado foi criado. Um padrão personalizado pode ser criado na conta de um repositório, organização ou empresa.
- Para um repositório ou organização, veja as configurações de "Segurança e análise" do repositório ou da organização em que o padrão personalizado foi criado. Para obter mais informações, confira "Como definir um padrão personalizado para um repositório" ou "Como definir um padrão personalizado para uma organização".
- Para uma empresa, em "Políticas", veja a área "Advanced Security" e clique em Recursos de segurança. Para obter mais informações, confira "Como definir um padrão personalizado para uma conta corporativa" acima.
-
Em "Secret scanning", à direita do padrão personalizado que você deseja editar, clique em .
-
Quando estiver pronto para testar o padrão personalizado editado, clique em Salvar e executar uma simulação para identificar correspondências sem criar alertas.
-
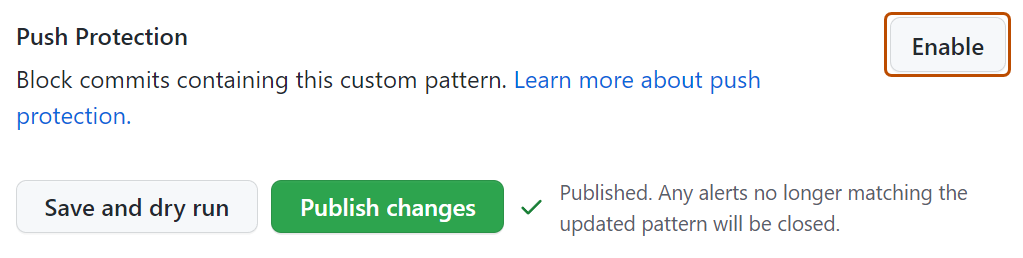
Depois de revisar e testar suas alterações, clique em Publicar alterações.
-
Opcionalmente, para habilitar a proteção push para seu padrão personalizado, clique em Habilitar.
Observação:
- A proteção de push para padrões personalizados será aplicada somente a repositórios que tenham o secret scanning como uma proteção de push habilitada. Para obter mais informações sobre a proteção por push, confira "Proteção por push para repositórios e organizações".
- Habilitar a proteção de push para padrões personalizados comumente encontrados pode ser prejudicial para os colaboradores.
-
Opcionalmente, para desabilitar a proteção de push para o padrão personalizado, clique em Desabilitar.
Removendo um padrão personalizado
- Acesse o local onde o padrão personalizado foi criado. Um padrão personalizado pode ser criado na conta de um repositório, organização ou empresa.
- Para um repositório ou organização, veja as configurações de "Segurança e análise" do repositório ou da organização em que o padrão personalizado foi criado. Para obter mais informações, confira "Como definir um padrão personalizado para um repositório" ou "Como definir um padrão personalizado para uma organização".
- Para uma empresa, em "Políticas", veja a área "Advanced Security" e clique em Recursos de segurança. Para obter mais informações, confira "Como definir um padrão personalizado para uma conta corporativa" acima.
- À direita do padrão personalizado que você deseja remover, clique em .
- Revise a confirmação e selecione um método para lidar com todos os alertas abertos relacionados ao padrão personalizado.
- Clique em Sim, excluir este padrão.
Métricas para padrões personalizados
Os proprietários da organização e as pessoas com permissões de administrador podem ver uma visão geral da atividade para padrões personalizados. A visão geral inclui atividades de alerta e proteção por push para o padrão personalizado durante os últimos 30 dias.
Nota: as métricas para padrões personalizados estão em versão beta pública e sujeitas a alterações.
Exibição de métricas para padrões personalizados
- Acesse o local onde o padrão personalizado foi criado. Um padrão personalizado pode ser criado na conta de um repositório, organização ou empresa.
- Para um repositório ou organização, veja as configurações de "Segurança e análise" do repositório ou da organização em que o padrão personalizado foi criado. Para obter mais informações, confira "Como definir um padrão personalizado para um repositório" ou "Como definir um padrão personalizado para uma organização".
- Para uma empresa, em "Políticas", veja a área "Advanced Security" e clique em Recursos de segurança. Para obter mais informações, confira "Como definir um padrão personalizado para uma conta corporativa" acima.
- Em "Secret scanning" clique no padrão personalizado que você deseja exibir.
As métricas são exibidas sob o nome do padrão personalizado.