About code scanning results on pull requests
In repositories where code scanning is configured as a pull request check, code scanning checks the code in the pull request. By default, this is limited to pull requests that target the default branch, but you can change this configuration within GitHub Actions or in a third-party CI/CD system.
If the lines of code changed in the pull request generate code scanning alerts, the alerts are reported in the following places on the pull request.
- Check results in the pull request
- The Conversation tab of the pull request, as part of a pull request review
- The Files changed tab of the pull request
Note: Code scanning displays alerts in pull requests only when all the lines of code identified by the alert exist in the pull request diff. For more information, see "SARIF support for code scanning."
If you have write permission for the repository, you can see any existing code scanning alerts on the Security tab. For information about repository alerts, see "Managing code scanning alerts for your repository."
In repositories where code scanning is configured to scan each time code is pushed, code scanning will also map the results to any open pull requests and add the alerts as annotations in the same places as other pull request checks. For more information, see "Customizing your advanced setup for code scanning."
If your pull request targets a protected branch that uses code scanning, and the repository owner has configured required status checks, then the "Code scanning results" check must pass before you can merge the pull request. For more information, see "About protected branches."
About code scanning as a pull request check
There are many options for configuring code scanning as a pull request check, so the exact configuration of each repository will vary and some will have more than one check.
Code scanning results check
For all configurations of code scanning, the check that contains the results of code scanning is: Code scanning results. The results for each analysis tool used are shown separately. Any new alerts on lines of code changed in the pull request are shown as annotations.
To see the full set of alerts for the analyzed branch, click View all branch alerts. This opens the full alert view where you can filter all the alerts on the branch by type, severity, tag, etc. For more information, see "Managing code scanning alerts for your repository."

Code scanning results check failures
If the code scanning results check finds any problems with a severity of error, critical, or high, the check fails and the error is reported in the check results. If all the results found by code scanning have lower severities, the alerts are treated as warnings or notes and the check succeeds.

You can override the default behavior in your repository settings, by specifying the level of severities and security severities that will cause a pull request check failure. For more information, see "Customizing your advanced setup for code scanning".
Other code scanning checks
Depending on your configuration, you may see additional checks running on pull requests with code scanning configured. These are usually workflows that analyze the code or that upload code scanning results. These checks are useful for troubleshooting when there are problems with the analysis.
For example, if the repository uses the CodeQL analysis workflow a CodeQL / Analyze (LANGUAGE) check is run for each language before the results check runs. The analysis check may fail if there are configuration problems, or if the pull request breaks the build for a language that the analysis compiles (for example, C/C++, C#, Go, Java, and Swift).
As with other pull request checks, you can see full details of the check failure on the Checks tab. For more information about configuring and troubleshooting, see "Customizing your advanced setup for code scanning" or "Troubleshooting code scanning."
Viewing an alert on your pull request
You can see any code scanning alerts that are inside the diff of the changes introduced in a pull request by viewing the Conversation tab. Code scanning posts a pull request review that shows each alert as an annotation on the lines of code that triggered the alert. You can comment on the alerts, dismiss the alerts, and view paths for the alerts, directly from the annotations. You can view the full details of an alert by clicking the "Show more details" link, which will take you to the alert details page.

You can also view all code scanning alerts that are inside the diff of the changes introduced in the pull request in the Files changed tab.
If you add a new code scanning configuration in your pull request, you will see a comment on your pull request directing you to the Security tab of the repository so you can view all the alerts on the pull request branch. For more information about viewing the alerts for a repository, see "Managing code scanning alerts for your repository."
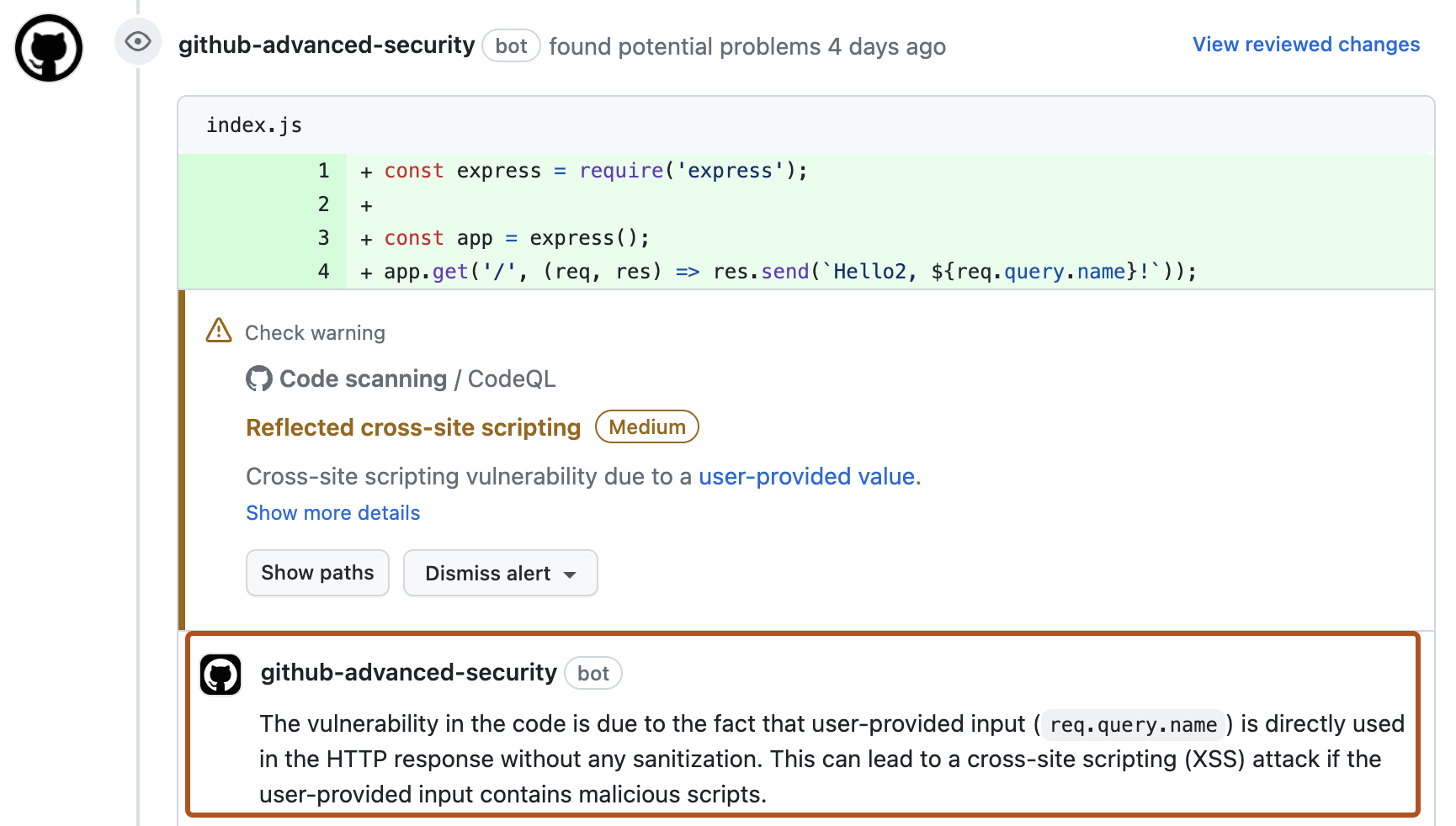
If you have write permission for the repository, some annotations contain links with extra context for the alert. In the example above, from CodeQL analysis, you can click user-provided value to see where the untrusted data enters the data flow (this is referred to as the source). In this case you can also view the full path from the source to the code that uses the data (the sink) by clicking Show paths. This makes it easy to check whether the data is untrusted or if the analysis failed to recognize a data sanitization step between the source and the sink. For information about analyzing data flow using CodeQL, see "About data flow analysis."
To see more information about an alert, users with write permission can click the Show more details link shown in the annotation. This allows you to see all of the context and metadata provided by the tool in an alert view. In the example below, you can see tags showing the severity, type, and relevant common weakness enumerations (CWEs) for the problem. The view also shows which commit introduced the problem.
The status and details on the alert page only reflect the state of the alert on the default branch of the repository, even if the alert exists in other branches. You can see the status of the alert on non-default branches in the Affected branches section on the right-hand side of the alert page. If an alert doesn't exist in the default branch, the status of the alert will display as "in pull request" or "in branch" and will be colored grey.
In the detailed view for an alert, some code scanning tools, like CodeQL analysis, also include a description of the problem and a Show more link for guidance on how to fix your code.

Commenting on an alert in a pull request
You can comment on any code scanning alert that appears in a pull request. Alerts appear as annotations in the Conversation tab of a pull request, as part of a pull request review, and also are shown in the Files changed tab.
You can choose to require all conversations in a pull request, including those on code scanning alerts, to be resolved before a pull request can be merged. For more information, see "About protected branches."
Fixing an alert on your pull request
Anyone with push access to a pull request can fix a code scanning alert that's identified on that pull request. If you commit changes to the pull request this triggers a new run of the pull request checks. If your changes fix the problem, the alert is closed and the annotation removed.
Working with autofix suggestions for alerts
Note: GitHub autofix for code scanning is in beta. Functionality and documentation are subject to change. During this phase, the feature is restricted to JavaScript, TypeScript, Python, and Java alerts identified by CodeQL. If you have an enterprise account and use GitHub Advanced Security, your enterprise has access to the beta.
Autofix, powered by GitHub Copilot, is an expansion of code scanning that provides you with targeted recommendations to help you fix code scanning alerts in pull requests. The potential fixes are generated automatically by large language models (LLMs) using data from the codebase, the pull request, and from CodeQL analysis.
Generating autofix suggestions and publishing to a pull request
When autofix is enabled for a repository, alerts are displayed in pull requests as normal and information from any alerts found by CodeQL is automatically sent to the LLM for processing. When LLM analysis is complete, any results are published as comments on relevant alerts. For more information, see "About autofix for CodeQL code scanning."
Notes:
- Autofix supports a subset of CodeQL queries. For information about the availability of autofix, see the query tables linked from "CodeQL query suites."
- When analysis is complete, all relevant results are published to the pull request at once. If at least one alert in your pull request has an autofix suggestion, you should assume that the LLM has finished identifying potential fixes for your code.
Usually, when you suggest changes to a pull request, your comment contains changes for a single file that is changed in the pull request. The following screenshot shows an autofix comment that suggests changes to the index.js file where the alert is displayed. Since the potential fix requires a new dependency on escape-html, the comment also suggests adding this dependency to the package.json file, even though the original pull request makes no changes to this file.
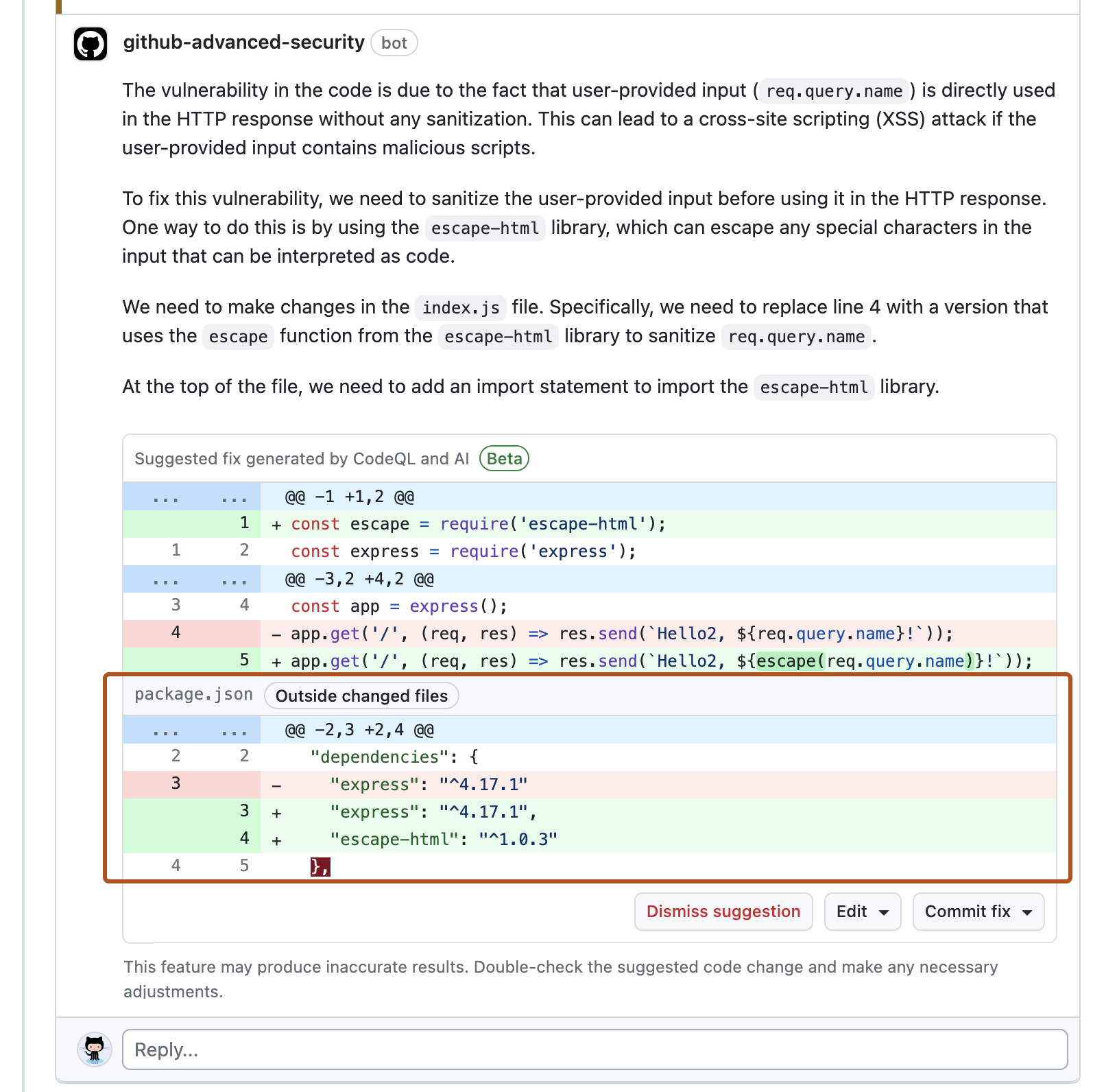
Assessing and committing an autofix suggestion
Each autofix suggestion demonstrates a potential solution for a code scanning alert in your codebase. You must assess the suggested changes to determine whether they are a good solution for your codebase and to ensure that they maintain the intended behavior. For information about the limitations of autofix suggestions, see "Limitations of autofix suggestions" and "Mitigating the limitations of autofix suggestions" in "About autofix for CodeQL code scanning."
- Click Edit to display the editing options and select your preferred method.
- Select Edit with codespaces to open a codespace showing your branch with the suggested fix applied.
- Select Edit locally with GitHub CLI to display instructions for applying the suggested fix to any local repository or branch.
- Test and modify the suggested fix as needed.
- When you have finished testing your changes, commit the changes, and push them to your branch.
- Pushing the changes to your branch will trigger all the usual tests for your pull request. Confirm that your unit tests still pass and that the code scanning alert is now fixed.
Dismissing an autofix suggestion
If you decide to reject an autofix suggestion, click Dismiss suggestion in the comment to dismiss the suggested fix.
Dismissing an alert on your pull request
An alternative way of closing an alert is to dismiss it. You can dismiss an alert if you don't think it needs to be fixed. For example, an error in code that's used only for testing, or when the effort of fixing the error is greater than the potential benefit of improving the code. If you have write permission for the repository, a Dismiss alert button is available in code annotations and in the alerts summary. When you click Dismiss alert you will be prompted to choose a reason for closing the alert.
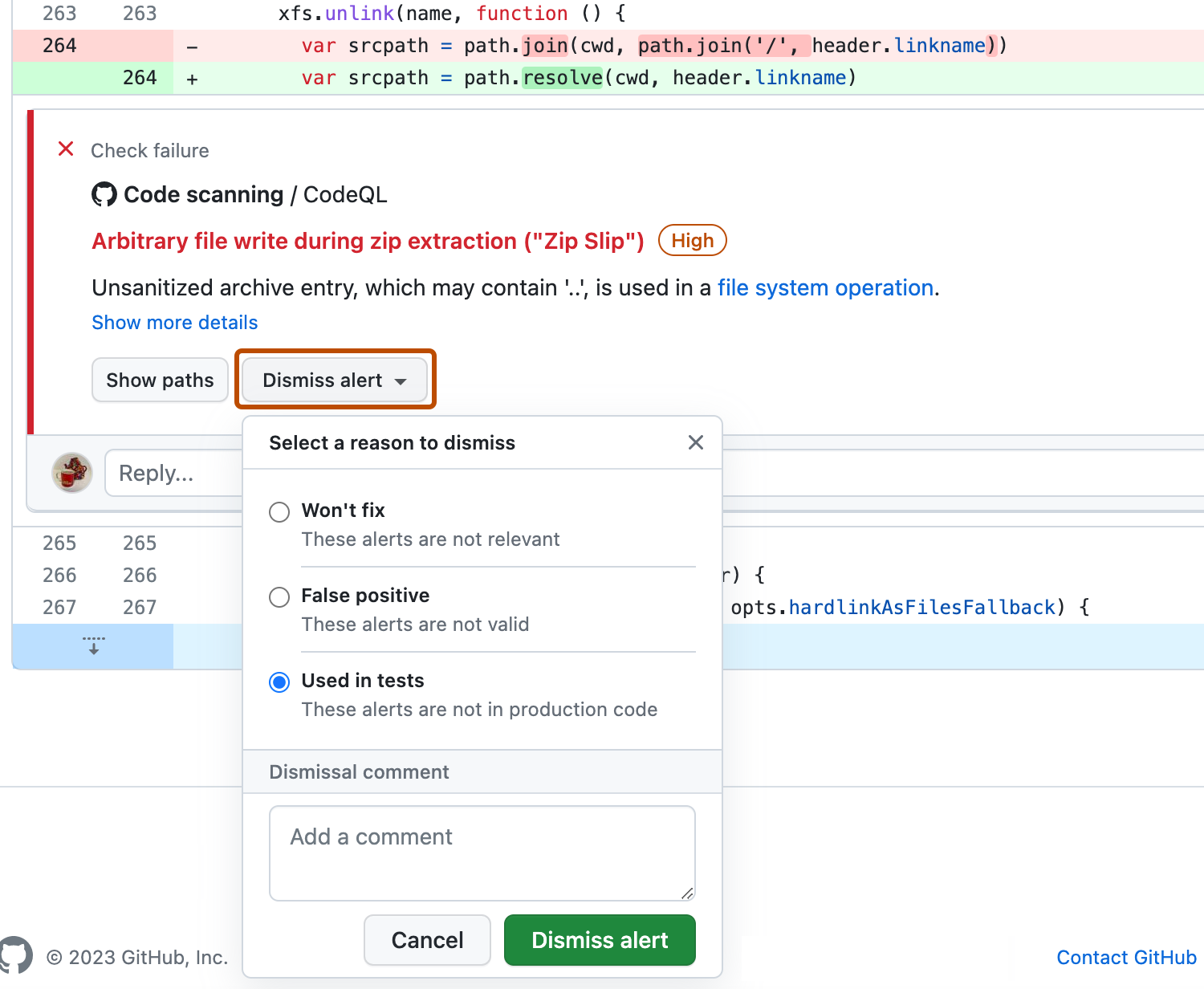
It's important to choose the appropriate reason from the drop-down menu as this may affect whether a query continues to be included in future analysis. Optionally, you can comment on a dismissal to record the context of an alert dismissal. The dismissal comment is added to the alert timeline and can be used as justification during auditing and reporting. You can retrieve or set a comment by using the code scanning REST API. The comment is contained in dismissed_comment for the alerts/{alert_number} endpoint. For more information, see "REST API endpoints for code scanning."
If you dismiss a CodeQL alert as a false positive result, for example because the code uses a sanitization library that isn't supported, consider contributing to the CodeQL repository and improving the analysis. For more information about CodeQL, see "Contributing to CodeQL."
For more information about dismissing alerts, see "Managing code scanning alerts for your repository."