CAS is a single sign-on (SSO) protocol for multiple web applications. A CAS user account does not take up a license seat until the user signs in to your Enterprise instance.
Username considerations with CAS
GitHub Enterprise usernames can only contain alphanumeric characters and dashes (-). GitHub Enterprise will normalize any non-alphanumeric character in your account's username into a dash. For example, a username of gregory.st.john will be normalized to gregory-st-john. Note that normalized usernames also can't start or end with a dash. They also can't contain two consecutive dashes.
Usernames created from email addresses are created from the normalized characters that precede the @ character.
If multiple accounts are normalized into the same GitHub Enterprise username, only the first user account is created. Subsequent users with the same username won't be able to sign in.
This table gives examples of how usernames are normalized in GitHub Enterprise:
| Username | Normalized username | Result |
|---|---|---|
| Ms.Bubbles | ms-bubbles |
This username is created successfully. |
| !Ms.Bubbles | -ms-bubbles |
This username is not created, because it starts with a dash. |
| Ms.Bubbles! | ms-bubbles- |
This username is not created, because it ends with a dash. |
| Ms!!Bubbles | ms--bubbles |
This username is not created, because it contains two consecutive dashes. |
| Ms!Bubbles | ms-bubbles |
This username is not created. Although the normalized username is valid, it already exists. |
| Ms.Bubbles@example.com | ms-bubbles |
This username is not created. Although the normalized username is valid, it already exists. |
Two-factor authentication
When using SAML or CAS, two-factor authentication is not supported on the GitHub Enterprise appliance. Two-factor authentication may be supported by the external authentication provider.
CAS attributes
The following attributes are available.
| Attribute name | Type | Description |
|---|---|---|
username |
Required | The GitHub Enterprise username. |
Configuring CAS
Warning: Before configuring CAS on your GitHub Enterprise instance, note that users will not be able to use their CAS usernames and passwords to authenticate API requests or Git operations over HTTP/HTTPS. Instead, they will need to create an access token.
In the left sidebar, click Authentication.
Select CAS.
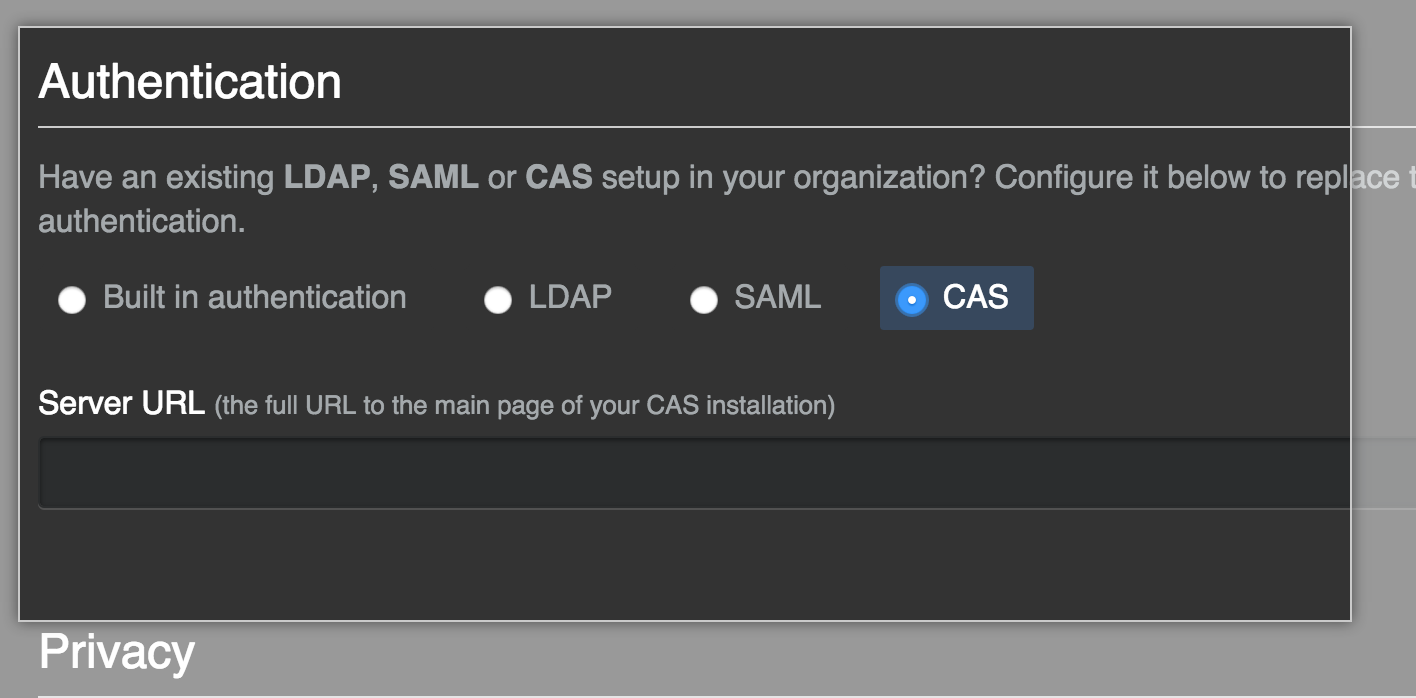
- In the Server URL field, type the full URL of your CAS server. If your CAS server uses a certificate that can't be validated by GitHub Enterprise, you can use the
ghe-ssl-ca-certificate-installcommand to install it as a trusted certificate.
