As a site administrator, you can search an extensive list of audited actions on your GitHub Enterprise instance.
Instructions
In the upper-left corner of any page, click .

In the upper-right corner of any page, click .
In the left sidebar, click Audit log.
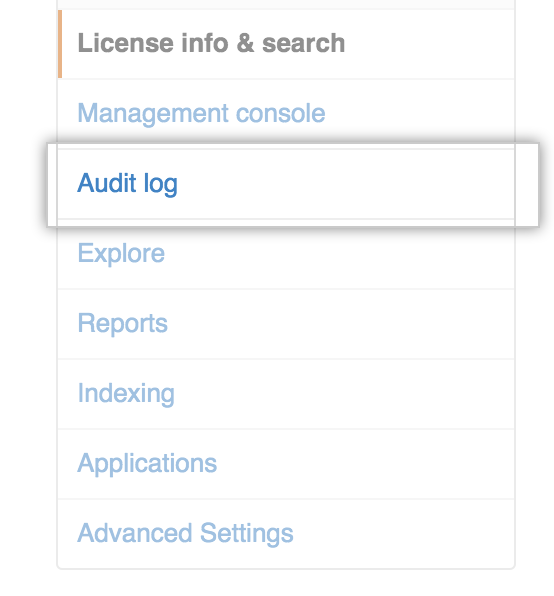
Type a search query.
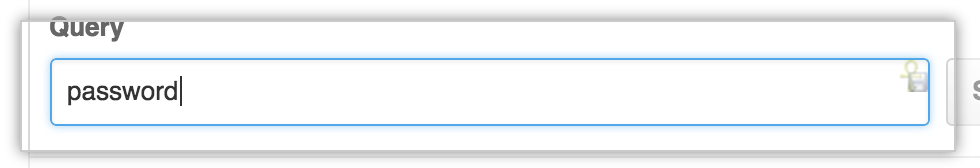
-
Click Search.
Search query syntax
Compose a search query from one or more key:value pairs separated by AND/OR logical operators.
| Key | Value |
|---|---|
actor_id |
ID of the user account that initiated the action |
actor |
Name of the user account that initiated the action |
oauth_app_id |
ID of the OAuth application associated with the action |
action |
Name of the audited action |
user_id |
ID of the user affected by the action |
user |
Name of the user affected by the action |
repo_id |
ID of the repository affected by the action (if applicable) |
repo |
Name of the repository affected by the action (if applicable) |
actor_ip |
IP address from which the action was initiated |
created_at |
Time at which the action occurred |
from |
View from which the action was initiated |
note |
Miscellaneous event-specific information (in either plain text or JSON format) |
org |
Name of the organization affected by the action (if applicable) |
org_id |
ID of the organization affected by the action (if applicable) |
For example, to see all actions that have affected the repository octocat/Spoon-Knife since the beginning of 2014, you would type the following query:
repo:"octocat/Spoon-Knife" AND created_at:[2014-01-01 TO *]
To see all actions that have affected or been initiated by the user account hubot, you would type:
user:hubot OR actor:hubot
To see all SSH keys that have been added, updated, or removed, you would type:
action:public_key.create OR action:public_key.update OR action:public_key.delete
For a full list of actions, see "Audited actions."
