About Transport Layer Security
TLS, which replaced SSL, is enabled and configured with a self-signed certificate when GitHub Enterprise Server is started for the first time. As self-signed certificates are not trusted by web browsers and Git clients, these clients will report certificate warnings until you disable TLS or upload a certificate signed by a trusted authority, such as Let's Encrypt.
The GitHub Enterprise Server appliance will send HTTP Strict Transport Security headers when SSL is enabled. Disabling TLS will cause users to lose access to the appliance, because their browsers will not allow a protocol downgrade to HTTP. For more information, see "HTTP Strict Transport Security (HSTS)" on Wikipedia.
警告:在负载均衡器上终止 HTTPS 连接时,从负载均衡器到 GitHub Enterprise Server 的请求也需要使用 HTTPS。 不支持降级到 HTTP 连接。
To allow users to use FIDO U2F for two-factor authentication, you must enable TLS for your instance. For more information, see "Configuring two-factor authentication."
Prerequisites
To use TLS in production, you must have a certificate in an unencrypted PEM format signed by a trusted certificate authority.
Your certificate will also need Subject Alternative Names configured for the subdomains listed in "Enabling subdomain isolation" and will need to include the full certificate chain if it has been signed by an intermediate certificate authority. For more information, see "Subject Alternative Name" on Wikipedia.
You can generate a certificate signing request (CSR) for your instance using the ghe-ssl-generate-csr command. For more information, see "Command-line utilities."
Your key must be an RSA key and must not have a passphrase. For more information, see "Removing the passphrase from your key file".
Uploading a custom TLS certificate
Warning: Configuring TLS causes a small amount of downtime for your GitHub Enterprise Server instance.
-
从 GitHub Enterprise Server 上的管理帐户任意页面的右上角,单击 。
-
如果� 尚未在“站点管理员”页上,请在左上角单击“站点管理员”。
-
在左侧边� �中,单击“管理控制台”。
-
在左侧边� �中,单击“隐私”。
-
选择“仅限 TLS”(推荐)。
-
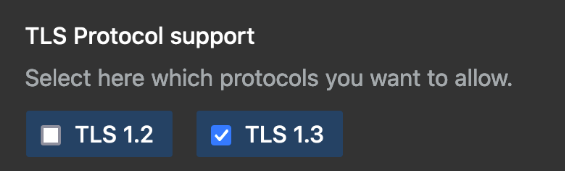
Under "TLS Protocol support", select the protocols you want to allow.
-
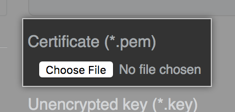
Under "Certificate", click Choose File to choose a TLS certificate or certificate chain (in PEM format) to install. This file will usually have a .pem, .crt, or .cer extension.
-
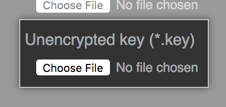
Under "Unencrypted key", click Choose File to choose an RSA key (in PEM format) to install. This file will usually have a .key extension.
-
在左侧边� �下,单击“保存设置”。
注意:保存 管理控制台 中的设置会重启系统服务,这可能会导致用户可察觉的停机时间。
-
等待配置运行完毕。
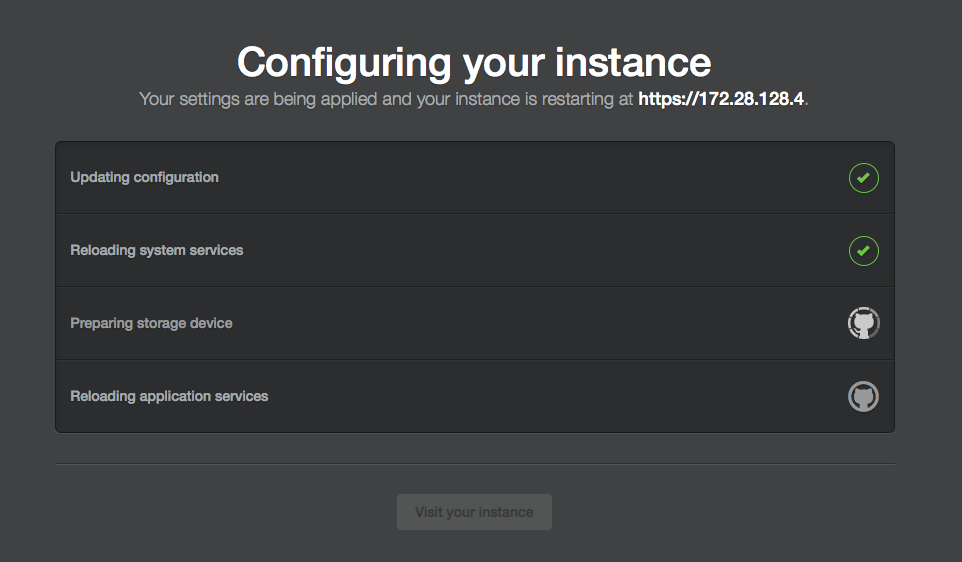
About Let's Encrypt support
Let's Encrypt is a public certificate authority that issues free, automated TLS certificates that are trusted by browsers using the ACME protocol. You can automatically obtain and renew Let's Encrypt certificates on your appliance without any required manual maintenance.
要使用“让我们� 密”自动化,您的设备必须配置可通过 HTTP 公开访问的主机名。 该设备还必须可以进行出站 HTTPS 连接。
When you enable automation of TLS certificate management using Let's Encrypt, your GitHub Enterprise Server instance will contact the Let's Encrypt servers to obtain a certificate. To renew a certificate, Let's Encrypt servers must validate control of the configured domain name with inbound HTTP requests.
You can also use the ghe-ssl-acme command line utility on your GitHub Enterprise Server instance to automatically generate a Let's Encrypt certificate. For more information, see "Command-line utilities."
Configuring TLS using Let's Encrypt
要使用“让我们� 密”自动化,您的设备必须配置可通过 HTTP 公开访问的主机名。 该设备还必须可以进行出站 HTTPS 连接。
Warning: Configuring TLS causes a small amount of downtime for your GitHub Enterprise Server instance.
-
从 GitHub Enterprise Server 上的管理帐户任意页面的右上角,单击 。

-
如果� 尚未在“站点管理员”页上,请在左上角单击“站点管理员”。

-
在左侧边� �中,单击“管理控制台”。

-
在左侧边� �中,单击“隐私”。

-
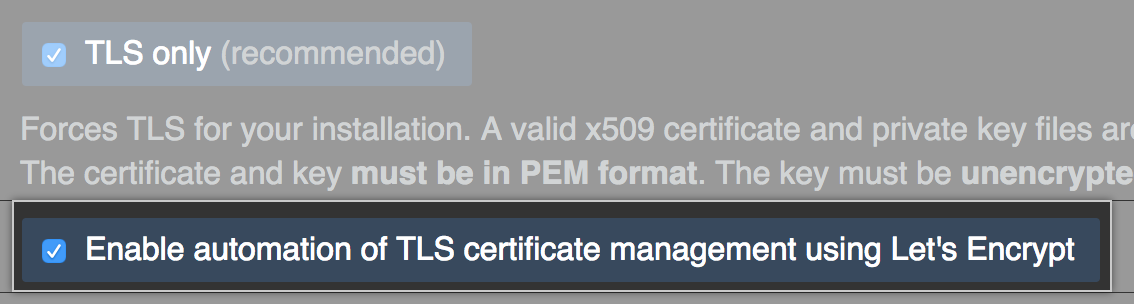
选择“仅限 TLS”(推荐)。

-
Select Enable automation of TLS certificate management using Let's Encrypt.
-
在左侧边� �下,单击“保存设置”。

注意:保存 管理控制台 中的设置会重启系统服务,这可能会导致用户可察觉的停机时间。
-
等待配置运行完毕。

-
在左侧边� �中,单击“隐私”。

-
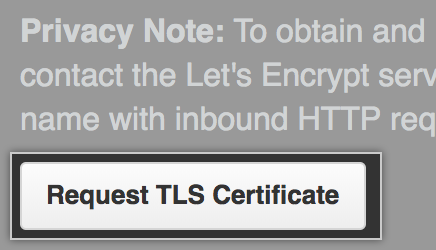
Click Request TLS certificate.
-
Wait for the "Status" to change from "STARTED" to "DONE".
-
Click Save configuration.