关于机密
开发环境机密是你在 GitHub Codespaces 设置中为组织、存储库或个人帐户创建的加密环境变量。 本文介绍如何管理组织机密和存储库机密。 有关创建用户特定机密的信息,请参阅“管理 GitHub Codespaces 特定于帐户的机密”。
你创建的开发环境机密可用于 GitHub Codespaces。 在机密到达 GitHub 之前,GitHub使用 libsodium 密封盒对机密进行加密,并且仅当你在 codespace 中使用它们时才进行解密。
组织机密允许在多个存储库之间共享机密,从而减少创建重复机密的需要。 您可以使用访问策略来控制哪些仓库可以使用组织密钥。
一旦创建了密码,便可以在创建新的代码空间或重新启动代码空间时使用它。 如果已在 GitHub.com 上创建了机密,并且想要在当前正在运行的 codespace 中使用它,请停止 codespace,然后重启它。 有关停止 codespace 的信息,请参阅“在 GitHub Codespaces 中使用 Visual Studio Code 命令面板”。
命名密钥
以下规则适用于密码名称:
-
密钥名称只能包含字母数字字符(
[a-z]、[A-Z]、[0-9])或下划线 (_)。 不允许空格。 -
机密名称不得以
GITHUB_前缀开头。 -
密码名称不能以数字开头。
-
机密名称不区分大小写。
-
密码名称在所创建的级别上必须是唯一的。 例如,在仓库级别创建的密钥必须在该仓库中具有唯一的名称, 而在组织级创建的密钥必须在该级别有独特的名称。
如果具有相同名称的机密存在于多个级别,则级别最低的机密优先。 例如,如果组织级别密码的名称与仓库级别的密码相同,则仓库级别的密码优先。
密码的限制
每个组织最多可存储 100 个密钥,每个仓库最多可存储 100 个密钥。
密码大小限于 48 KB。
用于存储库的建议的机密
项目可能需要特定的用户机密。 例如,要在 codespace 中运行应用程序,用户可能需要提供个人 API 密钥。 如果是这种情况,可在开发容器配置中指定建议的机密。 然后当用户使用高级选项页创建 codespace 时,系统会提示用户提供这些机密的值(如果他们尚未创建这些个人机密)。 如果用户提供用于 codespace 的机密值,则此机密将添加到 Codespaces 个人设置中。 用户在将来为此存储库创建 codespace 时,他们不必为此机密输入值。 有关详细信息,请参阅“为存储库指定建议的机密”。
为仓库添加密钥
要为组织存储库创建开发环境机密,您必须具有管理员访问权限。
-
在 GitHub.com 上,导航到存储库的主页。
-
在存储库名称下,单击 “设置”。 如果看不到“设置”选项卡,请选择“”下拉菜单,然后单击“设置”********。
-
在边栏的“安全性”部分中,选择 机密和变量,然后单击 Codespaces。
-
在页面顶部,单击“新建存储库机密”。
-
在“名称”输入框中键入机密名称。
-
输入密码的值。
-
单击“添加机密”。
为组织添加密钥
在组织中创建开发环境机密时,可以使用策略来限制可以访问该机密的存储库。 例如,您可以将访问权限授予所有仓库,也可以限制仅私有仓库或指定的仓库列表拥有访问权限。
要在组织级别创建机密,必须具有 admin 访问权限。
-
在 GitHub.com 上,导航到组织的主页。
-
在组织名称下,单击 “设置”****。 如果看不到“设置”选项卡,请选择“”下拉菜单,然后单击“设置”********。
-
在边栏的“安全性”部分中,选择 机密和变量,然后单击 Codespaces。
-
在页面顶部,单击“新建机密”。
-
在“名称”输入框中键入机密名称。
-
输入“机密”的值。
-
从“存储库访问”下拉列表中,选择访问策略。
-
单击“添加机密”。
审查对组织级别密码的访问权限
您可以检查哪些访问策略应用于组织中的开发环境机密。
-
在 GitHub.com 上,导航到组织的主页。
-
在组织名称下,单击 “设置”****。 如果看不到“设置”选项卡,请选择“”下拉菜单,然后单击“设置”********。

-
在边栏的“安全性”部分中,选择 机密和变量,然后单击 Codespaces。
-
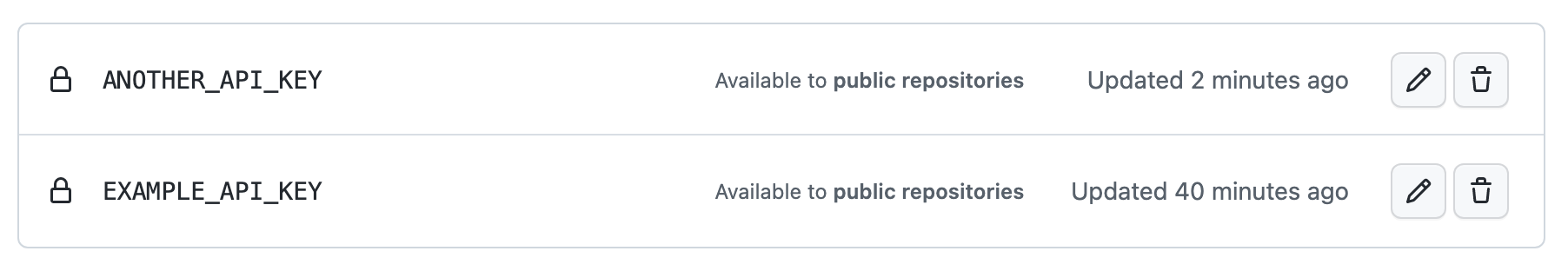
密码列表包括任何已配置的权限和策略。 例如:
-
若要详细了解已为每个机密配置的权限,请单击“更新”。