Nota: El Escaneo de código se encuentra en beta dentro de GitHub Enterprise Server 2.22. Para encontrar un lanzamiento de disponibilidad general del escaneo de código, mejora al último lanzamiento de GitHub Enterprise Server.
Acerca de los resultados del escaneo de código en las solicitudes de cambios
En los repositorios donde se configura el escaneo de código como una verificación de solicitudes de cambios, éste verificará el código en dicha solicitud. Predeterminadamente, esto se limita a solicitudes de cambios que apuntan a la rama predeterminada, pero puedes cambiar esta configuración dentro de GitHub Actions o en un sistema de IC/EC de terceros. Si el fusionar los cambios puede introducir alertas nuevas de escaneo de código a la rama destino, éstas se reportarán como resultados de verificación en la solicitud de cambios. Las alertas también se muestran como anotaciones en la pestaña de Archivos que cambiaron de la solicitud de cambios. Si tienes permisos de escritura para el repositorio, puedes ver cualquier alerta del escaneo de código existente en la pestaña de Seguridad. Para obtener más información sobre las alertas de los repositorios, consulta la sección "Administrar las alertas del escaneo de código para tu repositorio".
Si el escaneo de código presenta cualquier resultado con una severidad de error, la verificación fallará y el error se reportará en los resultados de la verificación. Si todos los resultados que encuentra el escaneo de código tienen severidades menores, las alertas se tratarán como advertencias o notificaciones y la verificación será exitosa. Si tu solicitud de cambios apunta a una rama protegida que utiliza el escaneo de código y el propietario del repositorio configuró las verificaciones de estado requeridas, entonces debes ya sea arreglar o cerrar todas las alertas de error antes de que se pueda fusionar la solicitud de cambios. Para obtener más información, consulta"Acerca de las ramas protegidas".
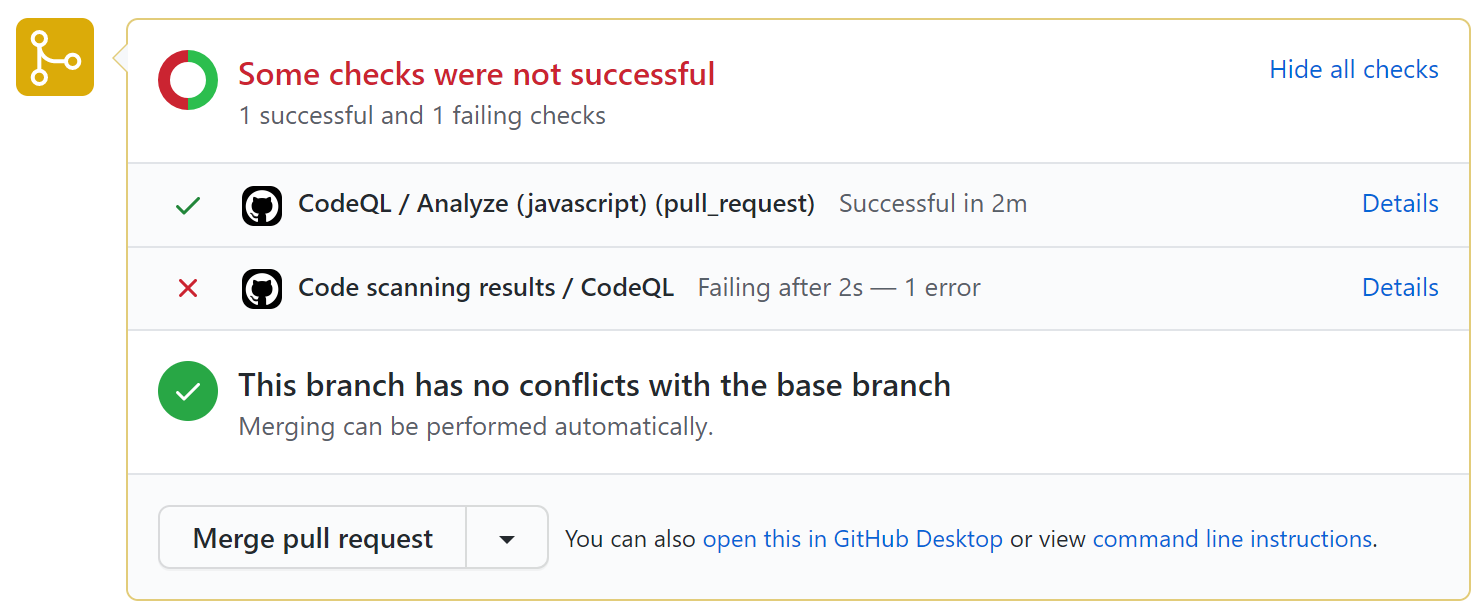
Acerca del escaneo de código como una verificación de solicitudes de cambio
Hay muchas opciones para configurar el escaneo de código como una verificación de solicitudes de cambio, así que la configuración de cada repositorio variará y algunas tendrán más de una verificación. La verificación que contiene los resultados del escaneo de código se llama: Resultados del escaneo de código.
Si el repositorio utiliza el Flujo de trabajo de análisis de CodeQL, se ejecutará una verificación de CodeQL / Analyze (LANGUAGE) para cada lenguaje antes de que la verificación de resultados se ejecute. La verificación del análisis podría fallar si existieran problemas de configuración o si la solicitud de cambios impide la compilación para un lenguaje que el análisis necesita compilar (por ejemplo, C/C++, C# o Java). Así como con otras verificaciones de solicitudes de cambios, puedes ver todos los detalles de la falla de la verificación en la pestaña de Verificaciones. Para obtener más información acerca de la configuración y la soución de problemas, consulta la sección "Configurar el escaneo de código" o "Solucionar problemas del flujo de trabajo de CodeQL".
Clasificar una alerta en tu solicitud de cambios
Cuando ves la pestaña de Archivos que cambiaron en una solicitud de cambios, puedes ver anotaciones de cualquier línea de código que haya activado la alerta.
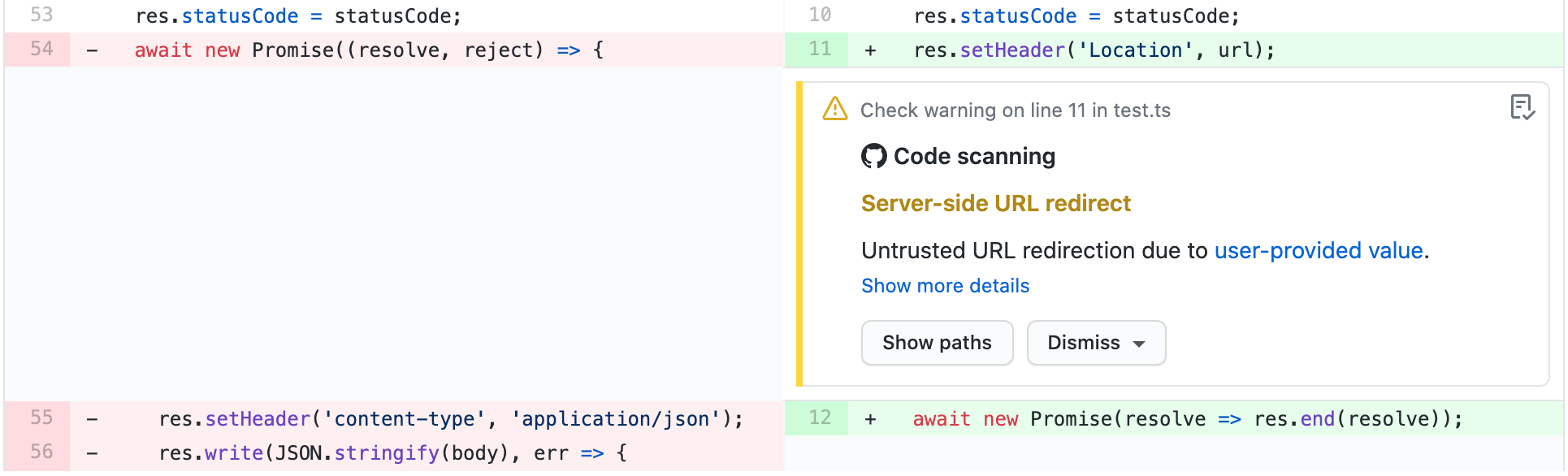
Si tienes permisos de escritura para el repositorio, algunas anotaciones contendrán enlaces con un contexto adicional de la alerta. En el ejemplo anterior del análisis de CodeQL, puedes dar clic en valor proporcionado por el usuario para ver en dónde ingresarían los datos no confiables dentro del flujo de datos (a esto se le conoce como la fuente). En este caso, también puedes ver la ruta completa desde la fuente hasta el código que utiliza los datos (el consumidor de datos) dando clic en Mostrar rutas. Esto facilita la revisión, ya sea que los datos no sean confiables o que el análisis falle en reconocer un paso de sanitización de datos entre la fuente y el consumidor de datos. Para obtener información sobre cómo analizar el flujo de datos utilizando CodeQL, consulta la sección "Acerca del análisis de flujo de datos".
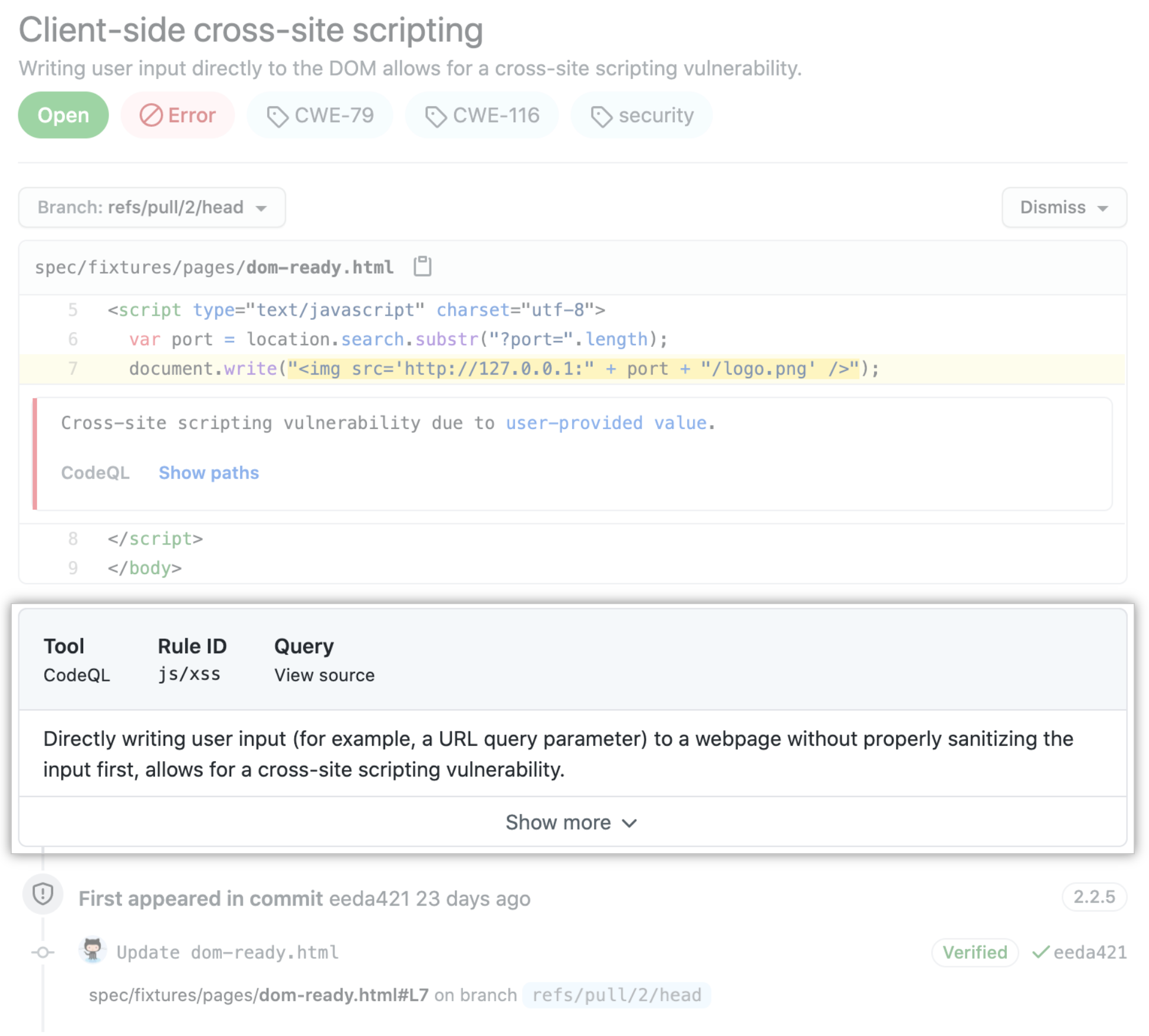
Para ver más información sobre una alerta, los usuarios con permisos de escritura pueden dar clic en el enlace de Mostrar más detalles que se muestra en la anotación. Esto te permite ver todo el contexto y los metadatos que proporciona la herramienta en una vista de alertas. En el siguiente ejemplo, puedes ver que las etiquetas muestran la severidad, tipo y las enumeraciones de los puntos débiles comunes (los CWE) del problema. La vista también muestra qué confirmación introdujo el problema.
En la vista detallada de una alerta, algunas herramientas del escaneo de código, como el análisis de CodeQL, también incluyen una descripción del problema y un enlace de Mostrar más para orientarte sobre cómo arreglar tu código.
Resolver una alerta en tu solicitud de extracción
Cualquiera con acceso de subida a una solicitud de cambios puede arreglar una alerta del escaneo de código, la cual se identifique en dicha solicitud. Si confirmas cambios en la solicitud de extracción, esto activará una ejecución nueva de las verificaciones de dicha solicitud. Si tus cambios arreglan el problema, la alerta se cierra y la anotación se elimina.
Si no crees que alguna alerta deba arreglarse, los usuarios con permisos de escritura pueden cerrarla manualmente. Por ejemplo, un error en el código que se utiliza únicamente para hacer pruebas, o cuando el esfuerzo de areglar el error es mayor que el beneficio potencial de mejorar el código. El botón de Cerrar se encuentra disponible en las anotaciones y en la vista de alertas si tienes permisos de escritura en el repositorio.
Si cierras una alerta de CodeQL como un resultado falso positivo, por ejemplo, porque el código utiliza una biblioteca de sanitización que no es compatible, considera colaborar con el repositorio de CodeQL y mejorar el análisis. Para obtener más información acerca de CodeQL, consulta la sección "Contribuir con CodeQL".